br-guest Link encap:Ethernet
inet addr:192.168.3.1 Bcast:255.255.255.255 Mask:255.255.255.255
inet6 addr: fe80::360a:33ff:fe87:c62/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:924 errors:0 dropped:0 overruns:0 frame:0
TX packets:13 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:67692 (66.1 KiB) TX bytes:2334 (2.2 KiB)
br-lan Link encap:Ethernet
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fd53:ca99:74bd::1/60 Scope:Global
inet6 addr: fe80::360a:33ff:fe87:c61/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:639382 errors:0 dropped:0 overruns:0 frame:0
TX packets:702524 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:116528711 (111.1 MiB) TX bytes:757654321 (722.5 MiB)
eth0 Link encap:Ethernet
inet6 addr: fe80::360a:33ff:fe87:c61/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1504 Metric:1
RX packets:1110649 errors:0 dropped:0 overruns:0 frame:0
TX packets:862217 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:740550782 (706.2 MiB) TX bytes:390533091 (372.4 MiB)
Interrupt:21
lan1 Link encap:Ethernet
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:145588 errors:0 dropped:23 overruns:0 frame:0
TX packets:184381 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:25082771 (23.9 MiB) TX bytes:259418839 (247.4 MiB)
lan2 Link encap:Ethernet
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
lan3 Link encap:Ethernet
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
lan4 Link encap:Ethernet
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:35324 errors:0 dropped:0 overruns:0 frame:0
TX packets:35324 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2612222 (2.4 MiB) TX bytes:2612222 (2.4 MiB)
wan Link encap:Ethernet
inet addr:192.168.0.29 Bcast:192.168.0.255 Mask:255.255.255.0
inet6 addr: fe80::360a:33ff:fe87:c64/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:965061 errors:0 dropped:14338 overruns:0 frame:0
TX packets:579907 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:695476329 (663.2 MiB) TX bytes:116671175 (111.2 MiB)
wlan0 Link encap:Ethernet
inet6 addr: fe80::360a:33ff:fe87:c62/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:16409 errors:0 dropped:0 overruns:0 frame:0
TX packets:7122 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2821362 (2.6 MiB) TX bytes:1308870 (1.2 MiB)
wlan1 Link encap:Ethernet
inet6 addr: fe80::360a:33ff:fe87:c63/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:510920 errors:0 dropped:0 overruns:0 frame:0
TX packets:558243 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:99547349 (94.9 MiB) TX bytes:525310092 (500.9 MiB)
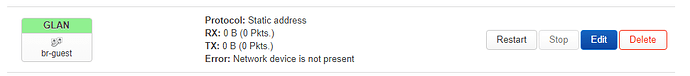
So br-guest is up and running.
Have you run the uci commit commands?
If you have not rebooted since then run those commands now.
openNDS should now be managing the br-guest network.
What happens when you connect a mobile device to Open-Guest SSID?
Hi @bluewavenet ,
Your questions are in bold
Have you run the uci commit commands?
If you have not rebooted since then run those commands now.
No, I've undo all and fresh installation,
I have rerun those commands as below
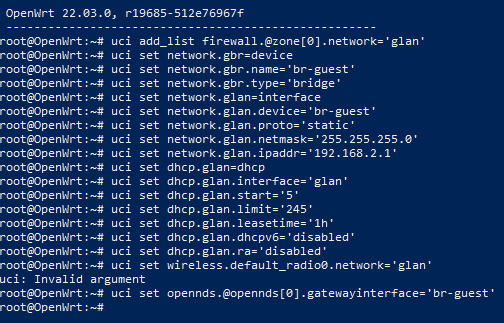
openNDS should now be managing the br-guest network.
Yes, its configured for option gatewayinterface 'br-guest'
What happens when you connect a mobile device to Open-Guest SSID?
if opennds is disabled, guest working fine with connected internet else
its not open anything.
Thanks.
I've undo all and fresh installation,
The list of commands was based on what you showed previously about your configs.
Your screenshot shows an error - uci: invalid argument
To be sure, show the configs as they are now:
If it is all working correctly, when openNDS is running, all Internet access should be blocked until you log in.
Almost all modern devices, (Android, Apple, Windows, Linux) should have an implementation of CPD (Captive Portal Detection) - unless it has been disabled.
You can read about CPD here:
https://opennds.readthedocs.io/en/stable/howitworks.html#captive-portal-detection-cpd
If you are connecting using your workstation and nothing happens then CPD is probably disabled.
Try reconnecting to the guest wifi then browsing to http://status.client
uci show wireless
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.path='1e140000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0'
wireless.radio0.channel='1'
wireless.radio0.band='2g'
wireless.radio0.htmode='HT20'
wireless.radio0.cell_density='0'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.path='1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
wireless.radio1.channel='36'
wireless.radio1.band='5g'
wireless.radio1.htmode='VHT80'
wireless.radio1.cell_density='0'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.network='lan'
wireless.default_radio1.mode='ap'
wireless.default_radio1.ssid='Jio5G-Test'
wireless.default_radio1.encryption='psk2'
wireless.default_radio1.key='P@$$w0rd@143'
wireless.guest=wifi-iface
wireless.guest.device='radio0'
wireless.guest.mode='ap'
wireless.guest.network='guest'
wireless.guest.encryption='none'
wireless.guest.ssid='Guest'
uci show network
network.loopback=interface
network.loopback.device='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.packet_steering='1'
network.globals.ula_prefix='fd53:ca99:74bd::/48'
network.@device[0]=device
network.@device[0].name='br-lan'
network.@device[0].type='bridge'
network.@device[0].ports='lan1' 'lan2' 'lan3' 'lan4'
network.lan=interface
network.lan.device='br-lan'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.wan=interface
network.wan.device='wan'
network.wan.proto='dhcp'
network.wan6=interface
network.wan6.device='wan'
network.wan6.proto='dhcpv6'
network.guest_dev=device
network.guest_dev.type='bridge'
network.guest_dev.name='br-guest'
network.guest=interface
network.guest.proto='static'
network.guest.device='br-guest'
network.guest.ipaddr='192.168.3.1'
network.gbr=device
network.gbr.name='br-guest'
network.gbr.type='bridge'
network.glan=interface
network.glan.device='br-guest'
network.glan.proto='static'
network.glan.netmask='255.255.255.0'
network.glan.ipaddr='192.168.2.1'
uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan' 'glan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.guest=zone
firewall.guest.name='guest'
firewall.guest.network='guest'
firewall.guest.input='REJECT'
firewall.guest.output='ACCEPT'
firewall.guest.forward='REJECT'
firewall.guest_wan=forwarding
firewall.guest_wan.src='guest'
firewall.guest_wan.dest='wan'
firewall.guest_dns=rule
firewall.guest_dns.name='Allow-DNS-Guest'
firewall.guest_dns.src='guest'
firewall.guest_dns.dest_port='53'
firewall.guest_dns.proto='tcp udp'
firewall.guest_dns.target='ACCEPT'
firewall.guest_dhcp=rule
firewall.guest_dhcp.name='Allow-DHCP-Guest'
firewall.guest_dhcp.src='guest'
firewall.guest_dhcp.src_port='68'
firewall.guest_dhcp.dest_port='67'
firewall.guest_dhcp.proto='udp'
firewall.guest_dhcp.family='ipv4'
firewall.guest_dhcp.target='ACCEPT'
firewall.opennds=include
firewall.opennds.type='script'
firewall.opennds.path='/usr/lib/opennds/restart.sh'
uci show opennds
opennds.@opennds[0]=opennds
opennds.@opennds[0].enabled='1'
opennds.@opennds[0].fwhook_enabled='1'
opennds.@opennds[0].gatewayinterface='br-guest'
opennds.@opennds[0].gatewayport='2050'
opennds.@opennds[0].gatewayname='OpenWiFi - Beta'
opennds.@opennds[0].maxclients='250'
opennds.@opennds[0].users_to_router='allow tcp port 53' 'allow udp port 53' 'allow udp port 67' 'allow tcp port 22' 'allow tcp port 80' 'allow tcp port 443'
You seem to be blindly following more than one set of instructions.
I gave you links to read as an aid to understanding, not to blindly follow.
I gave you commands to run and if you had learnt anything from reading the links, you would have some idea about what the requirements are and what the commands do.
Clearly you still have no understanding of any of this. Perhaps doing this is not really something you are interested in (my guess is it is a school project so you have to at least be seen to be making an effort).
Why have you decided to define a "guest" zone in the firewall? None of my instructions call for this.
Why have you defined a third bridge device (guest_dev)? This conflicts with the bridge device created by my commands.
Why have you defined a third ip subnet (192.168.3.x)?
Actually, as we discussed previously, i have applied Guest Wi-Fi basics, these settings coming when i applied it, now i have updated my settings according to your last three question, delete firewall on guest network, removed guest_dev and interface 192.168.3.x
Now output as below
uci show wireless
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.path='1e140000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0'
wireless.radio0.channel='1'
wireless.radio0.band='2g'
wireless.radio0.htmode='HT20'
wireless.radio0.cell_density='0'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.path='1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
wireless.radio1.channel='36'
wireless.radio1.band='5g'
wireless.radio1.htmode='VHT80'
wireless.radio1.cell_density='0'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.network='lan'
wireless.default_radio1.mode='ap'
wireless.default_radio1.ssid='Jio5G-Test'
wireless.default_radio1.encryption='psk2'
wireless.default_radio1.key='P@$$w0rd@143'
wireless.guest=wifi-iface
wireless.guest.device='radio0'
wireless.guest.mode='ap'
wireless.guest.network='guest'
wireless.guest.encryption='none'
wireless.guest.ssid='Guest'
uci show network
network.loopback=interface
network.loopback.device='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.packet_steering='1'
network.globals.ula_prefix='fd53:ca99:74bd::/48'
network.@device[0]=device
network.@device[0].name='br-lan'
network.@device[0].type='bridge'
network.@device[0].ports='lan1' 'lan2' 'lan3' 'lan4'
network.lan=interface
network.lan.device='br-lan'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.wan=interface
network.wan.device='wan'
network.wan.proto='dhcp'
network.wan6=interface
network.wan6.device='wan'
network.wan6.proto='dhcpv6'
network.gbr=device
network.gbr.name='br-guest'
network.gbr.type='bridge'
network.glan=interface
network.glan.device='br-guest'
network.glan.proto='static'
network.glan.netmask='255.255.255.0'
network.glan.ipaddr='192.168.2.1'
uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan' 'glan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.guest=zone
firewall.guest.name='guest'
firewall.guest.network='guest'
firewall.guest.input='REJECT'
firewall.guest.output='ACCEPT'
firewall.guest.forward='REJECT'
firewall.guest_wan=forwarding
firewall.guest_wan.src='guest'
firewall.guest_wan.dest='wan'
firewall.opennds=include
firewall.opennds.type='script'
firewall.opennds.path='/usr/lib/opennds/restart.sh'
uci show opennds
opennds.@opennds[0]=opennds
opennds.@opennds[0].enabled='1'
opennds.@opennds[0].fwhook_enabled='1'
opennds.@opennds[0].gatewayinterface='br-guest'
opennds.@opennds[0].gatewayport='2050'
opennds.@opennds[0].gatewayname='OpenWiFi - Beta'
opennds.@opennds[0].maxclients='250'
opennds.@opennds[0].users_to_router='allow tcp port 53' 'allow udp port 53' 'allow udp port 67' 'allow tcp port 22' 'allow tcp port 80' 'allow tcp port 443'
This is incorrect.
The correct command to set this up was:
uci set wireless.default_radio0.network='glan'
This would result in:
wireless.guest.network='glan'
-ash: wireless.guest.network=glan: not found
If you cannot see what you did wrong, I do not hold out much hope of you ever getting this working.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.