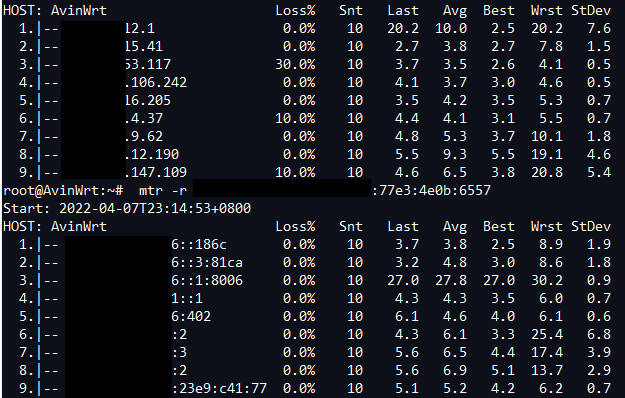
Hi there,
I have been using wireguard on a windows 10 PC to access a remote openwrt 21.02 snapshot router successfully with ipv4 for a while. Recently I used ipv6 address for the connection, and experienced frequent interruption. The phenomenon is a connected WG route suddenly "freeze" on all remote pages and ssh content, but if I do a reconnection then remote content can be displayed and updated again, a while later the "freeze" reappear.
Remote peer has public/native ipv4/v6 addresses, no NAT involved. My win10 PC dwells behind another openwrt router, which also has both native ipv4/v6 addresses but with different ISP, but I think the client side is irrelevant, no?
The firewall rule on the remote openwrt router is as below, WG listens on 65000 while 192.168.88.1 is remote router lan ip:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'WireGuard'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'WireGuard'
option src 'wan'
option dest_port '65000'
option target 'ACCEPT'
list proto 'udp'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option proto 'icmp'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type 'bad-header'
list icmp_type 'destination-unreachable'
list icmp_type 'echo-reply'
list icmp_type 'echo-request'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'unknown-header-type'
option dest '*'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option proto 'esp'
option target 'ACCEPT'
option dest 'lan'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option dest 'lan'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config redirect
option target 'DNAT'
option name 'WireGuard'
list proto 'udp'
option src 'wan'
option src_dport '65000'
option dest 'lan'
option dest_port '65000'
option dest_ip '192.168.88.1'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
If I use ipv4 address on remote access then this random "freeze/interruption" will gone. So can anyone tell me if I'm creating correct firewall rules? Or am I being QOSed by ISP specifically on IPV6 UDP? How can I have more log/detail about this freeze/interruption on the client's side? Thx in advance.