Hi! Sorry fo english.
I have internet access from PC and from my router (from openwrt admin) via my 3g qmi modem. PC to router connect by LAN cable.
But i cant understand, how share internet from 3g modem to wifi?
i have not lan internet connection - only 3g modem.
Pls help!!!
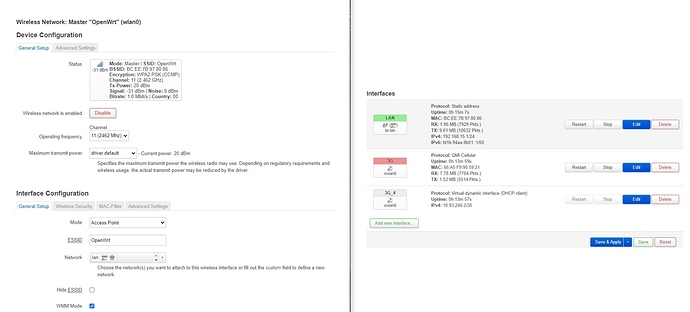
Wifi looks like it is enabled and broadcasting.
Can your wifi devices see 'OpenWrt' SSID ?
Thx for answer!
yes, the devices are connected. And it seems like it shows that there is a connection, but I can't get to the Internet. In other cases, they write that there is no Internet connection.
Use ssh to connect to the device.
Then run the following commands, copy the output, and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have
ubus call system board; \
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
ls -l /etc/resolv.* /tmp/resolv.*; head -n -0 /etc/resolv.* /tmp/resolv.*
Hello! Thx for attention!
root@OpenWrt:~# ubus call system board
{
"kernel": "4.14.180",
"hostname": "OpenWrt",
"system": "Broadcom BCM4716",
"model": "Asus RT-N16",
"board_name": "0x04cf:45",
"release": {
"distribution": "OpenWrt",
"version": "19.07.3",
"revision": "r11063-85e04e9f46",
"target": "brcm47xx/mips74k",
"description": "OpenWrt 19.07.3 r11063-85e04e9f46"
}
}
root@OpenWrt:~# uci export network
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd1b:94aa:8b01::/48'
config interface 'lan'
option ifname 'eth0.2'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.15.1'
option gateway '192.168.1.1'
list dns '8.8.8.8'
list dns '4.2.2.2'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 8t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 2 3 4 8t'
config interface '3g'
option proto 'qmi'
option device '/dev/cdc-wdm0'
option pdptype 'ipv4'
option apn 'internet'
option auth 'none'
config interface 'wan'
option ifname 'wlan0'
option proto 'dhcp'
option delegate '0'
root@OpenWrt:~# uci export wireless
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'bcma0:1'
config wifi-iface 'wifinet0'
option ssid 'OpenWrt'
option encryption 'psk2'
option device 'radio0'
option mode 'ap'
option key '11111111'
root@OpenWrt:~# uci export dhcp
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@OpenWrt:~# uci export firewall
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network '3g wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
root@OpenWrt:~# head -n -0 /etc/firewall.user
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
root@OpenWrt:~# iptables-save -c
# Generated by iptables-save v1.8.3 on Wed Sep 2 13:06:25 2020
*nat
:PREROUTING ACCEPT [105:41280]
:INPUT ACCEPT [7:640]
:OUTPUT ACCEPT [66:4821]
:POSTROUTING ACCEPT [39:2769]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[105:41280] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[74:37700] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i wwan0 -m comment --comment "!fw3" -j zone_wan_prerouting
[107:33770] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_lan_postrouting
[68:31001] -A POSTROUTING -o wwan0 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[74:37700] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[68:31001] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[68:31001] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Wed Sep 2 13:06:25 2020
# Generated by iptables-save v1.8.3 on Wed Sep 2 13:06:25 2020
*mangle
:PREROUTING ACCEPT [3014:949042]
:INPUT ACCEPT [1472:202234]
:FORWARD ACCEPT [1485:735117]
:OUTPUT ACCEPT [1650:740087]
:POSTROUTING ACCEPT [3135:1475204]
[11:580] -A FORWARD -o wwan0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Wed Sep 2 13:06:25 2020
# Generated by iptables-save v1.8.3 on Wed Sep 2 13:06:25 2020
*filter
:INPUT ACCEPT [27:8856]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[382:30412] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[1092:171902] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[1059:162734] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[6:312] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[6:312] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i wwan0 -m comment --comment "!fw3" -j zone_wan_input
[1485:735117] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[1420:698942] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[65:36175] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i wwan0 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[382:30412] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[1272:710507] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[1245:708455] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_lan_output
[27:2052] -A OUTPUT -o wwan0 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[6:312] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_lan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[65:36175] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[65:36175] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[6:312] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[6:312] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[0:0] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[0:0] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[6:312] -A zone_lan_src_ACCEPT -i eth0.2 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o wwan0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[92:38227] -A zone_wan_dest_ACCEPT -o wwan0 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o wwan0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[0:0] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[27:2052] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[27:2052] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i wwan0 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Wed Sep 2 13:06:25 2020
root@OpenWrt:~# ip -4 addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
4: wwan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN qlen 1000
inet 10.33.190.53/30 brd 10.33.190.55 scope global wwan0
valid_lft forever preferred_lft forever
10: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.15.1/24 brd 192.168.15.255 scope global eth0.2
valid_lft forever preferred_lft forever
root@OpenWrt:~# ip -4 ro li tab all
default via 10.33.190.54 dev wwan0 src 10.33.190.53
10.33.190.52/30 dev wwan0 scope link src 10.33.190.53
192.168.15.0/24 dev eth0.2 scope link src 192.168.15.1
broadcast 10.33.190.52 dev wwan0 table local scope link src 10.33.190.53
local 10.33.190.53 dev wwan0 table local scope host src 10.33.190.53
broadcast 10.33.190.55 dev wwan0 table local scope link src 10.33.190.53
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.15.0 dev eth0.2 table local scope link src 192.168.15.1
local 192.168.15.1 dev eth0.2 table local scope host src 192.168.15.1
broadcast 192.168.15.255 dev eth0.2 table local scope link src 192.168.15.1
root@OpenWrt:~# ip -4 ru
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
ls -l /etc/resolv.* /tmp/resolv.*
lrwxrwxrwx 1 root root 16 May 16 18:32 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 Sep 2 12:55 /tmp/resolv.conf
-rw-r--r-- 1 root root 114 Sep 2 12:58 /tmp/resolv.conf.auto
root@OpenWrt:~# head -n -0 /etc/resolv.* /tmp/resolv.*
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.auto <==
# Interface 3g_4
nameserver 10.10.32.130
nameserver 8.8.8.8
# Interface lan
nameserver 8.8.8.8
nameserver 4.2.2.2
Remove the gateway, the DNS should be under 3g interface.
wireless is not associated with lan network.
option network 'lan' is missing.
Yes, attach the wifi AP to the lan network. This can be done at the bottom of the wifi AP's configuration page, or as @trendy said, adding an option network line to the wifi-iface definition. Then wifi users will have the same service that wired connections to the LAN do.
And in your /etc/config/network, the wan network refers to wlan0. This is incorrect. Remove the wan network entirely. You only need two networks: lan and 3g. The firewall will route Internet requests from lan to 3g like a wan in a wired installation.
I delete wan interface at all.
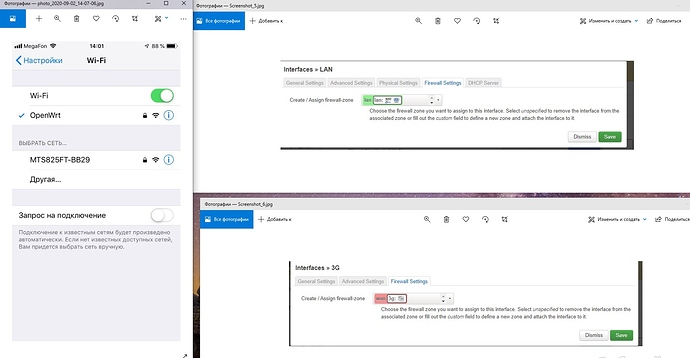
Delete gateway from LAN settings, and delete DNS.
In my wifi AP select network to LAN.
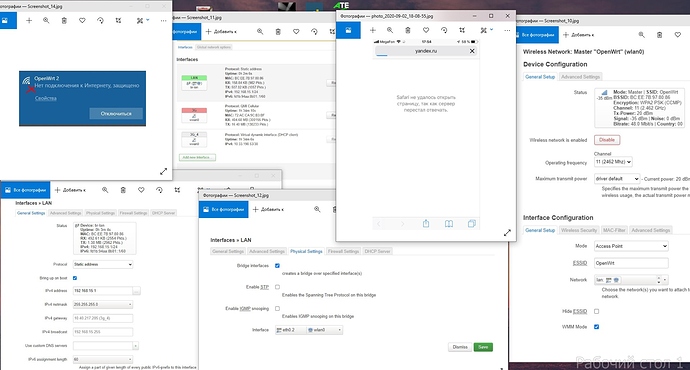
in this time in LAN settings - at this time, a check mark appeared opposite Bridge in the LAN settings. Two interfaces are marked. eth0.2 and wlan0
Make reboot.
In the end, nothing has changed. The phone says that it is connected to WiFi, but there is no Internet. PC says there is no internet connection.
uci export network
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd1b:94aa:8b01::/48'
config interface 'lan'
option ifname 'eth0.2'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.15.1'
option type 'bridge'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 8t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 2 3 4 8t'
config interface '3g'
option proto 'qmi'
option device '/dev/cdc-wdm0'
option pdptype 'ipv4'
option apn 'internet'
option auth 'none'
uci export wireless
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'bcma0:1'
config wifi-iface 'wifinet0'
option ssid 'OpenWrt'
option encryption 'psk2'
option device 'radio0'
option mode 'ap'
option key '11111111'
option network 'lan'
Please don't post screenshots.
Another mistake I didn't see earlier:
You have disabled the dhcp server for lan. Enable it or use static IP on your clients.
YES! EVERYTHING WORKS!)) Guys! Thank you all! To everyone who responded! trendy - you are cool!
I lost two days before asking here! I thought I'd go crazy!
THX everyone!))
You deviated too much from the default OpenWrt configuration, which would work fine for you. In such cases it makes more sense to restore to defaults and start configuring from scratch.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.