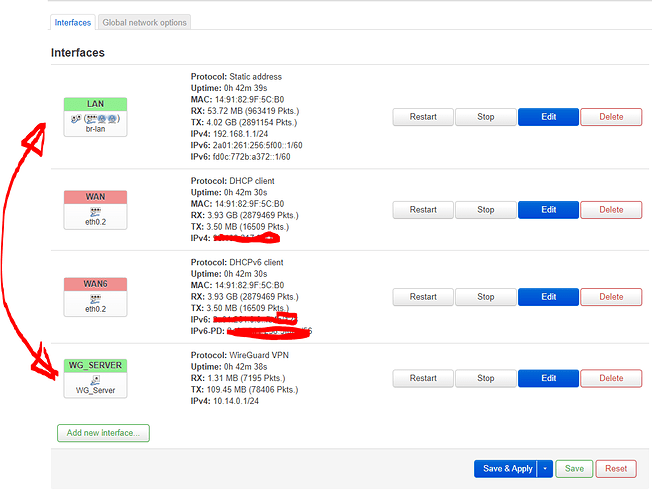
Handshake looks good. Remove the listen port from the peers and check the local firewall on the machines that are not reachable via the tunnel.
Soo i got a little too mouch informatin and getting lost with what i have to do. Shouldnt i just do something on a router to connect WG subnet (hope that is a correct term) with LAN subnet like in the picture down? Like a routing?
Routing will already work because the router understands the networks and the necessary routing. And the firewall has both interfaces in the same zone with forwarding allowed.
Ok but still there is something missing becaus i cant get on my NAS (Arrakis) that i can acess normaly on my home wifi or conected direct with cable
That's what were trying to help you solve.
Your nas appears to be running windows.
The machine (NAS) is a HP Gen8 microserver with openmediavault. If you know what to set up there much apreciated.
I can help you with OpenWrt. The rest is your responsibility. But look for the firewall settings on that system.
@psherman thats fair but i think its not the problem on NAS side, i think i need to make a route betwen LAN and WG interface, just dont know how to do it...
You dont need to make a route between 2 networks on the same device..as the device knows about itself (in fact a route should already exist).
But if you insist, it won't hurt anything. Just browse to the static route page on the router and add a unicast route.
I need to reinstal openWRT becaus u f*cked up something ![]() if anyone has any ideas the help is mouch apreciated.
if anyone has any ideas the help is mouch apreciated.
I was following this guide to setup wireguard:
But what bugs me the most when i configured the wireguard on my android and turned it on i was able to log in to the router on 192.168.1.1 but on laptop this was not possible
For the NAS, suggest changing from DHCP to a Static IP address (address before or after the DHCP range), and adding that entry in OpenWrt Network -> Hostnames: this should allow Windows to "find" the NAS server.
As far as I understand, forwarding works between zones, not within a zone. I don't think you can put the wireguard interface on the same firewall zone as the LAN interfaces and then expect that forwarding will occur between them.
So I suspect the problem is that your remote VPN "clients" have addresses in the 10.14.0.x subnet, but your LAN resources all have addresses in the 192.168.1.x subnet. DHCP on the router will be set up so that the LAN resources are given a default gateway of the router and will be told they live in 192.168.1.0/24. So when they send packets to 10.14.0.x, they will see that as existing outside the LAN and will send them not to their destination, but to the gateway address. But the router won't forward packets coming in from LAN resources on the LAN interfaces to the WG interface because they are in the same firewall zone.
You have two options:
- Place the wireguard interface into its own firewall zone. Allow forwarding from the firewall zone to the LAN zone. And then turn on masquerading for the LAN zone. This will cause the wireguard clients to get SNATed onto the router's LAN IP which will let LAN resources see them as existing on the LAN.
- Configure dnsmasq to push a route to all LAN devices to cause them to see 10.14.0.x IP addresses as not requiring a gateway.
Personally I suggest option 1 is the most appropriate.
I do this all the time. That's what the Forward firewall zone setting is for.
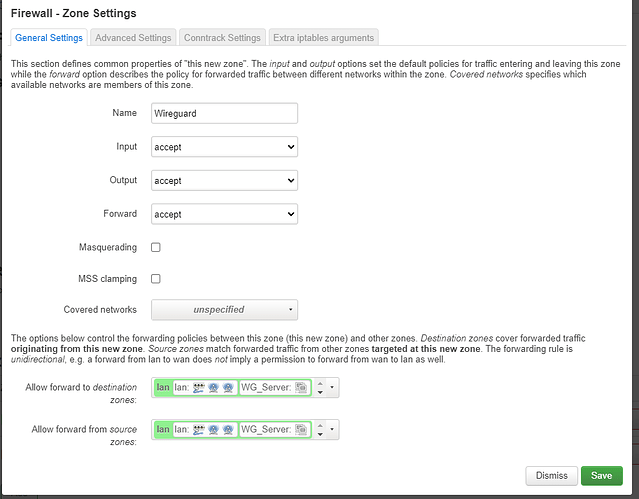
Could you explain a little more the option 1. I think that is the best way but dont really know how to implement it.
Something like that?
I think you need to add the network to the "AllowedIPs" entry, see solution post in this thread:
lleachii is right, the forward setting on the zone config is supposed to allow forwarding between interfaces within a zone. I'll just add that I've never gotten this to work with a Wireguard interface. It may just be something I'm doing wrong, though.
In any case, to answer your question:
Wireguard Zone:
- Allow forward to destination zones: LAN
- Allow forward from source zone: Empty *
LAN Zone:
- Allow forward to destination zones: (as it was)
- Allow forward from source zone: Wireguard
- Turn on masquarading
Save/apply then reboot.
* I should have noted before that this method should allow wireguard clients to see and connect to LAN resources, but will by design not allow LAN resources (except for the router itself) to initiate connections to wireguard clients. For me this is a security feature, but may not be what you want.
You do not need masquerading on the lan zone.
I was looking at that but didnt understand what he did. Tried to PM DmitryWorks but he did not answer to my question what he did exactly...
In the Wireguard -server- config file on the OpenWrt router,
sudo nano /etc/wireguard/wg0.conf
he added the (local) LAN IP subnet mask to the "AllowedIPs" entry for each [Peer] listed.
To add a subnet mask that covers all devices on the "192.168.1.1." network, add:
, 192.168.1.0/24
to the AllowedIPs= entry.
--
You stated above you were connecting into the wireguard server and could "see" the local 10... subnet: adding the local LAN subnet to the AllowedIPs entry should instruct Wireguard to allow the Peer to route to the LAN subnet / allow you access.