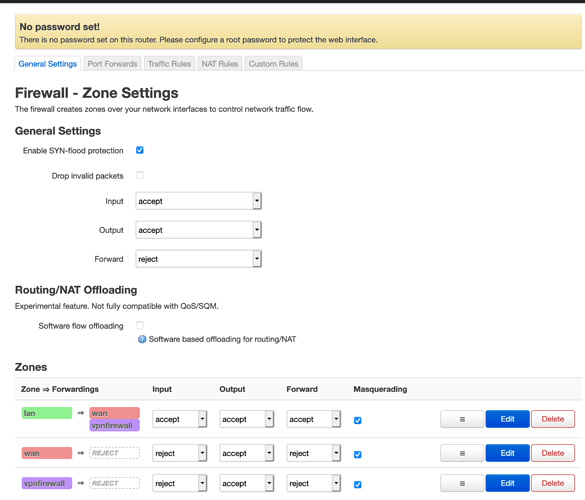
Context:
A raspberry pi with two usb ethernet adapters should become a router that sends all traffic from this clients through a vpn tunnel.
As an intermediate step, and that I understand the stuff, I wanted to have "normal" routing first. Then in the next step I care about an openvpn tunnel.
Currently:
- openwrt already installed.
- usb ethernet driver also installed.
- dhcp server is running, but routing is not.
raspi:
eth0: 10.0.0.4 static ip in my normal house network. for ssh, config etc. - independent from other routing. works.
eth1: should serve as wan, gets ip via dhcp from my main router (USG 3P, 10.0.0.1)
eth2: static ip 10.0.4.1, providing a dhcp server on it. works.
Now I wonder how to bridge the network. goal: that the clients behind eth2 are routed through eth1. (later through the tunnel).
If I connect behind eth2, I can ping 10.0.4.1 (of course), also 10.0.0.4 - but already pinging my main router 10.0.0.1 doesn't work anymore. 
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback
option ifname 'lo
option proto 'static
option ipaddr '127.0.0.1' option netmask
option netmask '255.0.0.0' config globals 'globals
config globals 'globals
option ula_prefix 'fd1f:880c:3687::/48' config interface 'eth2
config interface 'eth2
option type 'bridge
option ifname 'eth2
option proto 'static
option netmask '255.255.255.0
option ipaddr '10.0.4.1'
option igmp_snooping '1'
option stp '1
config interface 'eth0'
option ifname 'eth0
option proto 'static
option netmask '255.255.255.0
list dns '10.0.0.3' option ipaddr '10.0.0.4
option ipaddr '10.0.0.4'
option gateway '10.0.0.1
config interface 'nordvpntun
option proto 'none
option ifname 'tun0
config interface 'wan
option ifname 'eth1
option force_link '1
option proto 'dhcp
option peerdns '0'
root@OpenWrt:~# cat /proc/sys/net/ipv4/ip_forward
1
root@OpenWrt:~# ip route
default via 10.0.0.1 dev eth1 proto static src 10.0.0.173
10.0.0.0/24 dev eth0 proto kernel scope link src 10.0.0.4
10.0.0.0/24 dev eth1 proto kernel scope link src 10.0.0.173
10.0.4.0/24 dev br-eth2 proto kernel scope link src 10.0.4.1 linkdown
br-eth2 Link encap:Ethernet HWaddr 00:E0:4C:51:17:F8
inet addr:10.0.4.1 Bcast:10.0.4.255 Mask:255.255.255.0
inet6 addr: fe80::2e0:4cff:fe51:17f8/64 Scope:Link
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:471 errors:0 dropped:0 overruns:0 frame:0
TX packets:300 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:52998 (51.7 KiB) TX bytes:138836 (135.5 KiB)
eth0 Link encap:Ethernet HWaddr B8:27:EB:73:57:C4
inet addr:10.0.0.4 Bcast:10.0.0.255 Mask:255.255.255.0
inet6 addr: fe80::ba27:ebff:fe73:57c4/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:22739 errors:0 dropped:0 overruns:0 frame:0
TX packets:12074 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2939075 (2.8 MiB) TX bytes:5051816 (4.8 MiB)
eth1 Link encap:Ethernet HWaddr 00:E0:4C:08:0B:82
inet addr:10.0.0.173 Bcast:10.0.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:27095 errors:0 dropped:14 overruns:0 frame:0
TX packets:4366 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:6653975 (6.3 MiB) TX bytes:383929 (374.9 KiB)
eth2 Link encap:Ethernet HWaddr 00:E0:4C:51:17:F8
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:2992 errors:0 dropped:0 overruns:0 frame:0
TX packets:1303 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:345221 (337.1 KiB) TX bytes:590937 (577.0 KiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:4186 errors:0 dropped:0 overruns:0 frame:0
TX packets:4186 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:367210 (358.6 KiB) TX bytes:367210 (358.6 KiB)