Hi Brains Trust, I have a question that has had me stumped for a few days now. I'd appreciate someone helping me out as I can't find anything on the forums about this and am by no means a network expert.
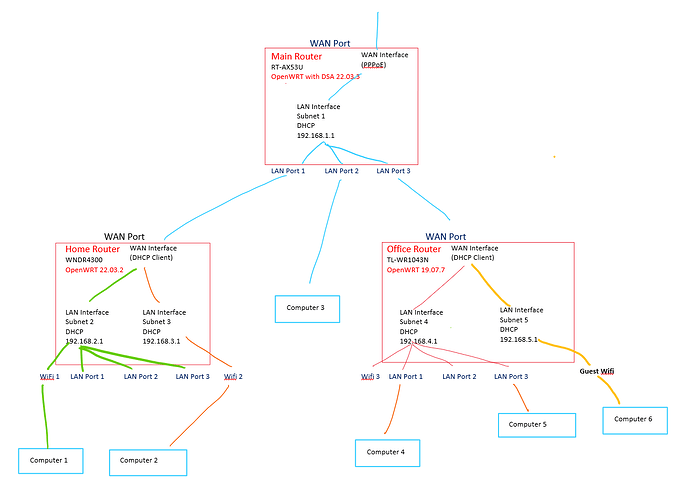
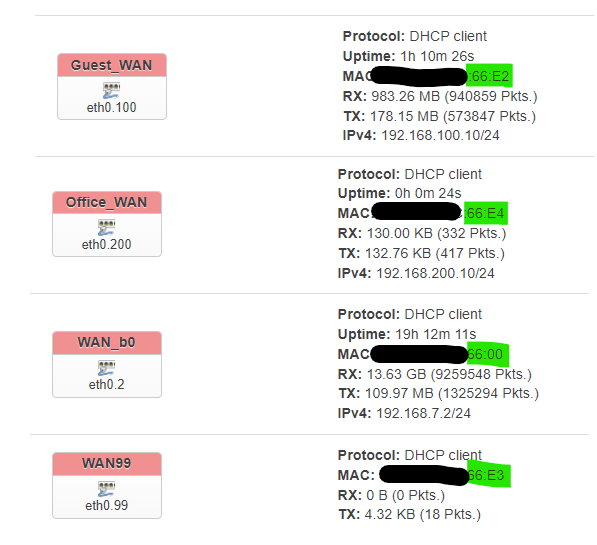
I have 3 devices running OpenWrt. One is my main router in the garage, the second is located in a home office, and the third is in the house. Details are in the image, but happy to go into more detail if needed. Currently all LAN ports on all devices are bridged.
I'm trying to set up a guest wifi in the office that allows internet access but not access to the LAN. It was simple enough to create "LAN Interface Subnet 5" in a different firewall Zone, connect a guest Wifi and use firewall rules to only allow access to the WAN. I do this on my home router so I can limit devices on WiFi 2 from accessing the WAN between certain hours.
Obviously this still allows access from the Guest wifi to every device on Subnet 1, so I believe I need a second WAN on the Office Router and handle this, with firewall rules on the main Router. I only have one ethernet cable between the Main Router and office Router.
I have tried to achieve this by creating a second WAN interface on the Office Router and creating a second LAN interface on the main router, but I'm not having much luck. I even tried having the Virtual WAN interface get a second IP address from Subnet 1's DHCP by spoofing the MAC, but this seems to only cause a LAN storm... I even tried to remove LAN port 3 from the bridge on the Main router, but not only did this not work either, it wouldn't be a suitable long-term solution as devices on Subnet 4 need to be able to access devices on Subnet 1.
Is it even possible to achieve this, and if so, how? I even tried macvlan but am completely out of my depth there!
Any help would be greatly appreciated.
You need to use VLANs, and trunk them on the wire that connects the routers. There are several posts in this forum, about similar scenarios.
1 Like
Thanks @eduperez, I'll keep persisting now that I know it's possible, but I'm 2 days in and still not looking any closer to a solution...
I've just updated my office router to 22.03.5, I'll see if I have any luck with that.
The preferred solution is to make the main router in charge of all of the routing and firewall functions, and then have the other devices simply as VLAN aware dumb APs. This will make administration much easier, and will give you flexibility to have any or all of the networks available (if desired) in each of the spaces.
1 Like
Probably right @psherman, but there are reasons for sticking with the current set up.
I've been researching VLANS all day, but I'm still stuck.
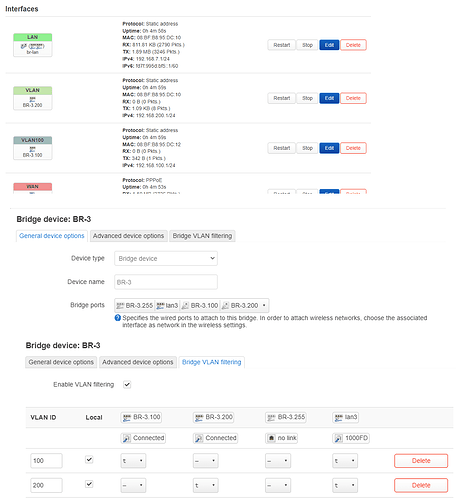
I've set up 2 VLANS on the main router, the only way I knew how was to bridge VLANS on the physical port 3.
I removed physical port 3 from the LAN bridge, and I can ping the corresponding IP addresses from my office router (although if I have set this up correctly I would have though this shouldn't have been possible...)
What I cant seem to do is make virtual WAN ports on the office router to connect to the DHCP servers on the VLAN. It seems I can only connect from the untagged WAN port...
Any help would be appreciated but I'll keep digging and if I manage to make this work I'll post the solution for any other newbies like me trying to do the same thing.
How are the APs configured now?
would you mind sharing these reasons? I'm not asking this sarcastically, but rather I'd like to understand why you feel this current general config is optimal, and maybe I can convince you otherwise if I disagree but have your perspective in mind.
the problem here is likely that you aren't yet familiar with DSA syntax (at least for the device that generated the screenshots). It's a bit confusing at first, but it does make sense once you get the hang of it.
It seems like there are probably errors in the config... but I'd like to get more info about your desire to keep the general topology/config first in order to best advise.
1 Like
Thanks for your help everyone, with your pointers I managed to find the right info to get it working how I wanted. It wasn't anywhere near as difficult as I had made it out to be, but because only some of my devices have DSA it did confuse me for a while...
I'll catch up on some work and over the weekend I'll post my solution for anyone else having the same problem.
@psherman, the reason for wanting to have multiple routers is really for segmentation and ease of management. I move offices frequently, so by managing the family devices from the home router and the office devices from the office router I can just move one router and everything is (mostly) set up.
So you're saying that you literally take the router itself from location to location? And that is sometimes at home, while other times is out of the home?
Yes. It's a bit weird but I take a bunch of network-connected hardware with me for work, and this allows me have them configured how I want regardless of where I am.
In any case, your approach seems much better now I've got the VLAN working, and it would allow Wi-Fi Roaming, so I'll probably rethink how I do all this when I get a chance.
For anyone in the future wanting to do this, here is what I did.
1. Create VLANs on the ethernet bridge device on the DSA main router:
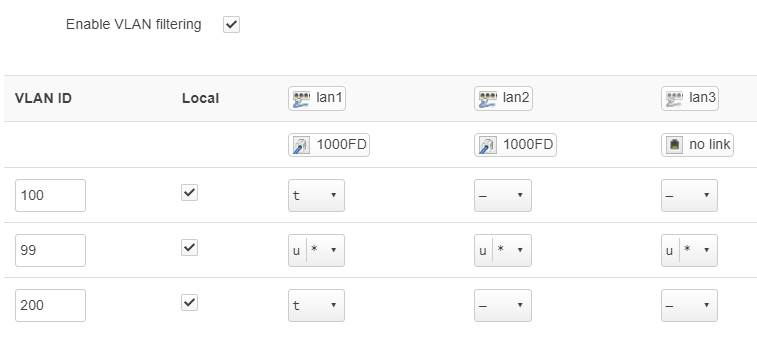
I connect the office router through an unmanaged switch with a few other devices, so I set the primary VLAN (99) to "unmanaged" on my lan1 port and set it to primary.
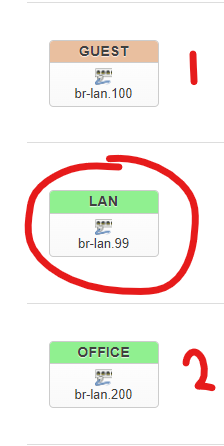
2. Change the LAN bridge on the main router to use the primary VLAN. Create 2 additional interfaces using each of the newly-created VLAN IDs, then save and apply:
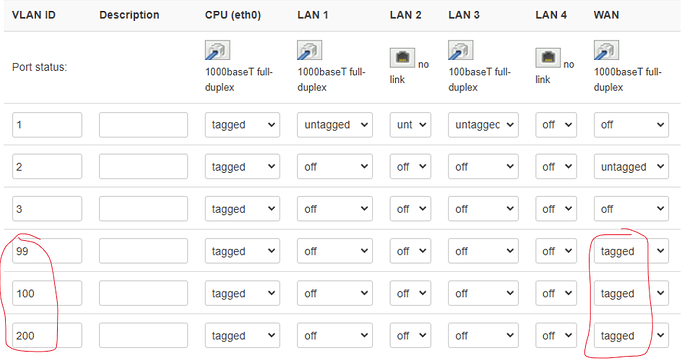
3. on the Non-DSA office router, create 3 additional VLANS under "Network", "Switch" for the WAN port:
4. I set a different MAC on each device (not sure this is strictly nescessary) and created 3 more WAN interfaces. Each connected over the VLAN no worries.
Note that if you set the primary VLAN (99) to "unmanaged" in step 1 then you'll connect over the untagged interface (eth0.2 in my case), if you set it to tagged you'll connect over the VLAN (eth0.99 in my case).
From there you configure your firewall zones accordingly.
Hope this helps another networking newbie sometime in the future!