For the n-th time...
![]()
copy-paste --- screenshots are not good. Follow the directions in my last post (and the several posts before that).
And we need the info from the OpenWrt device.
I'm happy to help, but I'm seriously about to give up here since you are not giving us what we need, despite being asked numerous times.
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd3b:6333:6f1c::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option proto 'static'
option ip6assign '60'
option gateway '10.1.0.4'
option device 'br-lan'
list ipaddr '192.168.33.1/25'
config device
option name 'eth0.2'
option macaddr '5c:a6:e6:d3:19:84'
config interface 'wan'
option proto 'dhcp'
option device 'eth0.2'
option peerdns '0'
list dns '1.1.1.1'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
config device
option name 'VPN'
config interface 'wg'
option proto 'wireguard'
option private_key '4LKIP9accNXm6H52k2mN7s6DJjEr+UQtVSGhBGC2B2Q='
list addresses '10.0.0.8/8'
config wireguard_wg
option description 'wireguard'
option public_key 'V8Ap9GsIm0Fcn5rvEhuMrZDwkAE+Eg2nanbQdexEWwM='
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '161.97.156.107'
option endpoint_port '51820'
option persistent_keepalive '25'
And the firewall file?
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg'
config zone 'wan'
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option input 'ACCEPT'
option masq '1'
option forward 'ACCEPT'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config forwarding
option src 'lan'
option dest 'wan'
config zone
option name 'VPN'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config forwarding
option src 'VPN'
option dest 'lan'
Thank you. This is post 27 in this thread. It could have been solved by the 4th-6th post if you had followed my initial request. Anyway... here's how you solve your issue:
Remove wg from the LAN zone, create a new zone for wg and enable masquerading on it. Then add forwarding from the lan zone to wg zone.
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone 'lan'
option name 'wg'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'wg'
option masq '1'
config forwarding
option src 'lan'
option dest 'wg'
In this section I need to follow last step that you mention , is that correct ?
Remove this. Follow what I said above.
Still the same issue not changes at all.
Made changes as per your instructions and restarted router.
at the server connection looks just fine
endpoint: 161.97.156.107:51820
allowed ips: 0.0.0.0/0
latest handshake: 38 seconds ago
transfer: 276 B received, 8.67 KiB sent
persistent keepalive: every 25 seconds
Post the latest config files for both sides.
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd3b:6333:6f1c::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option proto 'static'
option ip6assign '60'
option device 'br-lan'
list ipaddr '192.168.33.1/25'
option gateway '10.0.0.8'
config device
option name 'eth0.2'
option macaddr '5c:a6:e6:d3:19:84'
config interface 'wan'
option proto 'dhcp'
option device 'eth0.2'
option peerdns '0'
list dns '1.1.1.1'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
config device
option name 'VPN'
config interface 'wg'
option proto 'wireguard'
option private_key '4LKIP9accNXm6H52k2mN7s6DJjEr+UQtVSGhBGC2B2Q='
list addresses '10.0.0.8/8'
config wireguard_wg
option description 'wireguard'
option public_key 'V8Ap9GsIm0Fcn5rvEhuMrZDwkAE+Eg2nanbQdexEWwM='
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '161.97.156.107'
option endpoint_port '51820'
option persistent_keepalive '25'
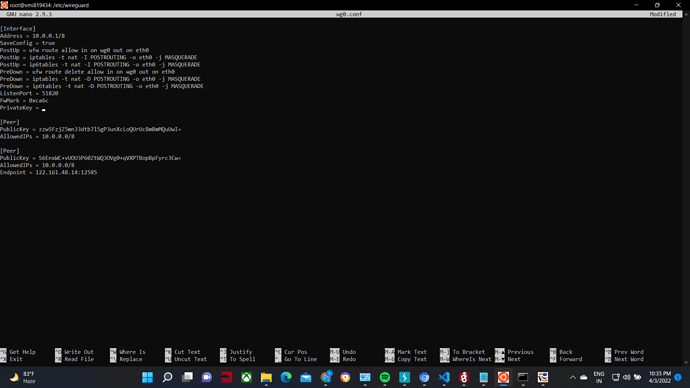
Server network configuration
[Interface]
Address = 10.0.0.1/8
SaveConfig = true
PostUp = ufw route allow in on wg0 out on eth0
PostUp = iptables -t nat -I POSTROUTING -o eth0 -j MASQUERADE
PostUp = ip6tables -t nat -I POSTROUTING -o eth0 -j MASQUERADE
PreDown = ufw route delete allow in on wg0 out on eth0
PreDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
PreDown = ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
ListenPort = 51820
FwMark = 0xca6c
PrivateKey =
[Peer]
PublicKey = zzw5FzjZ5mn33dtb7l5gP3unXcLoQUrUcBmBmMQuUwI=
AllowedIPs = 10.0.0.0/8
[Peer]
PublicKey = S6EnxWC+vUOU3P60ZtWQ3OVg0+qVXPTBopBpFyrc3Cw=
AllowedIPs = 10.0.0.0/8
Endpoint = 122.161.48.14:12585
Since these are road warrior / NATd road warrior clients, the allowed_ips at the server need only be that client's IP on the tunnel such as 10.0.0.8/32. The Wireguard interface on the server holds 10.0.0.1 but it needs a netmask large enough to include all the clients, such as /24. There's no reason to use a whole /8 for a few tunnel machines.
What does not work? There is a VPN connection now you need to troubleshoot to break down into sections why the overall goal of reaching the Internet from a LAN machine is not working.
This is a good start, but you're just pinging your own router at your end of the tunnel, as you can see from the very low ping times. The next steps would be:
From the router ping the server end of the tunnel 10.0.0.1.
From the router ping and traceroute a numeric IP on the Internet such as 8.8.8.8. The traceroute should show it going through the VPN server.
From the router ping a site on the Internet by name (e.g. dns.google which is 8.8.8.8). If you can ping by number but not by name, the DNS configuration is wrong.
After all of that works, go to a LAN machine and repeat those tests.
But first since you've posted your private keys (and server address) you need to immediately re-key.
packet lost
PING 10.0.0.1 (10.0.0.1): 56 data bytes
--- 10.0.0.1 ping statistics ---
5 packets transmitted, 0 packets received, 100% packet loss
These are wrong.
The IP address here should match the IP address of the interface. Whichever of the two peers in your server config relates to the openwrt router should be 10.0.0.8/32
The other one should have another /32 address (say 10.0.0.5/32 or whatever matches that remote peer address.
IP is replaced to 10.0.0.8/8 AllowedIP on server within peer..
As per range I am using class A classful /8
There is no reason to use a /8, but it won’t harm anything. But your peers need to be defined as /32.
I am trying to create Wireless Mesh network using this sub net.