I've gone a bit crosseyed trying to find and understand the ways program the OpenWRT firmware to take a DNS/NTP query going to an external IP hardcoded into an old IOT device (Ooma Hub VOIP device) to a working DNS name or IP. I'm just not experienced enough to translate what others have done for similar issues into what to do in my firmware to make this work.
What's happening:
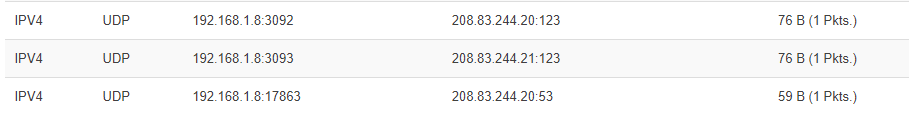
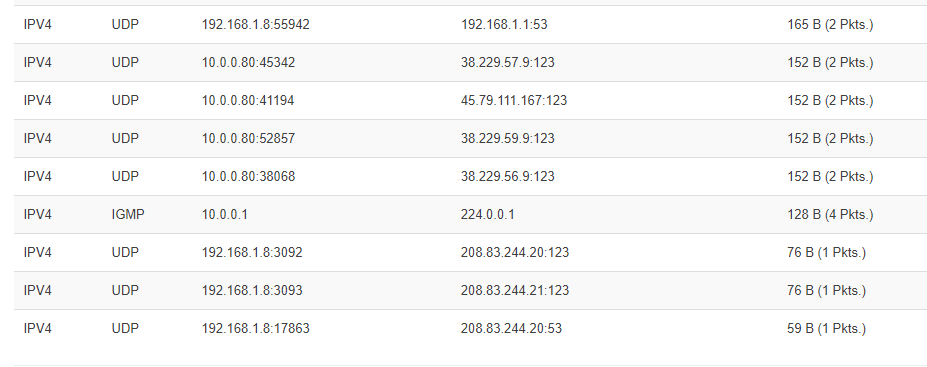
I have an old Ooma hub wich reaches out to 208.83.244.20 and .244.21 on ports 53 and 123 in order to begin connecting to the Ooma VOIP network. The reverse DNS on .244.21 is ns2.ooma.com, but an NSLookup to ns2.ooma.com to just about any DNS server says its .246.21, not .244.21. Ooma Tier 3 service people imply that .244.20 and .21 are still up and working, but tracert to those IPs (from some locations apprently) says there's a backbone problem where communication dead ends out at us.zip.zayo.com (confirmed by a lot of owners of this device - see the Reddit Ooma section). There's no telling if Ooma's engineers (who have been alerted to the problem) will take the time to work with the tech support in that part of the backbone to resolve an issue for old out of warrenty unsupported devices either. That means a factory reset of the device doesn't work for some of us.
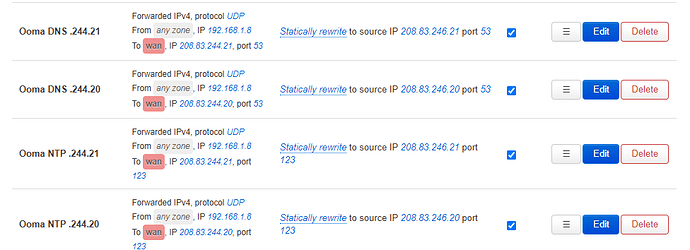
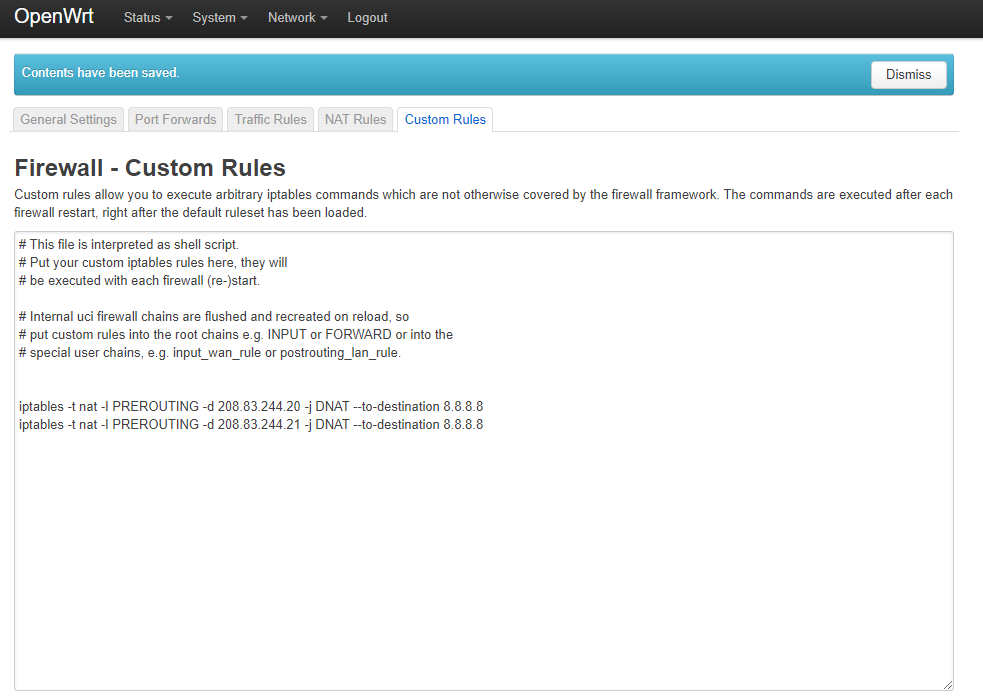
There are a number of savvy users who've redirected the .244.21 (or 20) queries to either Google's 8.8.8.8 or an actual reachable Ooma DNS (208.83.246.21), and their device begin working fine again.
I've tried using SSH Putty to send this command:
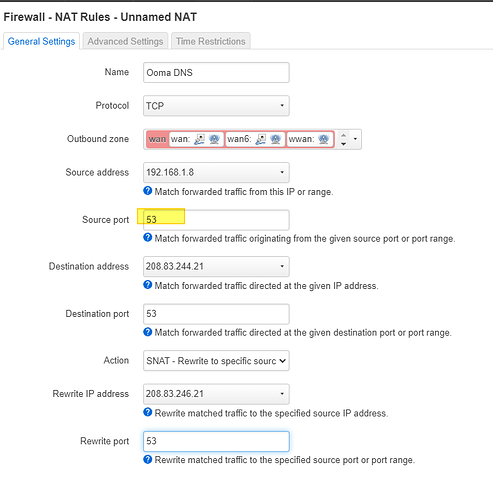
iptables -t nat -I PREROUTING -d 208.83.244.20 -j DNAT --to-destination 8.8.8.8
But I later read read why this command wasn't working (because OpenWRT depreciates iptables to be managed with FW3 apparently which.. I'm just not familiar with any more so than I fully understand iptables.) (per tab and per-field instructions would be great if I could ask for that...)
Do I need a plugin to make this happen? Will I have to manually write this into one of the files on the device?
Is it easier to do this substituting one IP for another instead of an IP --> DNS name (like a reverse host file entry). I think I'd prefer a reverse host entry so that ns2.ooma.com is always whatever is reachable, but if that's more complex than direct IP substitution I might reconsider.
Sorry for being too much of a newb to really ask the questions well, or understand the various solutions worked out by others for similar problems.
~FerrariGuy
OpenWrt 21.02.1 r16325-88151b8303 btw. WND3700 Netgear V1 (low memory) if it matters.