Hello Community,
I want to apologize in advance for this monsterious post. If it is catergorized incorrectly or posted in the wrong forum, please let me know rather than down-voting me and I will follow the proper protocol and procedures.
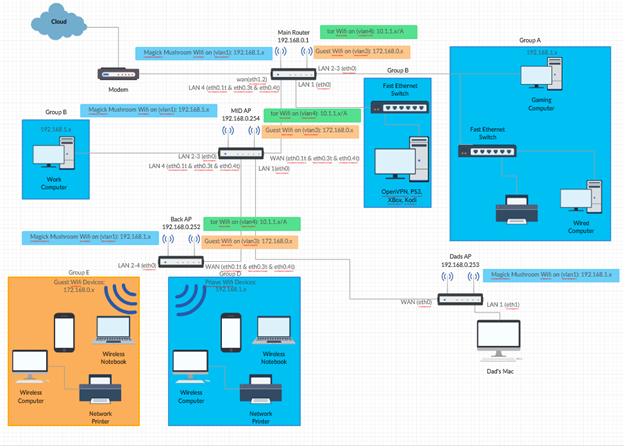
Before we begin, here is my network topology:
I have been trying to configure my Linksys WRT 3200ACM router to serve as my OpenVPN server so I can free up one of my Raspberry Pis. I noticed that the OpenVPN (Server Setup) and the OpenVPN Server (Comprehensive) wiki are no longer available so I followed along with the OpenVPN Basic wiki tutorial.
The tutorial has me follow three scripts (if this is an old post that I am not supposed to follow please let me know).
I am able to run the first script, create-certs.sh, fine without any problems I can detect.
However, there were some complications when running 2 and 3. When I run the 2nd script, create-configs.sh and reload the network/firewall or reboot the router, the router is inaccessible, not able to be pinged, loss of internet connectivity, and dhcp service does not distribute IP address.
The issues I have with the 3rd script, create-ovpn.sh, I notice that some configurations are missing in the *.ovpn file i.e. it will not list the dev, port number next to the ddns address, and there could be more I am not aware of.
Of course, my network is not standard in the way these scripts are meant to be performed on. So I had to, unfortunately, modify them to meet my use-case. I have three networks, each on their own respective vlan. I am starting with creating a vpn connection to my private lan interface. If that works, I would like to eventually edit the scripts to create the configs necessary to create remote-accessible vpn connections to connect to the other networks.
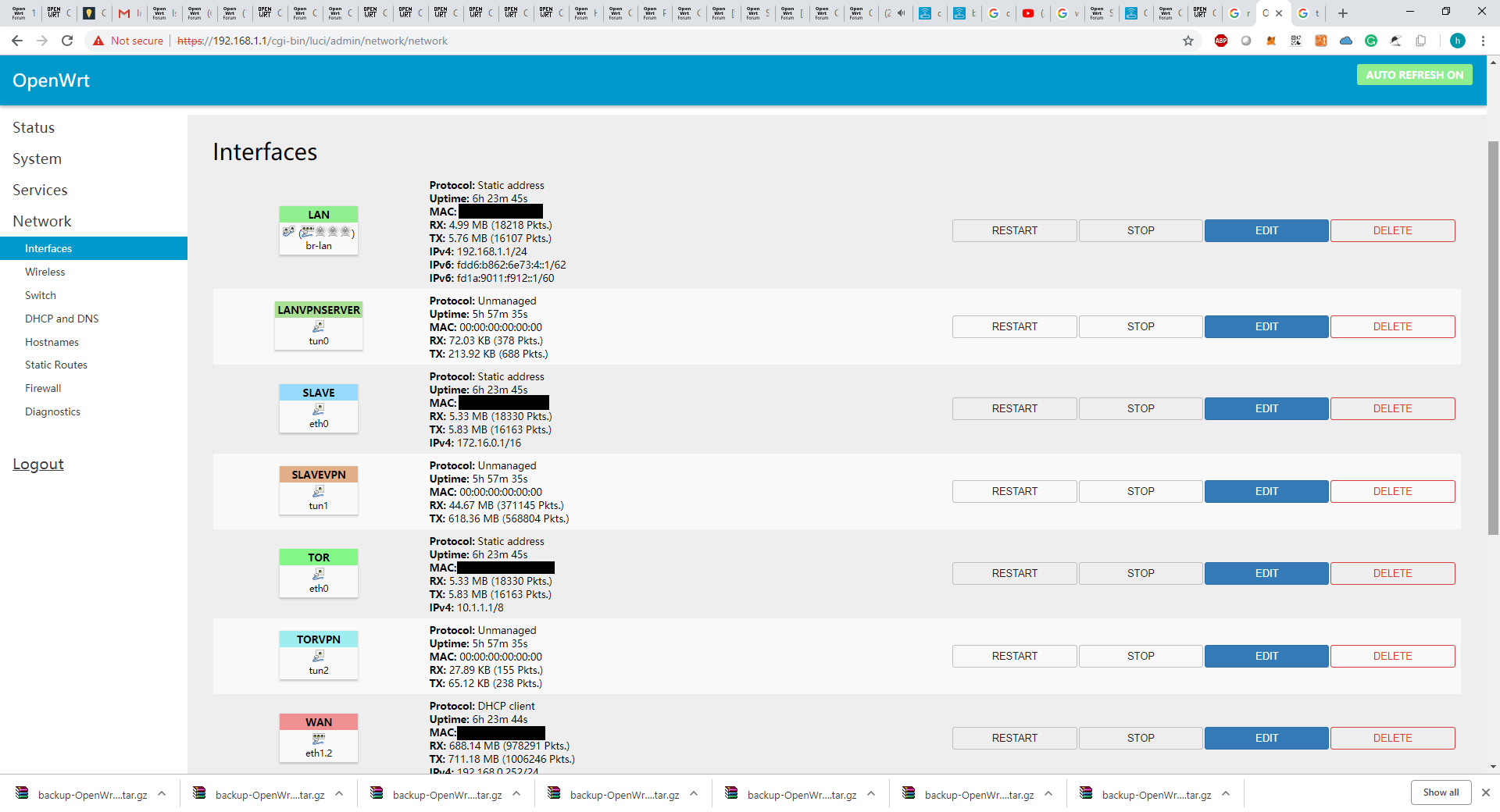
My current interfaces/networks are:
- lan = my private network
- slave = guest network
- tor = my tor network
The minor changes I made to the scripts was naming the vpnserver as their respective network they would connect to and the IP addresses/subnet they would be members of i.e. lan_vpnserver, 192.168.0.0/C, etc.
I tried breaking down the 2nd script and running the uci set commands individually, restarting the router after every input to try and isolate the root cause. It looks like the network and firewall redirect configs may be the culprit in causing my router to go offline.
My edited scripts are listed below (I have made comments on the areas I have changed):
Note: I have tried running the 2 script without changing vpnserver to lan_vpnserver and I still experience the same issue
01.create-certs.lan.sh
#!/bin/sh
# Installing packages
opkg update
opkg install openssl-util openvpn-openssl
# Creating Directory Structure
VPN_DIR="/etc/openvpn/lan" #added dir lan for orginizational purposes
PKI_DIR="$VPN_DIR/ssl"
if [ -d "$PKI_DIR" ]
then
rm -rf "$PKI_DIR"
fi
mkdir -p "$PKI_DIR"
chmod -R 600 "$PKI_DIR"
cd "$PKI_DIR"
touch index.txt index
echo 1000 > serial
cp -f /etc/ssl/openssl.cnf "$PKI_DIR"
# Customizing openssl.cnf
PKI_CONF="$PKI_DIR/openssl.cnf"
sed -i "
s:\\\\:/:g
/^dir/ s:=.*:= $PKI_DIR:
/^new_certs_dir/ s:=.*:= $PKI_DIR:
/.*Name/ s:= match:= optional:
/organizationName_default/ s:= .*:= OG.Infraverse:
/stateOrProvinceName_default/ s:= .*:= Yorkshire:
/countryName_default/ s:= .*:= UK:
/default_days/ s:=.*:= 3650:
/default_bits/ s:=.*:= 4096:
" "$PKI_CONF"
cat << "EOF" >> "$PKI_CONF"
[ lan_vpnserver ]
keyUsage = digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
[ lan_vpnclient ]
keyUsage = digitalSignature
extendedKeyUsage = clientAuth
EOF
# Generating Server PSK and CA, Server, & Client Certs
# Generating Certifcate Authority Cert & Key
openssl req -batch -nodes -new -keyout "ca.key" -out "ca.crt" -x509 -config "$PKI_CONF" -days "3650"
#changed vpnserver/vpnclient to lan_vpnserver/lan_client
# Generating Server Cert & Key
openssl req -batch -nodes -new -keyout "lan_vpnserver.key" -out "lan_vpnserver.csr" -subj "/CN=lan_vpnserver" -config "$PKI_CONF"
# Signing Server Cert
openssl ca -batch -keyfile "ca.key" -cert "ca.crt" -in "lan_vpnserver.csr" -out "lan_vpnserver.crt" -config "$PKI_CONF" -extensions "lan_vpnserver"
# Generating Client Cert & Key
# PASSPHRASE MUST BE SET (4 chars minimum, 16+ chars recommended)
openssl req -batch -new -keyout "lan_vpnclient.key" -out "lan_vpnclient.csr" -subj "/CN=lan_vpnclient" -config "$PKI_CONF"
# Signing Client Cert
openssl ca -batch -keyfile "ca.key" -cert "ca.crt" -in "lan_vpnclient.csr" -out "lan_vpnclient.crt" -config "$PKI_CONF" -extensions "lan_vpnclient"
# Generating OpenVPN TLS PSK
openvpn --genkey --secret "tc.pem"
# Generating Diffie-Hellman Cert
# May take a while to complete (~25m on WRT3200ACM)
openssl dhparam -out "dh.pem" 2048
# Correcting Permissions
chmod 600 tc.pem dh.pem ca.key lan_vpnserver.key lan_vpnclient.key
# Copying Certs & Keys to $VPN_DIR
cp tc.pem dh.pem ca.crt lan_vpnserver.* lan_vpnclient.* "$VPN_DIR"
# Returning to initial working directory
cd -
# Done
02.create-configs.lan.sh
#!/bin/sh
# Installing packages
opkg update
opkg install openvpn-openssl luci-app-openvpn
# Configuring network
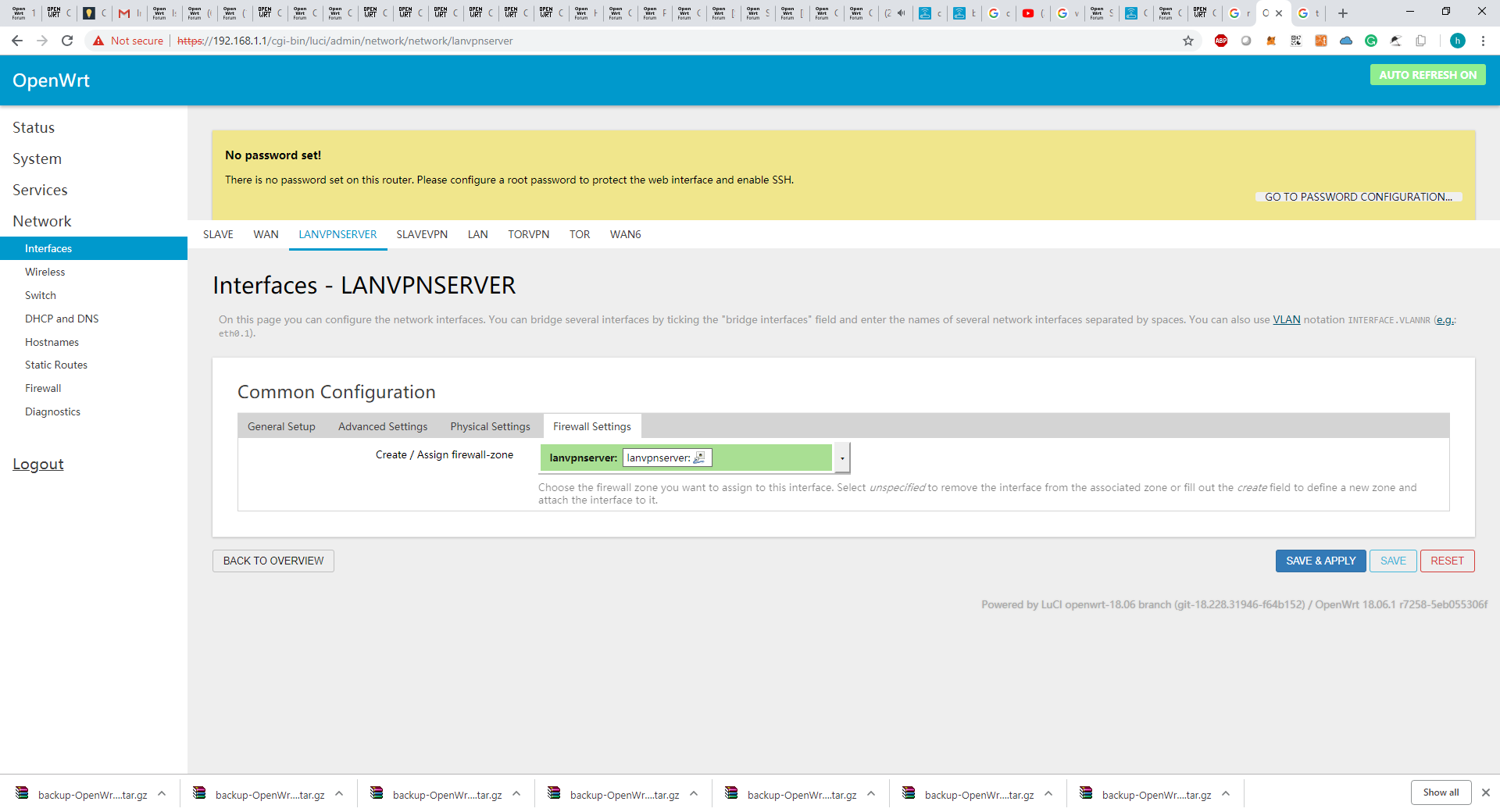
uci set network.lan_vpnserver="interface"
uci set network.lan_vpnserver.ifname="tun0"
uci set network.lan_vpnserver.proto="none"
uci commit network
# Configuring firewall
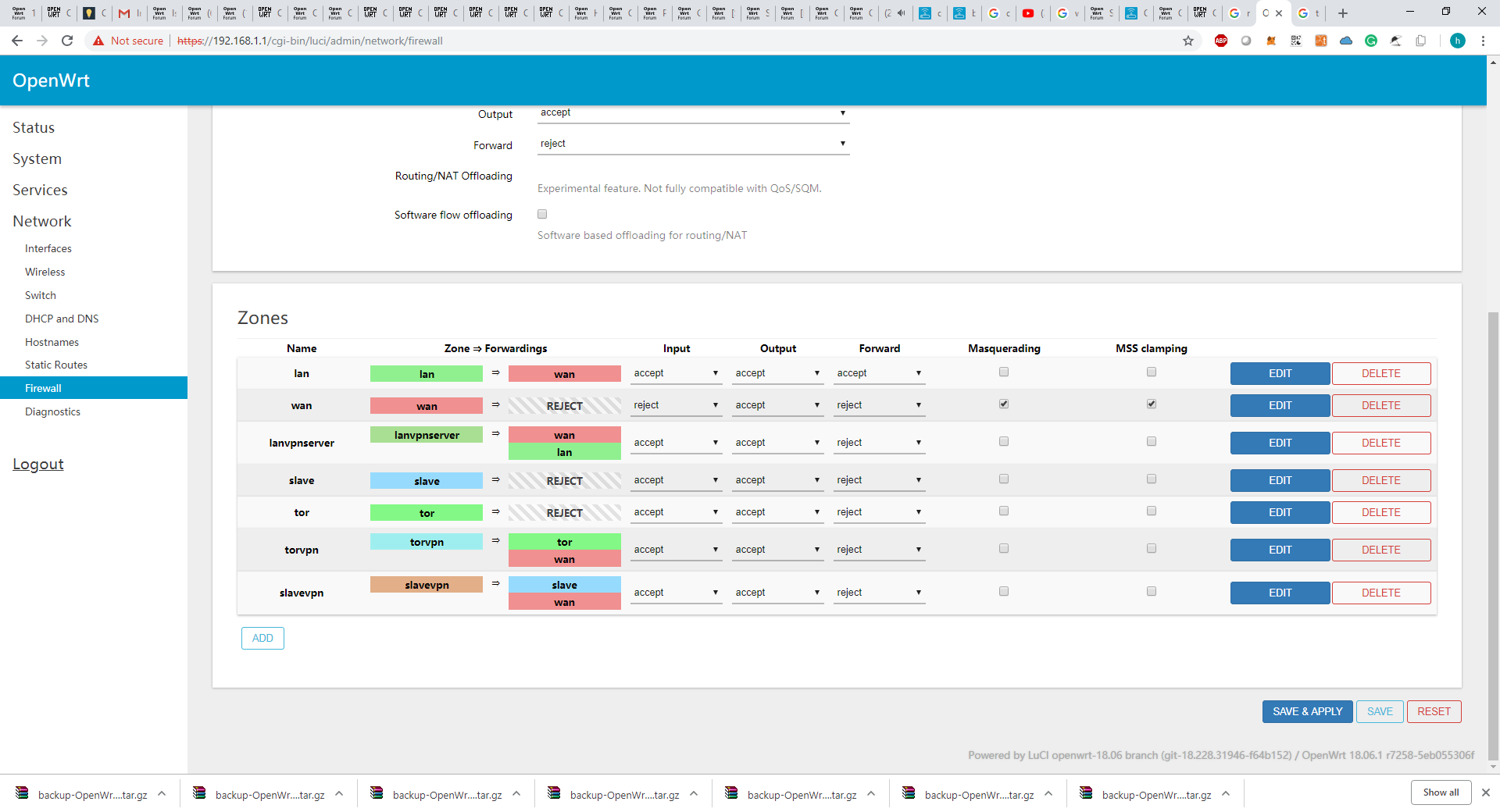
uci add firewall rule
uci set firewall.@rule[-1].name="Allow-LAN-OpenVPN"
uci set firewall.@rule[-1].src="wan"
uci set firewall.@rule[-1].dest_port="1999" #custom port for the vpn
uci set firewall.@rule[-1].proto="tcp udp"
uci set firewall.@rule[-1].target="ACCEPT"
uci add firewall zone
uci set firewall.@zone[-1].name="lan_vpnserver"
uci add_list firewall.@zone[-1].network="lan_vpnserver"
uci set firewall.@zone[-1].input="ACCEPT"
uci set firewall.@zone[-1].output="ACCEPT"
uci set firewall.@zone[-1].forward="REJECT"
uci add firewall forwarding
uci set firewall.@forwarding[-1].src="lan_vpnserver"
uci set firewall.@forwarding[-1].dest="wan"
uci add firewall forwarding
uci set firewall.@forwarding[-1].src="lan_vpnserver"
uci set firewall.@forwarding[-1].dest="lan"
uci commit firewall
# Configuring OpenVPN Server
VPN_DIR="/etc/openvpn/lan" #added dir lan for orginizational purposes
uci set openvpn.lan_vpnserver="openvpn"
uci set openvpn.lan_vpnserver.enabled="1"
uci set openvpn.lan_vpnserver.verb="3"
uci set openvpn.lan_vpnserver.dev="tun0"
uci set openvpn.lan_vpnserver.topology="subnet"
uci set openvpn.lan_vpnserver.port="1999"
uci set openvpn.lan_vpnserver.proto="udp"
uci set openvpn.lan_vpnserver.server="192.168.200.0 255.255.255.0"
uci set openvpn.lan_vpnserver.client_to_client="1"
uci set openvpn.lan_vpnserver.compress="lzo"
uci set openvpn.lan_vpnserver.keepalive="10 120"
uci set openvpn.lan_vpnserver.persist_tun="1"
uci set openvpn.lan_vpnserver.persist_key="1"
uci set openvpn.lan_vpnserver.dh="$VPN_DIR/dh.pem"
uci set openvpn.lan_vpnserver.tls_crypt="$VPN_DIR/tc.pem"
uci set openvpn.lan_vpnserver.ca="$VPN_DIR/ca.crt"
uci set openvpn.lan_vpnserver.cert="$VPN_DIR/lan_vpnserver.crt"
uci set openvpn.lan_vpnserver.key="$VPN_DIR/lan_vpnserver.key"
uci add_list openvpn.lan_vpnserver.push="redirect-gateway def1"
uci add_list openvpn.lan_vpnserver.push="route 192.168.0.0 255.255.255.0"
uci add_list openvpn.lan_vpnserver.push="dhcp-option DNS 192.168.0.1"
uci add_list openvpn.lan_vpnserver.push="compress lzo"
uci add_list openvpn.lan_vpnserver.push="persist-tun"
uci add_list openvpn.lan_vpnserver.push="persist-key"
VPN_DOMAIN="$(uci -q get dhcp.@dnsmasq[0].domain)"
if [ -n "$VPN_DOMAIN" ]
then
uci add_list openvpn.lan_vpnserver.push="dhcp-option DOMAIN $VPN_DOMAIN"
fi
uci commit openvpn
# Restarting services
service network restart
sleep 5
service firewall restart
sleep 5
service openvpn restart
# Done
03.create-ovpn.lan.sh
#!/bin/sh
# Obtaining server address from WAN-interface IP
source /lib/functions/network.sh
network_find_wan WAN_IF
network_get_ipaddr SERVER_ADDR "$WAN_IF"
# Obtaining server address from DDNS client service
SERVER_FQDN="$(uci -q get $(uci -q show ddns \
| sed -n -e "s/^\(.*\)\.enabled='1'$/\1/p" \
| head -n 1).lookup_host)"
if [ -n "$SERVER_FQDN" ]
then
SERVER_ADDR="$SERVER_FQDN"
fi
# Setting configuration parameters
SERVER_PORT="$(uci get openvpn.lan_vpnclient.port)" #changed vpnclient => lan_vpnclient
SERVER_PROTO="$(uci get openvpn.lan_vpnclient.proto)" #changed vpnclient => lan_vpnclient
CLIENT_DEV="$(uci get openvpn.lan_vpnclient.dev | sed -e "s/\d*$//")" #changed vpnclient => lan_vpnclient
CLIENT_COMPR="$(uci get openvpn.lan_vpnclient.compress)" #changed vpnclient => lan_vpnclient
VPN_DIR="/etc/openvpn/lan" #added dir lan for orginizational purposes
TC_KEY="$(sed -e "/^#/d;/^\w/N;s/\n//" "$VPN_DIR/tc.pem")"
CA_CERT="$(openssl x509 -in "$VPN_DIR/ca.crt")"
# Generating .ovpn-files
grep -l -e "TLS Web Client Authentication" "$VPN_DIR"/*.crt \
| sed -e "s/^.*\///;s/\.[^.]*$//" \
| while read CLIENT_ID
do
CLIENT_CERT="$(openssl x509 -in "$VPN_DIR/$CLIENT_ID.crt")"
CLIENT_KEY="$(cat "$VPN_DIR/$CLIENT_ID.key")"
CLIENT_CONF="$VPN_DIR/$CLIENT_ID.ovpn"
cat << EOF > "$CLIENT_CONF"
verb 3
nobind
dev $CLIENT_DEV
client
remote $SERVER_ADDR $SERVER_PORT $SERVER_PROTO
fast-io
compress $CLIENT_COMPR
auth-nocache
remote-cert-tls server
<tls-crypt>
$TC_KEY
</tls-crypt>
<ca>
$CA_CERT
</ca>
<cert>
$CLIENT_CERT
</cert>
<key>
$CLIENT_KEY
</key>
EOF
done
# Setting permissions
chmod 600 "$VPN_DIR"/*.ovpn
# Showing generated .ovpn-files
head -v -n -0 "$VPN_DIR"/*.ovpn
# Done
Output of 3rd script
verb 3
nobind
dev #the device is missing, i think this would need to match the config on the server/script which would be "tun"
client
remote my.domainname.com 1999
fast-io
compress
auth-nocache
remote-cert-tls server
<tls-crypt>
-----BEGIN OpenVPN Static key V1-----
d37...ef1a
-----END OpenVPN Static key V1-----
</tls-crypt>
<ca>
-----BEGIN CERTIFICATE-----
MII...qKP
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
MII...eYH
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN ENCRYPTED PRIVATE KEY-----
MII...M8=
-----END ENCRYPTED PRIVATE KEY-----
</key>
Current Configs before running the script.
Network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdfb:7e04:aca7::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.0.1'
option gateway '192.168.0.1'
option broadcast '192.168.0.255'
option dns '8.8.8.8'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
option hostname 'infraverse.network'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
option vid '2'
config interface 'slave'
option type 'bridge'
option proto 'static'
option ipaddr '172.16.0.1'
option netmask '255.255.0.0'
option ifname 'eth0.3 radio1'
option gateway '172.16.0.1'
option broadcast '172.16.255.255'
config interface 'tor'
option proto 'static'
option ipaddr '10.1.1.1'
option netmask '255.0.0.0'
option type 'bridge'
option ifname 'eth0.4'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '3'
option ports '0t 5t'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '4'
option ports '0t 5t'
dhcp:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option serversfile '/tmp/adb_list.overall'
list server '8.8.8.8'
list server '8.8.4.4'
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option start '2'
option limit '254'
option ra_management '1'
config dhcp 'slave'
option leasetime '12h'
option interface 'slave'
option start '2'
option limit '254'
config dhcp 'tor'
option leasetime '12h'
option interface 'tor'
option start '2'
option limit '254'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
Firewall:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config zone
option name 'slave'
option forward 'REJECT'
option output 'ACCEPT'
option network 'slave'
option input 'REJECT'
config forwarding
option dest 'wan'
option src 'slave'
config rule
option target 'ACCEPT'
option proto 'tcp udp'
option dest_port '53'
option name 'Slave dns'
option src 'slave'
config rule
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
option name 'slave dhcp'
option src 'slave'
config zone
option name 'tor'
option forward 'REJECT'
option output 'ACCEPT'
option network 'tor'
option input 'ACCEPT'
option syn_flood '1'
option conntrack '1'
config forwarding
option dest 'wan'
option src 'tor'
config forwarding
option src 'wan'
option dest 'tor'
config rule
option src 'tor'
option proto 'udp'
option dest_port '67'
option target 'ACCEPT'
config rule
option src 'tor'
option proto 'tcp'
option dest_port '9040'
option target 'ACCEPT'
config rule
option src 'tor'
option proto 'udp'
option dest_port '9053'
option target 'ACCEPT'
config redirect
option name 'Redirect-Tor-Traffic'
option src 'tor'
option src_dip '!10.1.1.1'
option dest_port '9040'
option proto 'tcp'
option target 'DNAT'
config redirect
option name 'Redirect-Tor-DNS'
option src 'tor'
option src_dport '53'
option dest_port '9053'
option proto 'udp'
option target 'DNAT'
I am not able to grab the logs after I run the 2nd and 3rd scripts. After I run the scripts, it renders my router offline since the second script reloads/restarts firewall and network which prohibits me from connecting to it to extract the logs.
If you need the configs of what it looks like after I run the scripts, let me know. I will re-run it on the router again with the reload/restart commented to grab them. I do not have it on me since I had to blow away my router and reload its backup.
I did notice after individually running each uci set command for the network section in the 2nd script and rebooting the router is what causes the issue. I notice the VPN interface has only two lines and it appends to the config file and adds it to the bottom underneath the vlan/switch config. Would this conflict if it puts it at the bottom of the vlan/switch config? would the vlan/switch config need to be the last lines of the network config file?
Are these scripts still applicable to OpenWrt 18?
I wouldn't be surprised if the minor changes I made to the script is causing these issues. I know running the scripts in the original form is best practice but if the original script works, how would I correctly create other vpns to connect with the other vlans/network interfaces? can the scripts be repurposed and reused in that case?
Thank you for your patience in allowing me to describe my predicament in detail. Any help would greatly be appreciated.
Sincerely,
A humbely committed student