get 404 page
fixed:
apt install nodejs npm
and cross compiling adguard
I think the step is required on dev side?
I am not familiar to recompile software on an embedded router device.
cant use openvpn while adguardhome is installed. i get this error.
daemon.err AdGuardHome[16274]: 2024/08/01 02:38:13.699994 [error] dnsproxy: 4.2.2.3:53: response received over udp: "exchanging with 4.2.2.3:53 over udp: read udp 10.96.0.20:57992->4.2.2.3:53: i/o timeout"
fix?
also vpn fails to connect. but everything works after uninstalling adguardhome
Cross compiling on servers or workstations.
I installed AdGuard Home and immediately the Update Lists.... options in OpenWrt stopped working, any idea what could be the cause and how to fix it:
*** Failed to download the package list from https://downloads.openwrt.org/releases/23.05.4/targets/mediatek/filogic/packages/Packages.gz
Hi there, got the same issue now, i am unable to download packages:
Failed to download the package list from https://downloads.openwrt.org/releases/23.05.4/targets/rockchip/armv8/packages/Packages.gz
Is it possible to understand in simple language how does the Lan address and loopback in upsteam would avoid problems with DNS queries. Also what does local dns query mean. Aren't all queries directed locally to adguard? .
I leave you some excerpts from the adguardhome wiki
LAN domain interception
Adding the following to the Upstream DNS Server configuration will intercept any LAN domain request or requests without a FQDN and pass those requests to the appropriate resolver, which is mostly like your OpenWrt router but it doesn't have to be.
The default LAN domain configured by OpenWrt is “lan”, but if you have configured you own domain, you can use this in the example code below:
(127.0.0.1) local loopback is used here to enable statistics tracking but you may also use your router ip (192.168.1.1) here too.
Settings → DNS Settings > Upstream Servers
[/lan/]127.0.0.1:54 [//]127.0.0.1:54
On the other hand, it is also necessary to make adjustments so that PTR queries work properly.
Reverse DNS (rDNS)
To enable rDNS so AGH picks up your DHCP assignments from OpenWrt.
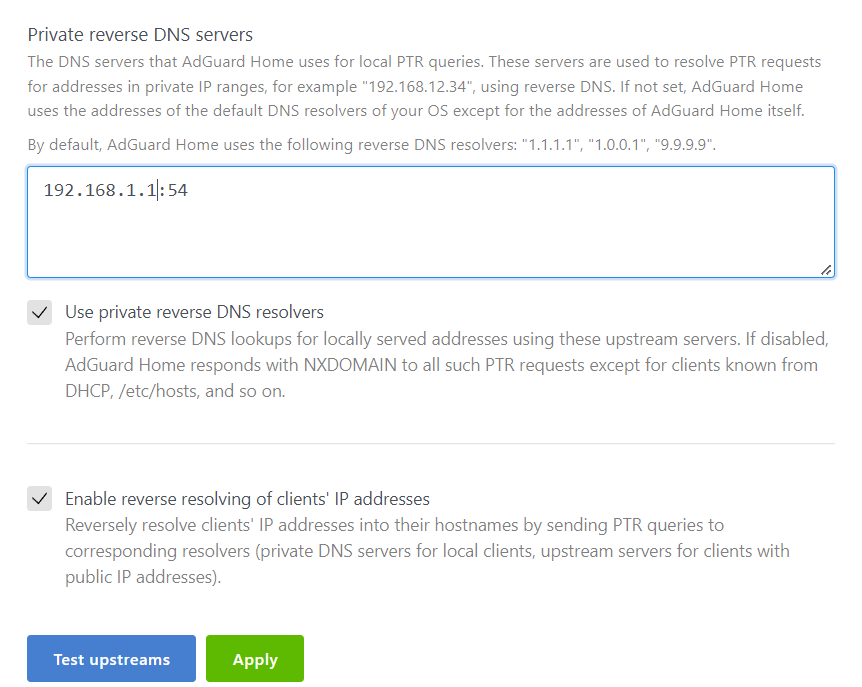
From the AdGuard Home web interface Settings → DNS settings
Scroll to “Private reverse DNS servers”
Add
192.168.1.1:54Tick both “Use private reverse DNS resolvers” and “Enable reverse resolving of clients' IP addresses” boxes and click apply.
Can someone explain to me (complete noob), how can I force Dns-over-https via adguard for all devices connected to my router?
Just add correct upstream dns server (like https://dns.cloudflare.com/dns-query) to Settings -> DNS Settings, right?
Also currently I have adguard binded to all interfaces. Why is it bad?
Partially correct. I've added both Google and Cloudflare and set to Parallel Requests.
Then, go to firewall and paste this:
config redirect
option dest 'lan'
option target 'DNAT'
option src 'lan'
option src_dport '53'
option name 'AdGuardHome DNS Interception'
option src_ip '!192.168.1.1'
option dest_ip '192.168.1.1'
option dest_port '53'
config nat
option name 'Prevent hardcoded DNS'
list proto 'tcp'
list proto 'udp'
option src 'lan'
option dest_ip '192.168.1.1'
option dest_port '53'
option target 'MASQUERADE'
Explanation is here: https://openwrt.org/docs/guide-user/services/dns/adguard-home
This is how it's gonna look in yaml file
dns:
bind_hosts:
- 192.168.1.1
- 127.0.0.1
port: 53
- For the security purpose.
- If bound to all interfaces then you'll see spam of unimportant addresses in Dashboard
I also have WireGuard interface (router automatically reroutes some websites to it). Do I need also to bind wg interface in Adguard's yaml?
@mercygroundabyss I am using OpenWrt 23.05.4 with IPv6 configured in NDP-Proxy mode, also known as Relay mode, because my ISP doesn't provide PD (Prefix Delegation), in this scenario the router doesn't have an IPv6 address assigned, should I leave it blank or should I add the IPv6 address of the upstream DHCPv6 server router providing all the IPv6 addresses that are being Passthrough the OpenWrt router? Thank you for creating this great guide
Nope, assuming the port is still set to the default 53, as I noted above.
In Network:
config interface 'wg0'
option proto 'wireguard'
option private_key 'xxxxx'
option peerdns '0'
list dns '1.1.1.1'
list addresses '2606:4700xxxxxx'
list addresses '172.xxxx/32'
config wireguard_wg0
option description 'wgcf-profile.conf'
option public_key 'xxxxxxxxxx'
option endpoint_host 'engage.cloudflareclient.com'
option endpoint_port 'xxxx'
list allowed_ips '::/0'
list allowed_ips '0.0.0.0/0'
option persistent_keepalive '25'
option route_allowed_ips '1'
Above example is for Clouflare warp
I have been using these rules for quite a while now, since around the time that you first shared them. Thank you for sharing these rules, by the way. They have always worked well.
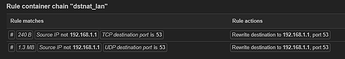
I do have a question though. I have always understood what is happening with the first rule.
If you have a moment, could you please explain to me what exactly happens behind-the-scenes with the nat rule?
I've just never been able to wrap my mind around what triggers it, how the firewall responds in that case, etc. Also, I have never seen any bytes counting up in the Firewall section over the last year or so, so I assume that it just has not been triggered in my network.
The idea is to prevent devices on your network from bypassing AGH by forcing all DNS queries through your router. That NAT rule captures that traffic & ensures it's redirected to the router itself (on port 53).
This prevents devices from using external DNS servers bcz all DNS traffic is routed through the router, allowing AGH to filter or process it.
Whereas MASQUERADE performs source NAT replacing the source IP address of the traffic with your router's WAN IP forcing the router to intercept and handle the DNS request.
Idk maybe your devices are already using the router for DNS or they just not trying to use a hardcoded DNS server not sure. For me it shows up:
Excellent information. That helped a lot. I appreciate it.
Can we somehow persist the AGH Installation during sysupgades?
Its such a chore that i often forget and end up breaking my entire network for hours.
just install using opkg rather manual
For mine, I added the AGH binary and the init.d script to the sysupgrade config. That worked well in my case. That was about a year ago though. I also added the automatic disabling of dnsmasq at that time too but your setup may not need that.
... done the same way.
@CrackedPotato
And added in Luci the backup & restore configuration parameters as follows (result can be found in /etc/sysupgrade.conf):
/usr/bin/AdGuardHome
/usr/bin/enable-adguardhome-update-check
/usr/bin/data
/usr/bin/AdGuardHome.yaml
/etc/init.d/AdGuardHome
/root/update-adguardhome.sh
Content of /root/update-adguardhome.sh can be found here: