The lan bridge is gone. So only eth0 is active on the lan.
can i just recreate it now? maybe that's been the darn problem all along...
i create something called "br-lan" under interface tab...that it?
i tried creating my own bridge before but i called it "camera" and then the box didn't reboot
Add:
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
list ports 'eth2'
list ports 'eth3'
edit
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option delegate '0'
exciting news! i'm finally 2 steps closer:
- router reboots after setting bridge!
- i can access the ip camera inside network from computer via static address 192.168.1.10!
i seem to still be unable to access the camera from cell phone
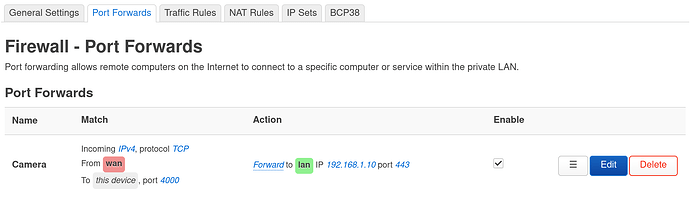
is there anything here that could block/drop my port forwarding?
cat /etc/config/firewall:
[REDACTED]
also, how do i output my port forwarding rule so you can review that too?
This does not look normal. Have you installed other packages?
all default settings though except i added netbios/ipv6 drop rules there
You should stick with the standard default release images until you have built up enough knowledge about openwrt.
also, does this part look ok?
config zone
option name 'wan'
option input 'DROP'
option output 'ACCEPT'
option forward 'DROP'
option masq '1'
option mtu_fix '1'
list network 'wan'
You don’t currently have the experience with openwrt to understand the details of what you are changing. I would strongly recommend that you use a default stable release so that you can minimize variables.
i get that i lack experience with openwrt and apparently bridging ports until now, but i know firewall/dnscrypt/port forwarding
if i'm right next to the finish line it makes little sense to go to a drastically less secure state in my network than where i came from with dd-wrt with dnscrypt-proxy, firewall, and port forwarding
could use a little more help to get from 90% solution to 100% solution here
Work the other way around. Start simple and then add complexity.
Standard build, near default. Get port forwarding working. Then add the other stuff.
I still urge you to reconsider the approach you are taking with port forwarding - use a vpn instead of port forwarding. It is much more secure.
i get its more secure using a vpn. i've got a nearly equal method without making my phone connect to my internal network.
- port forward to a higher than service port range
- ports don't match externally to internally
- internal device accepts at 443 which means it'll accept a cert
- once i can finally figure this last step out i must be doing wrong, then i can generate a "Let's Encrypt" cert and load it into my camera's configurator and phone so that the actual camera will only accept that device's connection
its really close to 1-for-1. i'm ok with 1 single high numbered port listening for TLS traffic...no different than any other business/enterprise so it blends into the noise
This is the illusion of security. It does not actually help.
This is backwards. The cert resides on the server side. It assures the client that the connection is secure. It doesn’t protect your server from attack. The server in this case is the camera.
Again, wrong angle.
yeah, you're right cert being loaded on the camera doesn't limit connections to only other devices with that cert...oh well
i'm not open to connecting phone to internal network
thanks again psherman. i'll see if someone else can jump in and help get me 90% to a 100% here
I suspect that most of the other contributors will agree with my stance and suggestions here. Your security approach is misguided and you have added unnecessary complexity to your configuration. It is best to start simple and add to your config as you learn the fundamentals.
Yes, use the default firewall config and add one redirect rule to forward the port and it should work. The firewall that you posted is very far from the default configuration, which is designed to be safe by blocking most all input from the Internet.
Double check that the IP held by the router's wan port matches that registered in ddns and reported by a "whats my IP" site. Remember that the camera does not have a public IP address or DNS name, the router does.
It would be nice if cameras did that but I'm not aware of any that do, even a certain high-end brand that we use at work. You could set this up with a proxy server somewhere in between the phone and the camera but that's an advanced topic.
If the camera did authenticate clients via certificates, you'd do that by building your own PKI system, and installing the public part of your system CA into the camera. Then the camera would only connect to clients that hold a certificate signed with that CA. Lets Encrypt is not for this use case; it is for server certificates for servers with a public DNS name and connection.
can't get around this error in the system log no matter what settings i change:
Sat Apr 27 14:04:11 2024 kern.warn kernel: [ 1429.020718] drop wan in: IN=eth1 OUT= MAC=[REDACTED DEVICE ID] SRC=[REDACTED CARRIER IP] DST=[REDACTED PUBLIC IP] LEN=40 TOS=0x00 PREC=0x00 TTL=51 ID=14939 PROTO=TCP SPT=20850 DPT=23 WINDOW=26957 RES=0x00 SYN URGP=0
edit: this was just some random port scan filling my log..not my phone's attempt to access the ip camera like i thought
well i unplugged/plugged in my camera after triple-checking my configs everywhere and it finally worked...i can finally view video feed from phone
thanks again to you both and sorry for the frustration
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.