In OpenWRT Luci, you can set up your router to use the OpenVPN client with NordVPN in 5 easy steps.
1/ install required packages
System > Software
- openvpn-openssl
- luci-app-openvpn
- ip-full
2/ upload .opvn file and complete configuration
VPN > OpenVPN
- choose Instance name under OVPN configuration file upload
- download NordVPN config here or here
- Choose File, pick up .opvn file obtained above
- Upload
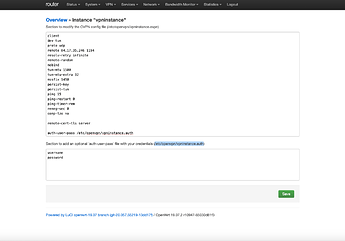
- Edit newly created instance
- add username and password in bottom box (personal NordVPN username and password, username and password need to be on separate lines)
- copy location of file containing username and password (line right above bottom box, ex:
/etc/openvpn/vpninstance.auth) - in top box, find line that says
auth-user-passand paste location next to it. Include space before (ex:auth-user-pass /etc/openvpn/vpninstance.auth) - Save
3/ create new network interface
Network > Interfaces
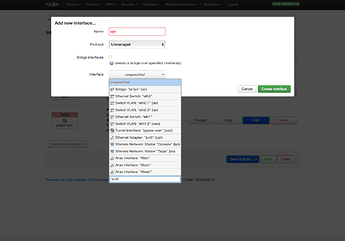
- Add new interface
- name it (ex: vpn)
- set Protocol to Unmanaged
- under Interface, type
tun0in custom box (very last option of drop down list) and hit enter - Create interface
4/ create new firewall zone for interface
Network > Firewall
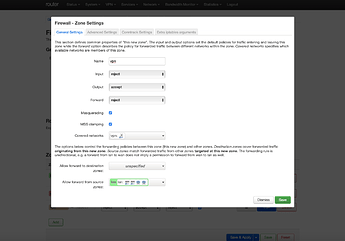
- Add zone
- name it (ex: vpn)
- set Input to reject, Output to accept and Forward to reject
- tick Masquerading
- tick MSS clamping
- under Covered networks, select interface created in 3/
- under Allow forward from source zones, select lan
5/ set DNS servers
Network > Interfaces
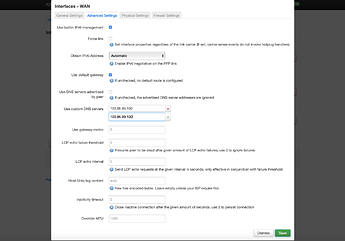
- edit WAN
- under Advanced Settings, untick box for Use DNS servers advertised by peer
- in Use custom DNS servers add 2 DNS servers supplied by NordVPN (103.86.96.100 and 103.86.99.100 as of today)
- Save
Finally, VPN > OpenVPN
- in Enabled column, tick box for OpenVPN instance created
- Save & Apply
- if VPN client hasn't started yet, press start