Yes, my WAN interface has a public IPv4 address. It's the same IP assigned to my laptop I use to manage the network.
Good news to report, I've created the vLan7 interface and my entire network didn't go down.
I changed my IPv4 gateway address to the wan IPv4 recommended by LuCi, which was my wan public ip address with the last octet being 1. I'm new to networking still, so it didn't quite click that my gateway shouldn't be a random IP address if I want the vLan traffic to actaully connect to the internet via a gateway.
Now the network doesn't go down, but the wired connection from port 7 in my switch doesn't deliver internet to the end user device.
Also here are the results from running the command you posted above, now with the vLan7 interface on my network:
BusyBox v1.31.1 () built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt SFE, r13152-5019a06fc1
-----------------------------------------------------
root@OpenWrt:~# uci export network; uci export wireless; \
> uci export dhcp; uci export firewall; \
> head -n -0 /etc/firewall.user; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru;
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc7:5059:d813::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'REDACTED'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2 3 4'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 5t'
option vid '7'
config interface 'vLan7'
option proto 'static'
option ifname 'eth0.7'
option ipaddr '192.168.7.3'
option netmask '255.255.255.0'
option gateway 'X.X.X.1'
option broadcast '192.168.7.255'
list dns '8.8.8.8'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt 5GHz'
option encryption 'psk2'
option key REDACTED
option ieee80211w '1'
option ieee80211w_max_timeout '1000'
option ieee80211w_retry_timeout '201'
option wpa_disable_eapol_key_retries '1'
config wifi-device 'radio1'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
option disabled '1'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'vLan7'
option interface 'vLan7'
option start '100'
option limit '150'
option leasetime '12h'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option forward 'REJECT'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vLan7'
option network 'vLan7'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'vLan7'
option dest 'wan'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
11: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet X.X.X.195/24 brd X.X.X.255 scope global eth0.2
valid_lft forever preferred_lft forever
34: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
37: eth0.7@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.7.3/24 brd 192.168.7.255 scope global eth0.7
valid_lft forever preferred_lft forever
default via X.X.X.1 dev eth0.2 proto static src X.X.X.195
X.X.X.0/24 dev eth0.2 proto kernel scope link src X.X.X.195
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.7.0/24 dev eth0.7 proto kernel scope link src 192.168.7.3
broadcast X.X.X.0 dev eth0.2 table local proto kernel scope link src X.X.X.195
local X.X.X.195 dev eth0.2 table local proto kernel scope host src X.X.X.195
broadcast X.X.X.255 dev eth0.2 table local proto kernel scope link src X.X.X.195
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
broadcast 192.168.7.0 dev eth0.7 table local proto kernel scope link src 192.168.7.3
local 192.168.7.3 dev eth0.7 table local proto kernel scope host src 192.168.7.3
broadcast 192.168.7.255 dev eth0.7 table local proto kernel scope link src 192.168.7.3
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
Change vLan7 to
config interface 'vLan7'
option proto 'static'
option ifname 'eth0.7'
option ipaddr '192.168.7.3'
option netmask '255.255.255.0'
I went into /etc/config/ and edited the network interface vLan 7 so it now has the ip address 192.168.7.3 and the 255.255.255.0 netmask and removed the gateway and broadcast and reset the vLan 7 network.
Unfortunately the device still does not receive internet over ethernet cable. Am I missing something simple like a lan or wan reset? Or possibly plugging the ethernet in and out the router or switch?
Your continued support is appreciated, if you could advise again that would be greatly appreciated. Thank you.
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc7:5059:d813::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'REDACTED'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2 3 4'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 5t'
option vid '7'
config interface 'vLan7'
option proto 'static'
option ifname 'eth0.7'
option ipaddr '192.168.7.3'
option netmask '255.255.255.0'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt 5GHz'
option encryption 'psk2'
option key 'REDACTED'
option ieee80211w '1'
option ieee80211w_max_timeout '1000'
option ieee80211w_retry_timeout '201'
option wpa_disable_eapol_key_retries '1'
config wifi-device 'radio1'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
option disabled '1'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'vLan7'
option interface 'vLan7'
option start '100'
option limit '150'
option leasetime '12h'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option forward 'REJECT'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vLan7'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'vLan7'
option dest 'wan'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
11: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet X.X.X.195/24 brd X.X.X.255 scope global eth0.2
valid_lft forever preferred_lft forever
34: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
41: eth0.7@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.7.3/24 brd 192.168.7.255 scope global eth0.7
valid_lft forever preferred_lft forever
default via X.X.X.1 dev eth0.2 proto static src X.X.X.195
X.X.X.0/24 dev eth0.2 proto kernel scope link src X.X.X.195
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.7.0/24 dev eth0.7 proto kernel scope link src 192.168.7.3
broadcast X.X.X.0 dev eth0.2 table local proto kernel scope link src X.X.X.195
local X.X.X.195 dev eth0.2 table local proto kernel scope host src X.X.X2.195
broadcast X.X.X.255 dev eth0.2 table local proto kernel scope link src X.X.X.195
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
broadcast 192.168.7.0 dev eth0.7 table local proto kernel scope link src 192.168.7.3
local 192.168.7.3 dev eth0.7 table local proto kernel scope host src 192.168.7.3
broadcast 192.168.7.255 dev eth0.7 table local proto kernel scope link src 192.168.7.3
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
Add list dhcp_option '6,192.168.1.1' to the DHCP config for vLan7.
I've added the additional DHCP option of 6,192.168.1.1 , the end device is still not receiving an internet connection.
I was looking at a thread from someone who wants the same set up and is experiencing the same issues as me, No internet with VLANs, something I noticed was in their vLan config interfaces, the had an option type 'bridge' included in the config. I did some reading and bridging vlans can help them discover the topology of the network, but am not sure if it is needed in my instanced.
Here are the vLan7 details from the network output:
config interface 'vLan7'
option proto 'static'
option ifname 'eth0.7'
option ipaddr '192.168.7.3'
option netmask '255.255.255.0'
config dhcp 'vLan7'
option interface 'vLan7'
option start '100'
option limit '150'
option leasetime '12h'
list dhcp_option '6,192.168.1.1'
config zone
option name 'vLan7'
option network 'vLan7'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'vLan7'
option dest 'wan'
Is there anything else you could recommend? Thanks for all the support thus far.
Has the end device got an IP in the correct subnet? Double check the firewall zones and forwardings on the router.
Did some troubleshooting, and found that the ports on my router are labeled in reverse from the the port labels in LuCi. Fixed this and created new switch settings, a new interface and firewall. Sorry for this basic mix up, but it's fixed now. Now my switch delivers internet to non vLan connections.
Unfortunately, my end user device on my vLan is still not connecting to the internet?
On the target device, I set the ip configuration to manual and entered the details below. For the gateway, should I be putting the same IP that my WAN has, even with the same ending octet? The IP address I assigned is within the subnet I gave and within the /24 convention.
Thank you.
If the vlan is working correctly you should be able to use DHCP. If not then there's still an issue somewhere.
I am able to connect with DHCP, so that looks good! But my internal IPv4 is on the 192.168.1.X subnet, if I created the vLan with the 192.168.7.X subnet, shouldn't the device's internal IP be 192.168.7.X?
Thank you for all your help Krazeh!
can you post your latest config files (network. DHCP, firewall)?
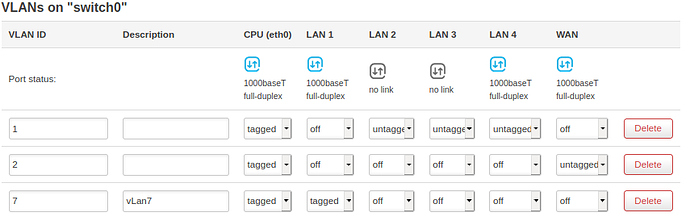
I assume the end device is plugged into the correct port on the switch? Make sure the switch port is only used by vlan 7.
Yes, the device is plugged in on the correct port on the switch. Edited the switch such that port 7 is only used by vlan7.
The router switch settings:
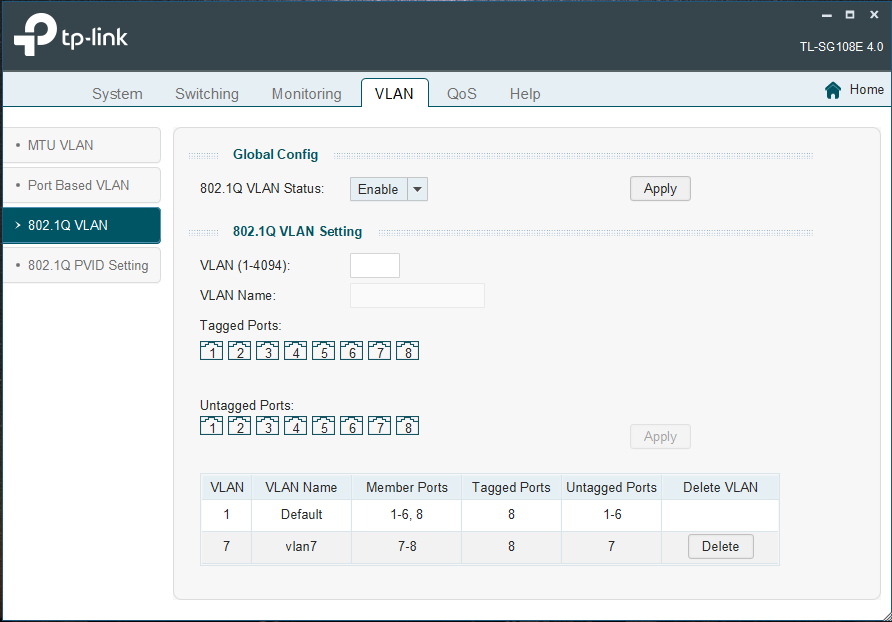
The switch 802.1Q Vlan settings:
The vlan7 interface:
(Not sure if I should have bridge interfaces checked in the physical settings?)
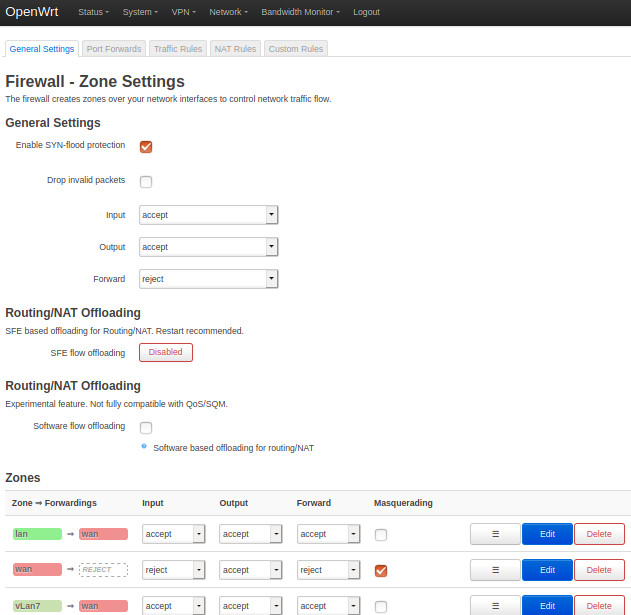
The firewall settings:
In the wan fw settings, Allow forward from source zones has lan and vlan7.
In the vlan7 fw settings, the allow forward to destinations is set to wan.
Yes, here is my latest configuration.
Thank you.
BusyBox v1.31.1 () built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt SFE, r13152-5019a06fc1
-----------------------------------------------------
root@OpenWrt:~# uci export network; uci export wireless; \
> uci export dhcp; uci export firewall; \
> head -n -0 /etc/firewall.user; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru;
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd8:ca6b:447b::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'REDACTED'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 3 4 5'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option description 'vLan7'
option vid '7'
option ports '0t 2t'
config interface 'vLan7'
option proto 'static'
option ifname 'eth0.7'
option netmask '255.255.255.0'
option ipaddr '192.168.7.1'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 2t'
option vid '6'
option description 'Vlan6'
config interface 'vLan6'
option proto 'static'
option ifname 'eth0.6'
option ipaddr '192.168.6.1'
option netmask '255.255.255.0'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option encryption 'psk2'
option key 'REDACTED'
option ssid 'OpenWrt 5GHz'
config wifi-device 'radio1'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'psk2'
option key 'REDACTED'
option disabled '1'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'vLan7'
option interface 'vLan7'
option start '100'
option limit '150'
option leasetime '12h'
list dhcp_option '6,192.168.1.1'
config dhcp 'vLan6'
option interface 'vLan6'
option start '100'
option limit '150'
option leasetime '12h'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vLan7'
option network 'vLan7'
option output 'ACCEPT'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'vLan7'
option dest 'wan'
config zone
option name 'vLan6'
option network 'vLan6'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'vLan6'
option dest 'wan'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
11: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet X.X.X.250/24 brd X.X.X.255 scope global eth0.2
valid_lft forever preferred_lft forever
24: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
27: eth0.7@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.7.1/24 brd 192.168.7.255 scope global eth0.7
valid_lft forever preferred_lft forever
28: eth0.6@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.6.1/24 brd 192.168.6.255 scope global eth0.6
valid_lft forever preferred_lft forever
default via X.X.X.1 dev eth0.2 proto static src X.X.X.250
X.X.X.0/24 dev eth0.2 proto kernel scope link src X.X.X.250
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.6.0/24 dev eth0.6 proto kernel scope link src 192.168.6.1
192.168.7.0/24 dev eth0.7 proto kernel scope link src 192.168.7.1
broadcast X.X.X.0 dev eth0.2 table local proto kernel scope link src X.X.X.250
local X.X.X.250 dev eth0.2 table local proto kernel scope host src X.X.X.250
broadcast X.X.X.255 dev eth0.2 table local proto kernel scope link src X.X.X.250
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
broadcast 192.168.6.0 dev eth0.6 table local proto kernel scope link src 192.168.6.1
local 192.168.6.1 dev eth0.6 table local proto kernel scope host src 192.168.6.1
broadcast 192.168.6.255 dev eth0.6 table local proto kernel scope link src 192.168.6.1
broadcast 192.168.7.0 dev eth0.7 table local proto kernel scope link src 192.168.7.1
local 192.168.7.1 dev eth0.7 table local proto kernel scope host src 192.168.7.1
broadcast 192.168.7.255 dev eth0.7 table local proto kernel scope link src 192.168.7.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
Looks good from what I can tell. Both vlan 6 and 7 are tagged - which is fine since they are trimmed to your external switch.
To eliminate the external switch as a possible issue, try making one of the VLANs untagged on the openwrt switch port (logical port 2) and then plug a computer directly into that port. see if it gets an IP and has internet access. The repeat with the other vlan. Once those are verified, tag both again and look at the switch configuration again.
I followed these steps and the device has an IPv4 address 192.168.1.X inside the lan interface, but there is no internet access. So as of now it appears the issue is not with the switch.
I'm glad you brought the switch up, because it is a switch that supports 802.1Q vlans but technically it is labeled as an unmanaged switch. I read through the vlan documentation provided by the switch manufacturer, and the process of setting up vlans recommended by them is much different? Not sure if it is of value, but here is their guide: https://www.tp-link.com/us/support/faq/788/
If you are getting an address on the 192.168.1.0/24 network, that is your default LAN (not one of the VLANs) -- if you are not getting internet access from on that network, you might want to figure out what is going on (your VLANs also probably won't have internet). It is possible you'll want to reset to defaults to get a working config again and then go from there if nothing appears to work...
- what do you see for the rest of the DHCP supplied address info on one of your client devices (IP address, subnet, gateway/router, dns)?
- If you try the experiment I suggested above (untagging one VLAN or the other), what do you get for the
- Do you have a proper WAN address on your OpenWrt router?
- If you ssh into the router and issue a ping to 8.8.8.8 -- do you get a response? What about google.com? (you can also do this from the Network > Diagnostics page on LuCI).
Yeah, I really hate that they did this. The switches used to be labeled as part of the "Gigabit Easy Smart Switch" series devices... then they renamed them as "Unmanaged Pro" switches. I get that there is a distinction between a smart switch (VLAN aware) and a fully managed switch, but using the term "unmanaged" implies that it is not a VLAN aware/configurable device. This is very bad marketing on the part of TP-Link (I ordered an "easy smart switch" and kinda freaked out when the product that arrived was an "unmanaged pro" switch). But fear not, these are 802.1q compliant and will work for your purposes.
Those switches are a little wonky. First of all do not use the DHCP setting on the switch, give it a static IP that is within your LAN. At least for my SG-108v3, the management listens on all the VLANs, so it will randomly get DHCP from one of them. (this is really bad if you're switching your cable modem through one of the VLANs, since the switch will get your public IP!)
For initial testing, especially since this is a live network, start with eth0.1, eth0.3 and eth0.7 all in the LAN network. Now even though they are trunked through to different ports on the switch, anything plugged into any of the ports will still be on the LAN. Once you see that that works, you can start making new networks and move one VLAN at a time to them.
A basic guest network has a static IP address usually something .1 and its network does not overlap any of your other networks. It has a DHCP server. It has a separate firewall zone. The zone has a forwarding rule from guest network to wan. Since there is no forwarding from guest to lan, the guests can't reach your LAN devices, but they do have all ports on the router itself. That can be blocked with additional rules.
You do not need to enter gateway or DNS for guest networks that is automatic when you forward them to wan.
Great news, after a short break, I retested the procedure and when checking the network connection the device now received an internal ip with the vlan subnet and is connected to the internet. I'm not sure if I did something wrong before or if I was looking at an old command output, I've been working on setting up these vlans on my network for a few days now maybe I'm starting to lose it a bit.
Thankfully, the vlan works now when there is no switch involved. The switch must be where is issue lies, but it is good to hear it is compatible at the end of the day, was starting to consider if i might of bought an incompatible switch.
Okay I followed your advice and disabled the DHCP settings, definitely don't want the switch having a public ip address. Okay so I will test the lan connections on eth0.1 , 0.2, 0.3 & 0.7, it seems that devices receive an IP on the lan subnet (192.168.1.X) when connected via ethernet and the internet works. Once I start messing with the switch settings to establish the vlan that's when things start to fail.
Thanks for clarifying the network structure, if I understand correctly, internal ip addresses are assigned via the DHCP on any given subnet. Firewalls are used to keep zones within a network separate and a vlan needs it's data forwarded to the wan in order to receive the internet connection, and the wan also handles DNS and gateway. This actually helped a lot thank you.
Trying to trouble shoot my switch now, because with the DHCP off and the ports set the same way I posted in the pictures above no internet is delivered and a lan IP is assigned.
EDIT: Wow, okay, I have vLan 7 operational now over the switch. So with DHCP off the switch is reduced to a port extension for the router. Tagging no longer works, but untagged connections deliver internet over the correct subnet. Will try to make the switch handle 3 or 4 different vLans and come back with an update.
Thank you so much for everybody's help, I learned so much about networking working hands on and this was one of my first attempts to take control of my network and securitize it.
AFAICT, based on my experience with a SG105E and a SG116E, assuming that there is only one uplink with DHCP servers, it appears that it sends a DHCP request via untagged network first (if present) and then presumably looks towards the tagged networks next. If you have a trunk with tagged networks only (which some people feel is the best way to manage trunks -- I can't remember if you're in that camp, @mk24), my guess (total speculation) is that it would try DHCP requests on the tagged networks in order of VLAN ID.
I base my (admittedly limited) experience based on the fact that I have never seen the device acquire an IP in a VLAN other than the untagged network in a trunk (doesn't mean it can't happen some other way, though).
If you had multiple uplinks and were using this switch series to aggregate the VLANs, that could certainly mess things up!