Hi everybody,
As a software developer and an electronic hobbyist, I am working on my own door access system.
This is going pretty well and I could already implement most of the required parts, but I am facing a last challenge: the network.
This is a critical part of the security of my system and I need to make sure it is properly configured. However, my knowledge in the subject is quite limited. I tried to document myself as much as possible on internet but I cannot get the whole picture right and I don't want to invest some money in the wrong hardware.
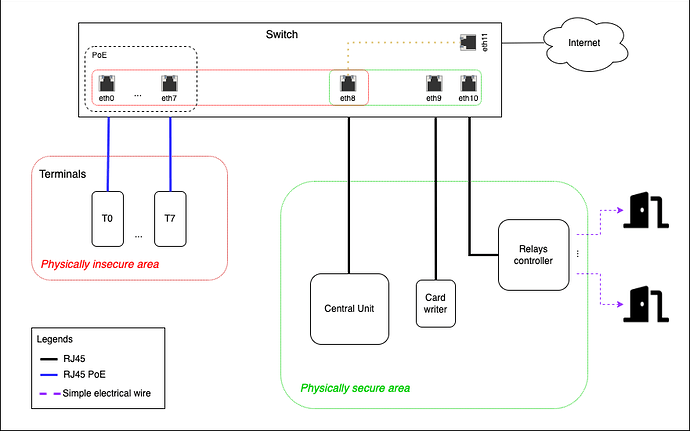
Here is a schema of my system:
Terminals are esp32 microcontrollers (more precisely wESP32 modules) that read RFID tags (Mifare Desfire EV1) containing a secret and sending it to a central unit that does all the authorisation/validity checks and sends an HTTP request to a relays controller to actually open the doors. The central unit can also communicate through HTTPS to a NFC device to configure the NFC cards.
Terminals are outside the building and thus highly insecure, but the rest is all in a secure room.
The communication between the central unit and the relays is insecure (the device I am using doesn't handle SSL) and thus it is very important that one cannot just plug its laptop instead of the terminal and send a command to open the door to the relays controller... This would defeat the whole purpose of my system... I thus want that terminals see as less as possible and can only communicate on port 443 with the central unit and doesn't see any other traffic (not even the one of other terminals).
I would then need to find a switch with at least 8 PoE outputs, 3 normal ones and one for internet. And I would need to be able to define rules in the switch to ensure that:
- eth0..7 can only communicate with eth8 (and not between each other) on port 443
- eth9 can only communicate with eth8 on port 443
- eth10 can only communicate with eth8 on port 80
- Only eth8 can access internet on eth11
Would someone have hints of which hardware I could use to fulfil my requirements ? And how to define the firewall rules I need ?
Thanks a lot in advance for your precious help.