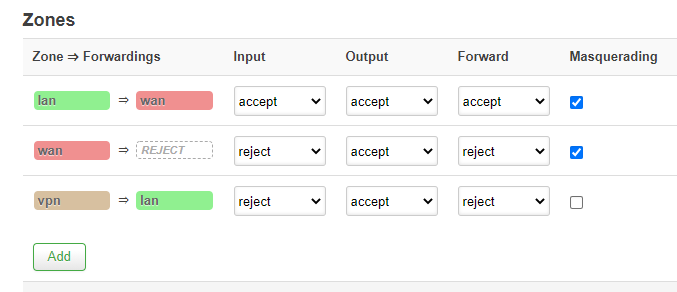
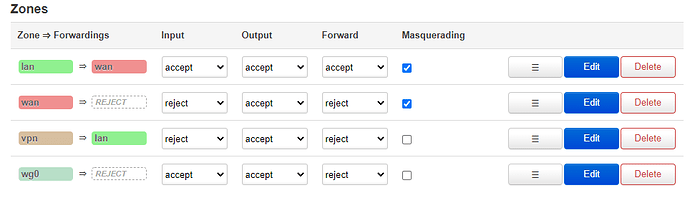
After doing this, the vpn=>lan has changed to: (as we have done "allow forward from sources zones: vpn").
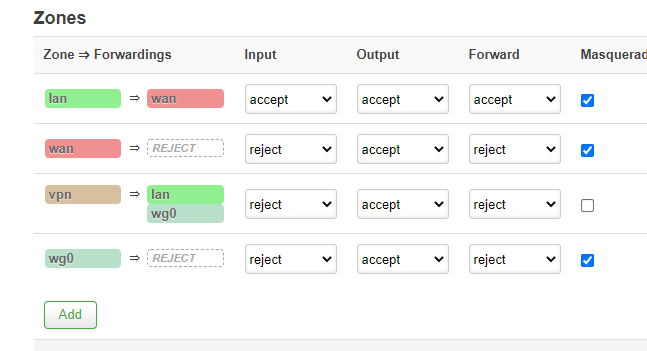
I have removed lan from here-
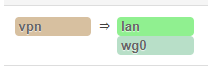
If I remove it, I can put masquerading and mss clampling.
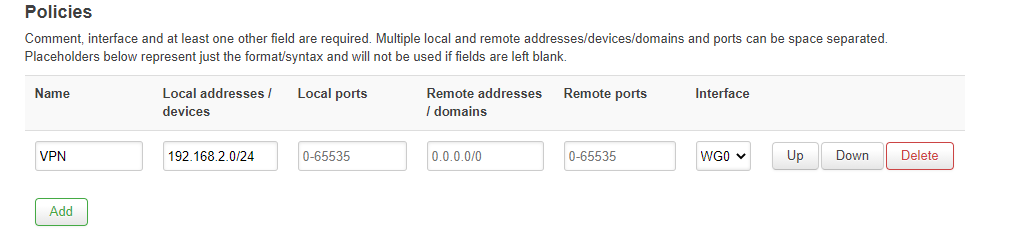
So I have checked this:
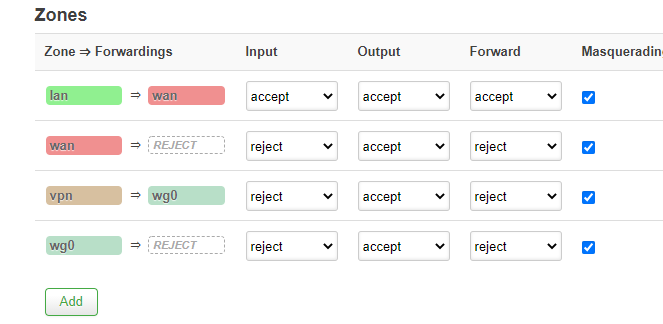
Do I configure it well?
I connected my laptop to WIFI_VPN, it says no access to internet.
Pings:
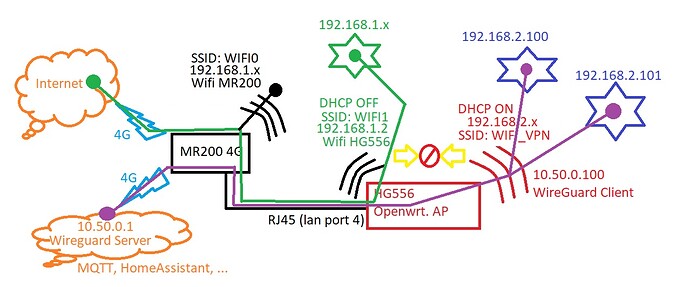
192.168.1.1 bad
192.168.1.2 ok (probably because of the new trafic rule)
192.168.2.1 ok (probably because of the new trafic rule)
10.50.0.100 ok
10.50.0.1 ok
Great !! Now I can ping to my server with 10.50.0.1.
I understand that it is ok, I could send "packets" directly to my server. I don't have an IP like 10.50.0.x because I am behind my openwrt router.
Is that way good, or do I have to do exactly what you said (first image, vpn => lan&wg0) ?
But now I have a doubt: from my laptop I can't tracert openwrt.org (for example) as I don't have any DNS configured. I can't also see my public ip address to confirm that it is the ip of my cloud server. This is to confirm that I am "inside the tunnel". I have tried to tracert 8.8.8.8, but not luck:
1 2 ms 3 ms 3 ms OpenWrt.lan [192.168.2.1]
2 * * * Tiempo de espera agotado para esta solicitud.
How could I check if I am really in tunnel?
What is the real reason because of I haven't got internet access trought WG0 ? is it because any configuration in server side (I am thinkg that I am reaching my server but it can't "foward" to internet?), or in openwrt client side? (Today is not very important, but as I am going to use some devices that sometimes nees update from internet, it will be great to know the reason, so I could activate/deactive the trafic rule or firewall zone or whatever to update my devices. Is the problem server side? or cliente side? Probably I could solve it by joining again VPN=>LAN, but I prefer to understand where the problem could be.
Probably next days I will ask you about traffic rules, as I am going to try to comunicate with my 10.50.0.1 sever with different ports (MQTT, ...). Probably all of they works, so no more questions.
After that, I will try "the other points not very important" that I said some post above, and try to write steps.
Thanks a lot @vgaetera, you have helped me a lot. Much more than anyone could expect. What about these last questions?
Thanks a lot again.



 .
.