Hi all,
I've been playing with my Mikrotik hAP AC2 which has just recently became OpenWrt (snapshot) compatible.
What I've already accomplished:
- Switch all the ports together and disable DHCP on LAN
- Made a WPA3 wireless that adds clients to this network
- Followed this guide to make a second Guest wireless network with DHCP
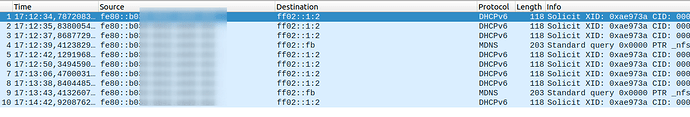
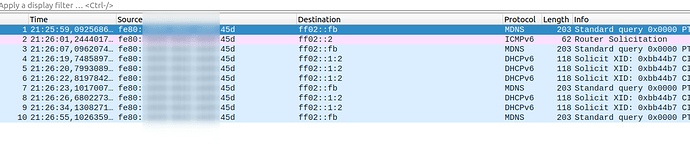
- I've made a DHCPv6 client interface that gets a public delegated IPv6 prefix (PD) from my router
The only thing I can't get to work is to get a IPv6 address from the LAN > Guest network through the correct icmp traffic rules or through DHCPv6 relay with a delegated address.
The LAN wireless clients do get a IPv6 address. I also tried to use the predefined traffic rules for obtaining WAN IPv6 addresses to get to propagate them to the Guest network, with no success.
Maybe somebody wants to look through my configuration with me on a voice chat with my screen shared? In return I can add the solution we've found to above mentioned guide or a new one.
Of course the solution will also be shared here.
I'm available for the next few hours. If someone is interested, let me know. Else we can of course also do it the old-fashioned way in the thread below