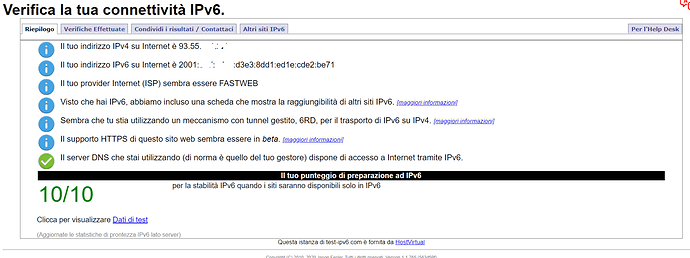
I made some tcpdump and it seems that the ping arrives on WAN but does not make the way in LAN:
root@MenionRouter:~# tcpdump -i 6in4-WAN6 "icmp6 && ( ip6[40] == 128 || ip6[40] == 129)"
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on 6in4-WAN6, link-type RAW (Raw IP), capture size 262144 bytes
11:49:13.657790 IP6 2001:xxx:yyyy:d3e3::1 > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 1, length 64
11:49:13.664296 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3::1: ICMP6, echo reply, seq 1, length 64
11:49:14.659125 IP6 2001:xxx:yyyy:d3e3::1 > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 2, length 64
11:49:14.664169 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3::1: ICMP6, echo reply, seq 2, length 64
11:49:15.661017 IP6 2001:xxx:yyyy:d3e3::1 > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 3, length 64
11:49:15.665892 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3::1: ICMP6, echo reply, seq 3, length 64
11:49:16.662738 IP6 2001:xxx:yyyy:d3e3::1 > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 4, length 64
11:49:16.667392 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3::1: ICMP6, echo reply, seq 4, length 64
11:49:17.664345 IP6 2001:xxx:yyyy:d3e3::1 > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 5, length 64
11:49:17.669144 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3::1: ICMP6, echo reply, seq 5, length 64
11:49:18.665989 IP6 2001:xxx:yyyy:d3e3::1 > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 6, length 64
11:49:18.670659 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3::1: ICMP6, echo reply, seq 6, length 64
11:49:25.116494 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 0, length 64
11:49:25.122884 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 0, length 64
11:49:25.122962 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 0, length 64
11:49:26.116781 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 1, length 64
11:49:26.121391 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 1, length 64
11:49:26.121448 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 1, length 64
11:49:27.117115 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 2, length 64
11:49:27.121627 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 2, length 64
11:49:27.121687 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 2, length 64
11:49:28.117443 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 3, length 64
11:49:28.122415 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 3, length 64
11:49:28.122485 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 3, length 64
11:49:29.117772 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 4, length 64
11:49:29.122408 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 4, length 64
11:49:29.122479 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 4, length 64
11:49:30.118101 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 5, length 64
11:49:30.123148 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 5, length 64
11:49:30.123206 IP6 mil04s24-in-x0e.1e100.net > 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c: ICMP6, echo reply, seq 5, length 64
^C
30 packets captured
30 packets received by filter
0 packets dropped by kernel
The first block is ping from the rounter (which works) the second is from a LAN device. You can see that ECHO-REPLY arrivers, but it is duplicated.
While on LAN:
root@MenionRouter:~# tcpdump -i br-lan "icmp6 && ( ip6[40] == 128 || ip6[40] == 129)"
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on br-lan, link-type EN10MB (Ethernet), capture size 262144 bytes
11:50:14.892234 IP6 fdb5:24dd:30d::3c2 > fe80::1:c8ff:feec:fc1c: ICMP6, echo request, seq 0, length 12
11:50:14.892381 IP6 fe80::1:c8ff:feec:fc1c > fdb5:24dd:30d::3c2: ICMP6, echo reply, seq 0, length 12
11:50:17.546342 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 0, length 64
11:50:18.546676 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 1, length 64
11:50:19.547006 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 2, length 64
11:50:20.547336 IP6 2001:xxx:yyyy:d3e3:c66e:1fff:fe08:9d0c > mil04s24-in-x0e.1e100.net: ICMP6, echo request, seq 3, length 64
11:50:20.928859 IP6 fdb5:24dd:30d::3c2 > fe80::1:c8ff:feec:fc1c: ICMP6, echo request, seq 0, length 12
11:50:20.928979 IP6 fe80::1:c8ff:feec:fc1c > fdb5:24dd:30d::3c2: ICMP6, echo reply, seq 0, length 12
11:50:26.967157 IP6 fdb5:24dd:30d::3c2 > fe80::1:c8ff:feec:fc1c: ICMP6, echo request, seq 0, length 12
11:50:26.967292 IP6 fe80::1:c8ff:feec:fc1c > fdb5:24dd:30d::3c2: ICMP6, echo reply, seq 0, length 12
11:50:33.002839 IP6 fdb5:24dd:30d::3c2 > fe80::1:c8ff:feec:fc1c: ICMP6, echo request, seq 0, length 12
11:50:33.002966 IP6 fe80::1:c8ff:feec:fc1c > fdb5:24dd:30d::3c2: ICMP6, echo reply, seq 0, length 12
you can see that there is no reply. Firewall rules for ICMP6 are set as default.