Hi guys !
I'm trying to use OpenWRT on a WRT54GL to act as a VPN end-point, using NordVPN commercial service to encrypt all traffic between my LAN and the internet, and increase my privacy when browsing the Internet.
I found many guides online, I read all I could find on the subject from the official documentation, but I keep running on the same issue again and again.
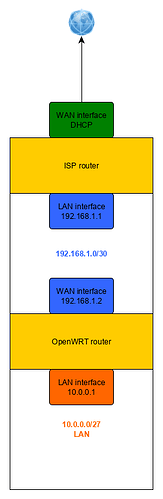
Here's an overview of my current setup:
Setting up the tunnel works fine. I'm able to ping any Internet destination from the Tun interface.
However, when the tunnel is active, I'm unable to get out of the LAN through it.
The following command works:
ping 1.1.1.1
It's using the tunnel interface IP as source.
However, the following command fails:
ping -I 10.0.0.1 1.1.1.1
With the tunnel active, the routing table looks like this:
root@OpenWrt:~# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
REDACTED 192.168.1.1 255.255.255.255 UGH 0 0 0 eth0.1
192.168.1.0 0.0.0.0 255.255.255.240 U 0 0 0 eth0.1
10.0.0.0 0.0.0.0 255.255.255.224 U 0 0 0 br-lan
10.8.8.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
0.0.0.0 10.8.8.1 128.0.0.0 UG 0 0 0 tun0
128.0.0.0 10.8.8.1 128.0.0.0 UG 0 0 0 tun0
0.0.0.0 192.168.1.1 0.0.0.0 UG 0 0 0 eth0.1
To the best of my understanding, this should be fine. I have taken no steps to customize it.
Since the bare "ping 1.1.1.1" works (using the tunnel interface IP address as a source), I'm assuming that my ISP modem/router isn't interfering and that the NAT is working as expected.
The most obvious possible culprit, to my limited understanding, would be the firewall. To make things simple, I added the tunnel interface to the WAN zone (as recommended in the OpenWRT documentation).
I've also tried setting everything temporarily to "ACCEPT" for debugging purpose, but it did not help.
I do not know how to debug packet filtering/routing in real-time, which would help.
The OpenVPN configuration file looks like this:
client
dev tun
proto udp
remote REDACTED
resolv-retry infinite
remote-random
nobind
tun-mtu 1500
tun-mtu-extra 32
mssfix 1450
persist-key
persist-tun
ping 15
ping-restart 0
ping-timer-rem
reneg-sec 0
comp-lzo no
ca /etc/openvpn/ca.cert
tls-auth /etc/openvpn/ta.key 1
redirect-gateway def1
remote-cert-tls server
auth-user-pass /etc/openvpn/secret
verb 3
pull
fast-io
cipher AES-256-CBC
auth SHA512
key-direction 1
And the /etc/openvpn file pointing to it:
config 'openvpn' 'nordvpn'
option 'config' '/etc/openvpn/custom.ovpn'
Here's the firewall setup:
config 'defaults'
option 'syn_flood' '1'
option 'input' 'ACCEPT'
option 'output' 'ACCEPT'
option 'drop_invalid' '1'
option 'forward' 'DROP'
config 'zone'
option 'name' 'lan'
option 'network' 'lan'
option 'input' 'ACCEPT'
option 'output' 'ACCEPT'
option 'forward' 'ACCEPT'
config 'zone'
option 'name' 'wan'
option 'output' 'ACCEPT'
option 'network' 'openvpn wan'
option 'masq' '1'
option 'mtu_fix' '1'
option 'input' 'DROP'
option 'forward' 'DROP'
config 'include'
option 'path' '/etc/firewall.user'
config 'forwarding'
option 'dest' 'wan'
option 'src' 'lan'
The network config:
config 'switch' 'eth0'
option 'enable' '1'
config 'switch_vlan' 'eth0_0'
option 'device' 'eth0'
option 'vlan' '0'
option 'ports' '0 1 2 3 5'
config 'switch_vlan' 'eth0_1'
option 'device' 'eth0'
option 'vlan' '1'
option 'ports' '4 5'
config 'interface' 'loopback'
option 'ifname' 'lo'
option 'proto' 'static'
option 'ipaddr' '127.0.0.1'
option 'netmask' '255.0.0.0'
config 'interface' 'lan'
option 'type' 'bridge'
option 'ifname' 'eth0.0'
option 'proto' 'static'
option 'dns' '1.1.1.1'
option 'ipaddr' '10.0.0.1'
option 'netmask' '255.255.255.224'
option 'gateway' '192.168.1.1'
config 'interface' 'wan'
option 'ifname' 'eth0.1'
option '_orig_ifname' 'eth0.1'
option '_orig_bridge' 'false'
option 'proto' 'static'
option 'netmask' '255.255.255.240'
option 'ipaddr' '192.168.1.2'
option 'gateway' '192.168.1.1'
option 'peerdns' '0'
list 'dns' '1.1.1.1'
list 'dns' REDACTED
list 'dns' REDACTED
option 'metric' '0'
config 'interface' 'openvpn'
option 'proto' 'none'
option 'ifname' 'tun1'
option 'auto' '1'
Note: I'm using 1.1.1.1 as a DNS server for the time being for debugging reasons.
Would anyone have an idea what I have missed? Any help would be greatly appreciated!
(edit: routing table formatting)