Hello everyone,
I'm new to all this and learning new stuff everyday so sorry If I missed something obvious
I have problem getting openvpn to work I followed this guide
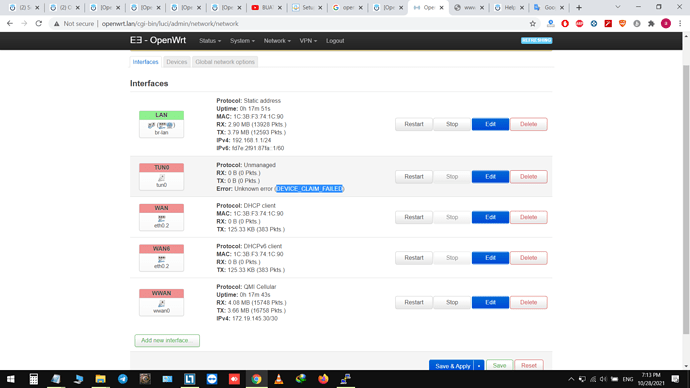
my router is tp-link MR6400v4 I did exactly same as the guide I can see in the log system that I established connection with my vpn server but still can't access internet I guess the problem is with step 4:
(At this point the VPN is set up and the router can use it, but devices in the LAN of your router won't be able to access the internet anymore, We need to set the VPN network interface as public by assigning VPN interface to WAN zone.)
when I turn the vpn off the internet works but when I turn it back on I have no connection !
PS: I tried the vpn on windows and it's working fine also there is no user/pass for it so I didn't edit it on openwrt
some troubleshooting
root@OpenWrt:~# uci show network;
network.loopback=interface
network.loopback.device='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd7e:2f91:87fa::/48'
network.@device[0]=device
network.@device[0].name='br-lan'
network.@device[0].type='bridge'
network.@device[0].ports='eth0.1'
network.lan=interface
network.lan.device='br-lan'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.wan=interface
network.wan.device='eth0.2'
network.wan.proto='dhcp'
network.wan6=interface
network.wan6.device='eth0.2'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='1 2 3 6t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='4 6t'
network.wwan=interface
network.wwan.proto='qmi'
network.wwan.device='/dev/cdc-wdm0'
network.wwan.modes='lte,umts'
network.wwan.apn='internet'
network.wwan.pdptype='ip4'
network.wwan.dhcp='0'
network.tun0=interface
network.tun0.proto='none'
network.tun0.device='tun0'
root@OpenWrt:~# uci show firewall;
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan' 'wan6' 'wwan' 'tun0'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].name='Support-UDP-Traceroute'
firewall.@rule[9].src='wan'
firewall.@rule[9].dest_port='33434:33689'
firewall.@rule[9].proto='udp'
firewall.@rule[9].family='ipv4'
firewall.@rule[9].target='REJECT'
firewall.@rule[9].enabled='false'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
root@OpenWrt:~#
root@OpenWrt:~# uci show openvpn
openvpn.custom_config=openvpn
openvpn.custom_config.config='/etc/openvpn/my-vpn.conf'
openvpn.sample_server=openvpn
openvpn.sample_server.port='1194'
openvpn.sample_server.proto='udp'
openvpn.sample_server.dev='tun'
openvpn.sample_server.ca='/etc/openvpn/ca.crt'
openvpn.sample_server.cert='/etc/openvpn/server.crt'
openvpn.sample_server.key='/etc/openvpn/server.key'
openvpn.sample_server.dh='/etc/openvpn/dh2048.pem'
openvpn.sample_server.server='10.8.0.0 255.255.255.0'
openvpn.sample_server.ifconfig_pool_persist='/tmp/ipp.txt'
openvpn.sample_server.keepalive='10 120'
openvpn.sample_server.persist_key='1'
openvpn.sample_server.persist_tun='1'
openvpn.sample_server.user='nobody'
openvpn.sample_server.status='/tmp/openvpn-status.log'
openvpn.sample_server.verb='3'
openvpn.sample_client=openvpn
openvpn.sample_client.client='1'
openvpn.sample_client.dev='tun'
openvpn.sample_client.proto='udp'
openvpn.sample_client.remote='my_server_1 1194'
openvpn.sample_client.resolv_retry='infinite'
openvpn.sample_client.nobind='1'
openvpn.sample_client.persist_key='1'
openvpn.sample_client.persist_tun='1'
openvpn.sample_client.user='nobody'
openvpn.sample_client.ca='/etc/openvpn/ca.crt'
openvpn.sample_client.cert='/etc/openvpn/client.crt'
openvpn.sample_client.key='/etc/openvpn/client.key'
openvpn.sample_client.verb='3'
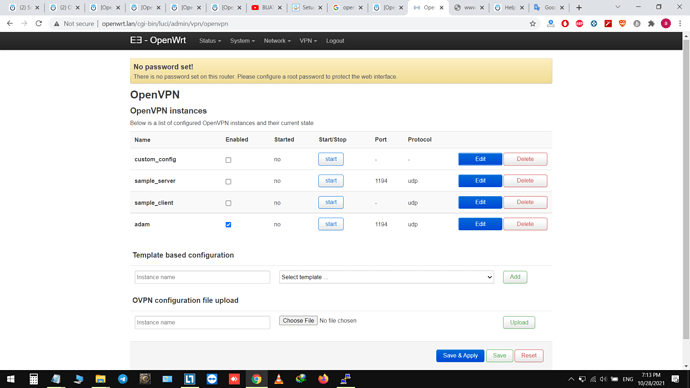
openvpn.adam=openvpn
openvpn.adam.config='/etc/openvpn/adam.ovpn'
openvpn.adam.enabled='1'
root@OpenWrt:~# pgrep -f -a openvpn
1934 /usr/sbin/openvpn --syslog openvpn(adam) --status /var/run/openvpn.adam.status --cd /etc/openvpn --config /etc/openvpn/adam.ovpn --up /usr/libexec/openvpn-hotplug up adam --down /usr/libexec/openvpn-hotplug down adam --script-security 2
system log:
Fri Oct 29 00:55:17 2021 daemon.notice netifd: Interface 'lan' is now up
Fri Oct 29 00:55:17 2021 daemon.notice netifd: bridge 'br-lan' link is up
Fri Oct 29 00:55:17 2021 daemon.notice netifd: Interface 'lan' has link connectivity
Fri Oct 29 00:55:17 2021 daemon.notice netifd: VLAN 'eth0.1' link is up
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'loopback' is enabled
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'loopback' is setting up now
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'loopback' is now up
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'wan' is enabled
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'wan6' is enabled
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'wwan' is setting up now
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Network device 'eth0' link is up
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Network device 'lo' link is up
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'loopback' has link connectivity
Fri Oct 29 00:55:18 2021 daemon.notice netifd: VLAN 'eth0.2' link is up
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'wan' has link connectivity
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'wan' is setting up now
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'wan6' has link connectivity
Fri Oct 29 00:55:18 2021 daemon.notice netifd: Interface 'wan6' is setting up now
Fri Oct 29 00:55:18 2021 kern.info kernel: [ 41.063423] IPv6: ADDRCONF(NETDEV_CHANGE): br-lan: link becomes ready
Fri Oct 29 00:55:19 2021 daemon.err odhcpd[1556]: Failed to send to ff02::1%lan@br-lan (Address not available)
Fri Oct 29 00:55:19 2021 daemon.notice netifd: wan (2135): udhcpc: started, v1.33.1
Fri Oct 29 00:55:20 2021 user.notice firewall: Reloading firewall due to ifup of lan (br-lan)
Fri Oct 29 00:55:20 2021 daemon.notice procd: /etc/rc.d/S96led: setting up led lan
Fri Oct 29 00:55:22 2021 daemon.notice netifd: wan (2135): udhcpc: sending discover
Fri Oct 29 00:55:22 2021 daemon.notice netifd: wwan (2009): Waiting for SIM initialization
Fri Oct 29 00:55:23 2021 daemon.notice netifd: wwan (2009): Device does not support 802.3 mode. Informing driver of raw-ip only for wwan0 ..
Fri Oct 29 00:55:23 2021 daemon.notice hostapd: Configuration file: /var/run/hostapd-phy0.conf (phy wlan0) --> new PHY
Fri Oct 29 00:55:23 2021 daemon.warn openvpn(adam)[1934]: Unrecognized option or missing or extra parameter(s) in /etc/openvpn/adam.ovpn:19: block-outside-dns (2.5.3)
Fri Oct 29 00:55:23 2021 kern.info kernel: [ 46.303492] br-lan: port 2(wlan0) entered blocking state
Fri Oct 29 00:55:23 2021 kern.info kernel: [ 46.308980] br-lan: port 2(wlan0) entered disabled state
Fri Oct 29 00:55:23 2021 kern.info kernel: [ 46.314868] device wlan0 entered promiscuous mode
Fri Oct 29 00:55:23 2021 daemon.notice hostapd: wlan0: interface state UNINITIALIZED->HT_SCAN
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: OpenVPN 2.5.3 mipsel-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: library versions: OpenSSL 1.1.1l 24 Aug 2021, LZO 2.10
Fri Oct 29 00:55:23 2021 daemon.notice netifd: wwan (2009): Waiting for network registration
Fri Oct 29 00:55:23 2021 daemon.warn openvpn(adam)[1934]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: TCP/UDP: Preserving recently used remote address: [AF_INET]139.162.134.125:1194
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: Socket Buffers: R=[180224->180224] S=[180224->180224]
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: UDP link local: (not bound)
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: UDP link remote: [AF_INET]139.162.134.125:1194
Fri Oct 29 00:55:23 2021 daemon.err openvpn(adam)[1934]: write UDP: Network unreachable (code=128)
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: Network unreachable, restarting
Fri Oct 29 00:55:23 2021 daemon.notice openvpn(adam)[1934]: SIGUSR1[soft,network-unreachable] received, process restarting
Fri Oct 29 00:55:24 2021 daemon.notice openvpn(adam)[1934]: Restart pause, 5 second(s)
Fri Oct 29 00:55:24 2021 daemon.info procd: - init complete -
Fri Oct 29 00:55:25 2021 daemon.notice netifd: wwan (2009): Starting network wwan
Fri Oct 29 00:55:25 2021 daemon.notice hostapd: 20/40 MHz operation not permitted on channel pri=11 sec=7 based on overlapping BSSes
Fri Oct 29 00:55:25 2021 kern.info kernel: [ 48.117827] IPv6: ADDRCONF(NETDEV_CHANGE): wlan0: link becomes ready
Fri Oct 29 00:55:25 2021 kern.info kernel: [ 48.124724] br-lan: port 2(wlan0) entered blocking state
Fri Oct 29 00:55:25 2021 kern.info kernel: [ 48.130201] br-lan: port 2(wlan0) entered forwarding state
Fri Oct 29 00:55:25 2021 daemon.notice netifd: Network device 'wlan0' link is up
Fri Oct 29 00:55:25 2021 daemon.notice hostapd: wlan0: interface state HT_SCAN->ENABLED
Fri Oct 29 00:55:25 2021 daemon.notice hostapd: wlan0: AP-ENABLED
Fri Oct 29 00:55:25 2021 daemon.notice netifd: wan (2135): udhcpc: sending discover
Fri Oct 29 00:55:25 2021 daemon.notice netifd: wwan (2009): Setting up wwan0
Fri Oct 29 00:55:25 2021 daemon.notice netifd: Interface 'wwan' is now up
Fri Oct 29 00:55:25 2021 daemon.notice netifd: Network device 'wwan0' link is up
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: reading /tmp/resolv.conf.d/resolv.conf.auto
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using only locally-known addresses for domain test
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using only locally-known addresses for domain onion
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using only locally-known addresses for domain localhost
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using only locally-known addresses for domain local
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using only locally-known addresses for domain invalid
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using only locally-known addresses for domain bind
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using only locally-known addresses for domain lan
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using nameserver 41.208.116.8#53
Fri Oct 29 00:55:25 2021 daemon.info dnsmasq[1152]: using nameserver 62.68.42.2#53
Fri Oct 29 00:55:25 2021 user.notice firewall: Reloading firewall due to ifup of wwan (wwan0)
Fri Oct 29 00:55:26 2021 user.notice firewall: Reloading firewall due to ifupdate of wwan (wwan0)
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[1152]: exiting on receipt of SIGTERM
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: Connected to system UBus
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: started, version 2.85 cachesize 150
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: DNS service limited to local subnets
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-cryptohash no-DNSSEC no-ID loop-detect inotify dumpfile
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: UBus support enabled: connected to system bus
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq-dhcp[2675]: DHCP, IP range 192.168.1.100 -- 192.168.1.249, lease time 12h
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain test
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain onion
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain localhost
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain local
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain invalid
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain bind
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain lan
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: reading /tmp/resolv.conf.d/resolv.conf.auto
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain test
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain onion
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain localhost
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain local
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain invalid
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain bind
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using only locally-known addresses for domain lan
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using nameserver 41.208.116.8#53
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: using nameserver 62.68.42.2#53
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: read /etc/hosts - 4 addresses
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq-dhcp[2675]: read /etc/ethers - 0 addresses
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: read /etc/hosts - 4 addresses
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq[2675]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Fri Oct 29 00:55:27 2021 daemon.info dnsmasq-dhcp[2675]: read /etc/ethers - 0 addresses
Fri Oct 29 00:55:28 2021 daemon.notice netifd: wan (2135): udhcpc: sending discover
Fri Oct 29 00:55:29 2021 daemon.warn openvpn(adam)[1934]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: TCP/UDP: Preserving recently used remote address: [AF_INET]139.162.134.125:1194
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Socket Buffers: R=[180224->180224] S=[180224->180224]
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: UDP link local: (not bound)
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: UDP link remote: [AF_INET]139.162.134.125:1194
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: TLS: Initial packet from [AF_INET]139.162.134.125:1194, sid=d8fb54b4 ccb837e3
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: VERIFY OK: depth=1, CN=cn_eAvCYRG1pJmIXU67
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: VERIFY KU OK
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Validating certificate extended key usage
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: VERIFY EKU OK
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: VERIFY X509NAME OK: CN=server_BxOk3f00AMYT6nJk
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: VERIFY OK: depth=0, CN=server_BxOk3f00AMYT6nJk
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 256 bit EC, curve prime256v1, signature: ecdsa-with-SHA256
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: [server_BxOk3f00AMYT6nJk] Peer Connection Initiated with [AF_INET]139.162.134.125:1194
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: PUSH: Received control message: 'PUSH_REPLY,dhcp-option DNS 1.0.0.1,dhcp-option DNS 1.1.1.1,redirect-gateway def1 bypass-dhcp,tun-ipv6,route-ipv6 2000::/3,redirect-gateway ipv6,tun-ipv6,route-gateway 10.8.0.1,topology subnet,ping 10,ping-restart 120,ifconfig-ipv6 fd42:42:42:42::2/112 fd42:42:42:42::1,ifconfig 10.8.0.2 255.255.255.0,peer-id 0,cipher AES-128-GCM'
Fri Oct 29 00:55:29 2021 daemon.warn openvpn(adam)[1934]: WARNING: You have specified redirect-gateway and redirect-private at the same time (or the same option multiple times). This is not well supported and may lead to unexpected results
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: OPTIONS IMPORT: timers and/or timeouts modified
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: OPTIONS IMPORT: --ifconfig/up options modified
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: OPTIONS IMPORT: route options modified
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: OPTIONS IMPORT: route-related options modified
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: OPTIONS IMPORT: peer-id set
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: OPTIONS IMPORT: adjusting link_mtu to 1624
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: OPTIONS IMPORT: data channel crypto options modified
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v4_best_gw query: dst 0.0.0.0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v4_best_gw result: via 172.19.145.29 dev wwan0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: GDG6: remote_host_ipv6=n/a
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v6_best_gw query: dst ::
Fri Oct 29 00:55:29 2021 daemon.warn openvpn(adam)[1934]: sitnl_send: rtnl: generic error (-13): Permission denied
Fri Oct 29 00:55:29 2021 daemon.notice netifd: Interface 'tun0' is enabled
Fri Oct 29 00:55:29 2021 daemon.notice netifd: Network device 'tun0' link is up
Fri Oct 29 00:55:29 2021 daemon.notice netifd: Interface 'tun0' has link connectivity
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: TUN/TAP device tun0 opened
Fri Oct 29 00:55:29 2021 daemon.notice netifd: Interface 'tun0' is setting up now
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_iface_mtu_set: mtu 1500 for tun0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_iface_up: set tun0 up
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_addr_v4_add: 10.8.0.2/24 dev tun0
Fri Oct 29 00:55:29 2021 daemon.notice netifd: Interface 'tun0' is now up
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_iface_mtu_set: mtu 1500 for tun0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_iface_up: set tun0 up
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_addr_v6_add: fd42:42:42:42::2/112 dev tun0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: /usr/libexec/openvpn-hotplug up adam tun0 1500 1624 10.8.0.2 255.255.255.0 init
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v4_add: 139.162.134.125/32 via 172.19.145.29 dev [NULL] table 0 metric -1
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v4_add: 0.0.0.0/1 via 10.8.0.1 dev [NULL] table 0 metric -1
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v4_add: 128.0.0.0/1 via 10.8.0.1 dev [NULL] table 0 metric -1
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: add_route_ipv6(2000::/3 -> fd42:42:42:42::1 metric -1) dev tun0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v6_add: 2000::/3 via :: dev tun0 table 0 metric -1
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: add_route_ipv6(::/3 -> fd42:42:42:42::1 metric -1) dev tun0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v6_add: ::/3 via :: dev tun0 table 0 metric -1
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: add_route_ipv6(2000::/4 -> fd42:42:42:42::1 metric -1) dev tun0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v6_add: 2000::/4 via :: dev tun0 table 0 metric -1
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: add_route_ipv6(3000::/4 -> fd42:42:42:42::1 metric -1) dev tun0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v6_add: 3000::/4 via :: dev tun0 table 0 metric -1
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: add_route_ipv6(fc00::/7 -> fd42:42:42:42::1 metric -1) dev tun0
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: net_route_v6_add: fc00::/7 via :: dev tun0 table 0 metric -1
Fri Oct 29 00:55:29 2021 daemon.notice openvpn(adam)[1934]: Initialization Sequence Completed
Fri Oct 29 00:55:30 2021 user.notice firewall: Reloading firewall due to ifup of tun0 (tun0)
Fri Oct 29 00:56:36 2021 daemon.info hostapd: wlan0: STA 30:d1:6b:97:b3:c9 IEEE 802.11: authenticated
Fri Oct 29 00:56:36 2021 daemon.info hostapd: wlan0: STA 30:d1:6b:97:b3:c9 IEEE 802.11: associated (aid 1)
Fri Oct 29 00:56:36 2021 daemon.notice hostapd: wlan0: AP-STA-CONNECTED 30:d1:6b:97:b3:c9
Fri Oct 29 00:56:36 2021 daemon.info dnsmasq-dhcp[2675]: DHCPREQUEST(br-lan) 192.168.1.125 30:d1:6b:97:b3:c9
Fri Oct 29 00:56:36 2021 daemon.info dnsmasq-dhcp[2675]: DHCPACK(br-lan) 192.168.1.125 30:d1:6b:97:b3:c9 LAPTOP-OA5A3HBT
Fri Oct 29 00:56:40 2021 authpriv.info dropbear[2936]: Child connection from 192.168.1.125:64865
Fri Oct 29 00:56:42 2021 authpriv.notice dropbear[2936]: Auth succeeded with blank password for 'root' from 192.168.1.125:64865
Fri Oct 29 00:56:45 2021 daemon.info dnsmasq[2675]: read /etc/hosts - 4 addresses
Fri Oct 29 00:56:45 2021 daemon.info dnsmasq[2675]: read /tmp/hosts/odhcpd - 0 addresses
Fri Oct 29 00:56:45 2021 daemon.info dnsmasq[2675]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Fri Oct 29 00:56:45 2021 daemon.info dnsmasq-dhcp[2675]: read /etc/ethers - 0 addresses
Fri Oct 29 00:56:46 2021 daemon.info dnsmasq[2675]: read /etc/hosts - 4 addresses
Fri Oct 29 00:56:46 2021 daemon.info dnsmasq[2675]: read /tmp/hosts/odhcpd - 1 addresses
Fri Oct 29 00:56:46 2021 daemon.info dnsmasq[2675]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Fri Oct 29 00:56:46 2021 daemon.info dnsmasq-dhcp[2675]: read /etc/ethers - 0 addresses
Fri Oct 29 00:56:50 2021 daemon.err uhttpd[1670]: luci: accepted login on / for root from 192.168.1.125