I don't know how you usually connect on an Octoprint. Maybe open a browser and type the IP?
Usually the way I access the webserver, I type in the pi's ip address. I did go and do that but it doesn't work 
You mentioned that internet works. Do other hosts in the lan work?
I suspect it is the firewall on Raspberry or some access list on the Octoprint.
I did try to ping to a sonoff but it couldn't connect ot it, kept saying the ip took too long to respond
--Edit--
Oh, I just attempted the ping again to the sonoff and it worked flawless this time, but can't ping to the pi
Are Rpi and Sonoff in the same subnet? If yes, then you should verify that Rpi is not blocking the incoming packets from different subnets.
I think they are in the same subnet, I don't recall creating a completely seperate one. However they are connected to different access points (I've created a 2.4 Ghz access point, a 2.4Gh guest access point, and a 5Ghz access point); which the pi is connected to the 5Ghz one and the sonoff connected to the 2.4 Ghz (non guest) access point. As a test, I went and tried a couple of different devices connected on each access point and noticed certain devices (such as computers) I can't ping to (though they may be in sleep mode, so they can't respond to the packages) but others like TVs and game systems I can ping to easily. So my guess at this point now is that it's the firewall on the pi
The access points are configured as shown
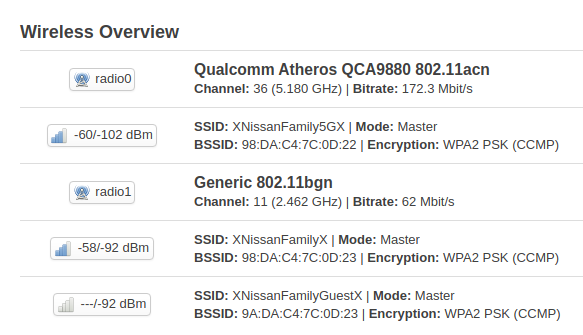
It is not that difficult, are they both in the lan or not? What are their IPs?
Ah, my mistake. They're both lan connections (but not connected to ethernet), starting with the 192.168.x.x address
Hey! I went and reset my pi entirely and now I can access the pi while connected to the VPN. So, now that I finally got that fixed, I'm back on trying to figure out how to isolate the VPN connection so that only the pi is visible to devices connected to the VPN. How would I be able to do this now that I don't have a seperate interface for the VPN connection?
Use this rule:
config rule
option src 'lan'
option family 'ipv4'
option dest 'lan'
list dest_ip '!10.0.0.1'
option target 'REJECT'
option name 'vpn to RPi'
list src_ip '192.168.8.0/24'
Change dest_ip with the IP of the RPi.
Thanks! It all seems to be working now. Um... one more question, is there a way to enforce password authentication on the connection? Just in case the certificates I'm using gets hijacked. I'm also wondering if I can make multiple clients for each device so I don't have to go sharing around the 1 client (which would decrease the likelihood of said certificates getting hijacked)
Erm... how do know which one to use?
If you don't know, use local.
Alrighty, so I'm trying to get the local authentication setup but how do I run sacli command on OpenWrt? It's not available on it
In general the methods to add user/pass authentication are in the form of plugins and scripts. The sacli is part of access server, but I am not sure if it is imported to OpenWrt. Since it is not documented you'll have to do some digging or live without it.
Ah ok, I was earlier trying to look for it but I hardly found anything on setting it up in general, so I'm just going to do without it. Also, when adding more clients.. do I need to create .ovpn client files for each one? Because I went and added some clients for my phone and laptop and then made .ovpn files; then imported and tried to connect to them. However when I tried to connect to them, my VPN logs on the router kept saying TLS error and that it couldn't find a certificate log for CN='the client's name for the device, e.g. myphone'.
You need to create the new client certificates and then run the client profile generator from the guide. This will read all certificates in the folder and create the configurations.
I tried it again, but it still keeps throwing back TLS errors
Tue Jun 2 13:18:59 2020 daemon.notice openvpn(server)[16262]: 166.137.218.90:57676 TLS: Initial packet from [AF_INET]166.137.218.90:57676, sid=746796c7 2e48ea0a
Tue Jun 2 13:19:00 2020 daemon.notice openvpn(server)[16262]: 166.137.218.90:57676 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=novag6
Tue Jun 2 13:19:00 2020 daemon.notice openvpn(server)[16262]: 166.137.218.90:57676 VERIFY WARNING: depth=1, unable to get certificate CRL: CN=Octoprint CA
Tue Jun 2 13:19:00 2020 daemon.err openvpn(server)[16262]: 166.137.218.90:57676 VERIFY ERROR: CRL not loaded
Tue Jun 2 13:19:00 2020 daemon.err openvpn(server)[16262]: 166.137.218.90:57676 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Tue Jun 2 13:19:00 2020 daemon.err openvpn(server)[16262]: 166.137.218.90:57676 TLS_ERROR: BIO read tls_read_plaintext error
Tue Jun 2 13:19:00 2020 daemon.err openvpn(server)[16262]: 166.137.218.90:57676 TLS Error: TLS object -> incoming plaintext read error
Tue Jun 2 13:19:00 2020 daemon.err openvpn(server)[16262]: 166.137.218.90:57676 TLS Error: TLS handshake failed
Tue Jun 2 13:19:00 2020 daemon.notice openvpn(server)[16262]: 166.137.218.90:57676 SIGUSR1[soft,tls-error] received, client-instance restarting
Paste here the commands you are using.