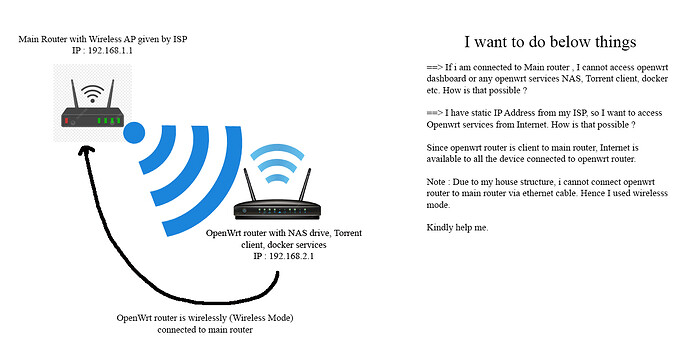
My Openwrt router is wirelessly connected main ISP router. So openwrt is in wireless mode and it is having having various services like NAS drive, Torrent client, Docker.
Main ISP Router : 192.168.1.1
I am unable to access openwrt services if i am connected to main router. I have a static ip given by my ISP, So I want to access openwrt NAS and docker services from internet. Please see the attached image explaining more.
Kindly help me.
Is the OpenWrt router used for any other pruposes other than hosting those services (in other words, is it serving as an AP for other devices or anything like that)?
Does your main router support the addition of user-configured static routes?
Accessing your OpenWrt services from the internet can be done in 2 main ways -- port forwarding or VPN. The latter is much better for security and is the best option if those services don't need to be available to the rest of the internet (in terms of the people who need to be able to access it)... if it's just you (and maybe some family, etc.), you can setup VPN access fairly easily (I recommend wireguard)
@psherman thanks very much for the reply. At present Openwrt is used only for those services.
I dont have much Idea on the VPN setup. I prefer first method which you mentioned. could you please help me to get it done ?
Ok... so there are two really easy ways to fix your situation of accessing the router from the upstream network...
Assign the network that is connected to the wireless uplink (sta mode connection) to the lan firewall zone instead of the wan zone.
change the "input" on the wan firewall zone to "ACCEPT"
If you need help doing either of those, please post your config files...
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/firewall
Meanwhile, the other question about VPN -- take a look at the guides for wireguard (specifically the road warrior type configuration)
@psherman , I dont know how to do that. Hence i am posting the details here. please find the details below
cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdec:24a0:67de::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config interface 'vpn0'
option ifname 'tun0'
option proto 'none'
config interface 'docker'
option ifname 'docker0'
option proto 'none'
option auto '0'
config device
option type 'bridge'
option name 'docker0'
config interface 'wwan'
option proto 'dhcp'
cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/soc/soc:usb@c9000000/c9000000.dwc3/xhci-hcd.0.auto/usb1/1-1/1-1:1.0'
option band '2g'
option htmode 'HT20'
option country 'US'
option disabled '0'
option channel '11'
option legacy_rates '1'
option mu_beamformer '0'
config wifi-iface
option network 'wwan'
option ssid 'FTTH-B668'
option encryption 'psk2'
option device 'radio0'
option mode 'sta'
option bssid 'fake mac address'
option key 'fake password'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/soc/soc:usb@c9000000/c9000000.dwc3/xhci-hcd.0.auto/usb1/1-2/1-2:1.0'
option channel '1'
option band '2g'
option htmode 'HT20'
option country 'US'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6 wwan'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config include 'zerotier'
option type 'script'
option path '/etc/zerotier.start'
option reload '1'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'adbyby'
option type 'script'
option path '/var/etc/adbyby.include'
option reload '1'
config rule 'adblock'
option name 'adblock'
option target 'DROP'
option src 'wan'
option proto 'tcp'
option dest_port '8118'
config include 'mia'
option type 'script'
option path '/etc/mia.include'
option reload '1'
config rule 'openvpn'
option name 'openvpn'
option target 'ACCEPT'
option src 'wan'
option proto 'tcp udp'
option dest_port '1194'
config zone 'vpn'
option name 'vpn'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option network 'vpn0'
config forwarding 'vpntowan'
option src 'vpn'
option dest 'wan'
config forwarding 'vpntolan'
option src 'vpn'
option dest 'lan'
config forwarding 'lantovpn'
option src 'lan'
option dest 'vpn'
config rule 'kms'
option name 'kms'
option target 'ACCEPT'
option src 'wan'
option proto 'tcp'
option dest_port '1688'
config zone 'docker'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option name 'docker'
list network 'docker'
To make the uplink part of the lan zone, simply remove wwan from the wan zone and then add it to the lan zone... it'll look like this:
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
option network 'wwan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
option input 'REJECT'
option forward 'REJECT'
@psherman I made the changes and restarted the Openwrt router. Do I need to make any changes in my Main router. like port forwarding
This solves your problem of access from your main lan > OpenWrt services.
It doesn't help you with the remote access. For that, you'll need to add port forwarding on the main router to either the services of interest, or to the OpenWrt router for the VPN port (recommended route).
I have added the port forwarding rule in the main router.. now its working like charm.. thanks very much @psherman
system
January 26, 2023, 9:44pm
10
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.