krazeh
June 10, 2020, 11:30am
21
On the 'Server' change
config wireguard_wg0
option description 'Client pc'
option route_allowed_ips '1'
option public_key '<KEY>'
list allowed_ips '192.168.10.16/32'
to
config wireguard_wg0
option description 'Client pc'
option route_allowed_ips '1'
option public_key '<KEY>'
list allowed_ips '0.0.0.0/0'
On the 'client' change
config wireguard_wg0
option description 'server PC'
option public_key '<KEY>'
option route_allowed_ips '1'
list allowed_ips '192.168.10.1/32'
to
config wireguard_wg0
option description 'server PC'
option public_key '<KEY>'
option route_allowed_ips '1'
list allowed_ips '192.168.10.1/32'
list allowed_ips '192.168.1.1/32'
Restart the interface on both sides.
1 Like
hdog01
June 10, 2020, 11:32am
22
Yes sir. I will run home and test!
krazeh
June 10, 2020, 12:09pm
24
You need to be more detailed. Ping from where? To where? What were you expecting to see? What did you see?
Please don't respond with one line. Take some time and put together a detailed response fully explaining your setup (on both sides) and what exactly it is that you are wanting to happen.
2 Likes
I think the OP wants a simple VPN server...but this terminology about an "seeing IPs" is confusing.
Being very clear about what you're trying to accomplish would be helpful.
2 Likes
hdog01
June 11, 2020, 11:29am
26
Tested for a few days.
server
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd15:5672:3a87::/48'
option multipath 'disable'
option mptcp_path_manager 'fullmesh'
option mptcp_scheduler 'default'
option mptcp_checksum '0'
option mptcp_debug '0'
option mptcp_syn_retries '5'
option mptcp_fullmesh_num_subflows '1'
option mptcp_fullmesh_create_on_err '1'
option mptcp_ndiffports_num_subflows '1'
option congestion 'cubic'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
option multipath 'off'
config interface 'lan'
option proto 'static'
option multipath 'off'
option ipaddr '192.168.0.40'
option netmask '255.255.254.0'
option ifname 'eth0'
config interface 'wg0'
option proto 'wireguard'
list addresses '192.168.10.1/32'
option listen_port '51820'
option private_key '<KEY>'
option multipath 'off'
config wireguard_wg0
option description 'Client'
option route_allowed_ips '1'
option public_key '<KEY>'
list allowed_ips '0.0.0.0/0'
option endpoint_host '121.185.53.XXX'
option endpoint_port '51820'
config wireguard_wg0
option description 'mobile'
option public_key '<KEY>'
list allowed_ips '192.168.10.17/32'
option route_allowed_ips '1'
Client
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd15:5672:3a87::/48'
option multipath 'disable'
option mptcp_path_manager 'fullmesh'
option mptcp_scheduler 'default'
option mptcp_checksum '0'
option mptcp_debug '0'
option mptcp_syn_retries '5'
option mptcp_fullmesh_num_subflows '1'
option mptcp_fullmesh_create_on_err '1'
option mptcp_ndiffports_num_subflows '1'
option congestion 'cubic'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'lan'
option proto 'static'
option ifname 'eth0'
option multipath 'off'
option netmask '255.255.254.0'
option ipaddr '192.168.0.1'
config interface 'wg0'
option proto 'wireguard'
option private_key '<KEY>'
option listen_port '51820'
list addresses '192.168.10.16/32'
config wireguard_wg0
option description 'mobile'
option public_key '<KEY>'
list allowed_ips '192.168.10.15/32'
option route_allowed_ips '1'
config wireguard_wg0
option description 'server'
option public_key '<KEY>'
option endpoint_host '14.50.148.XXX'
option endpoint_port '51820'
option route_allowed_ips '1'
list allowed_ips '192.168.10.1/32'
list allowed_ips '192.168.1.2/32'
trendy
June 11, 2020, 12:49pm
27
FYI, having the same IPs in LAN interfaces of both server and client is complicating things. You won't be able to reach each other. Nor the allowed IP 192.168.1.2/32 in wg0 is correct, since it conflicts with the lan subnet.
2 Likes
hdog01
June 11, 2020, 1:01pm
28
Need to change the subnet? Please tell me how. Thank you.
trendy
June 11, 2020, 1:13pm
29
The easiest way is to go to Luci Network/Interfaces/ Edit lan and change the IP address to something not overlapping, like 192.168.2.1
2 Likes
hdog01
June 11, 2020, 1:21pm
30
192.168.10.1/32 Can I use this as well?
trendy
June 11, 2020, 1:51pm
31
These are WG tunnel IPs and they don't overlap with 192.168.0.0/23 or 192.168.2.0/23 that will be the lan subnets, so you can use them.
2 Likes
hdog01
June 12, 2020, 9:54am
32
I reconstructed from scratch.
Server network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd15:5672:3a87::/48'
option multipath 'disable'
option mptcp_path_manager 'fullmesh'
option mptcp_scheduler 'default'
option mptcp_checksum '0'
option mptcp_debug '0'
option mptcp_syn_retries '5'
option mptcp_fullmesh_num_subflows '1'
option mptcp_fullmesh_create_on_err '1'
option mptcp_ndiffports_num_subflows '1'
option congestion 'cubic'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
option multipath 'off'
option peerdns '0'
config interface 'lan'
option proto 'static'
option multipath 'off'
option netmask '255.255.254.0'
option ifname 'eth0'
option ipaddr '192.168.0.40'
config interface 'wg0'
option proto 'wireguard'
option listen_port '51820'
option private_key '<key>'
option multipath 'off'
list addresses '10.66.66.1/24'
config wireguard_wg0
option description 'Client'
option public_key '<key>'
option endpoint_host '121.185.53.xxx'
option endpoint_port '51820'
option route_allowed_ips '1'
list allowed_ips '10.66.66.2/32'
config wireguard_wg0
option description 'mobile'
option public_key '<key>'
option route_allowed_ips '1'
list allowed_ips '10.66.66.12/32'
Server firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option network 'lan'
option mtu_fix '1'
config zone
option name 'wan'
option network 'wan'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option mtu_fix '1'
config redirect
option enabled '1'
config rule
option enabled '1'
option target 'ACCEPT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'unblockmusic'
option type 'script'
option path '/var/etc/unblockmusic.include'
option reload '1'
config redirect
option target 'DNAT'
option proto 'tcp udp'
option src 'wan'
option src_dport '80'
option dest 'lan'
option dest_port '80'
config redirect
option target 'DNAT'
option name '2'
option proto 'tcp udp'
option src 'wan'
option src_dport '80'
option dest 'wan'
option dest_port '80'
config zone
option name 'wg0'
option output 'ACCEPT'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
option network 'wg0'
option masq '1'
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '51820'
option name 'Allow-Wireguard-Inbound'
config forwarding
option src 'lan'
option dest 'wg0'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'wan'
option dest 'wg0'
config forwarding
option src 'wg0'
option dest 'lan'
Client network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd15:5672:3a87::/48'
option multipath 'disable'
option mptcp_path_manager 'fullmesh'
option mptcp_scheduler 'default'
option mptcp_checksum '0'
option mptcp_debug '0'
option mptcp_syn_retries '5'
option mptcp_fullmesh_num_subflows '1'
option mptcp_fullmesh_create_on_err '1'
option mptcp_ndiffports_num_subflows '1'
option congestion 'cubic'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wg0'
option proto 'wireguard'
option private_key '<key>='
option listen_port '51820'
option multipath 'off'
list addresses '10.66.66.2/24'
config wireguard_wg0
option description 'mobile'
option public_key '<key>'
option route_allowed_ips '1'
list allowed_ips '10.66.66.11/32'
config wireguard_wg0
option description 'server'
option public_key '<key>'
option endpoint_host '14.50.148.xx'
option endpoint_port '51820'
option route_allowed_ips '1'
list allowed_ips '192.168.1.2/32'
list allowed_ips '10.66.66.1/32'
Client firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option fullcone '1'
option network ' '
config zone
option name 'wan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option mtu_fix '1'
option fullcone '1'
option network 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'unblockmusic'
option type 'script'
option path '/var/etc/unblockmusic.include'
option reload '1'
config redirect
option target 'DNAT'
option proto 'tcp udp'
option src 'wan'
option src_dport '80'
option dest 'lan'
option dest_port '80'
config redirect
option target 'DNAT'
option name '2'
option proto 'tcp udp'
option src 'wan'
option src_dport '80'
option dest 'wan'
option dest_port '80'
config zone
option name 'wg0'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option network 'wg0'
option masq '1'
config forwarding
option src 'lan'
option dest 'wg0'
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '51820'
option name 'Allow-Wireguard-Inbound'
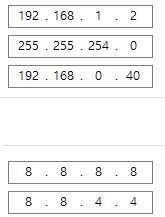
Below is the computer Ethernet network configuration.
trendy
June 12, 2020, 10:10am
33
As it is now the wireguard tunnel allows communication between the peers and the client can contact host 192.168.1.2 in server lan. I don't know if that is what you wished.
Client doesn't have lan
Both firewalls are totally open, have unnecessary forwards (e.g wan->wg) and use masquerade when it is not necessary.
1 Like
hdog01
June 12, 2020, 10:15am
34
1.The client is not using a LAN.
192.168.1.2 server I need to get 121.185.53.xxx internet from static LAN.
trendy
June 12, 2020, 10:25am
35
I didn't quite get what you mean here.
1 Like
krazeh
June 12, 2020, 10:27am
36
Me neither. It's been tricky throughout this thread to work out exactly what the OP is trying to do, what is working, and what isn't.
hdog01
June 12, 2020, 10:28am
37
The DHCP address of the client's router WAN is 121.185.53.xxx.
krazeh
June 12, 2020, 10:36am
38
list allowed_ips needs changing to '0.0.0.0/0'. On the 'client' device you need to add a forward from the wireguard zone to the wan zone.
1 Like
hdog01
June 12, 2020, 10:38am
39
I also tried this method.
But let's try again......
trendy
June 12, 2020, 11:09am
40
Do I understand correctly that the host 192.168.1.2 in server's lan must browse the internet and be visible to others with the IP 121.185.... that the client side wan has?
1 Like
hdog01
June 12, 2020, 11:13am
41
You only need to use 121.185 internet only at 192.168.1.2 address. ^^