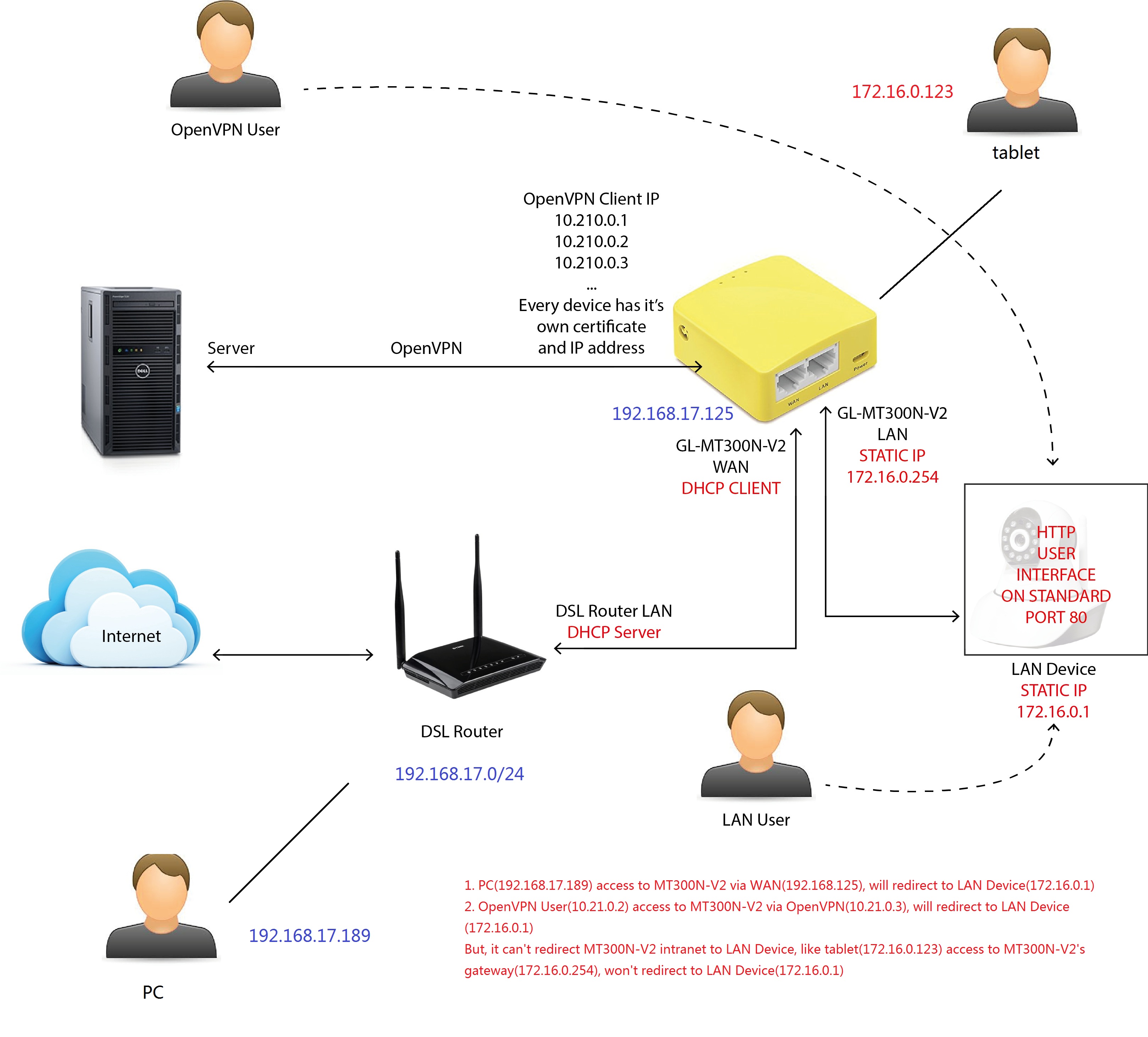
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
Downloading 'http://172.16.0.1/'
07:21:52.703482 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [S], seq 2900303454, win 29200, options [mss 1460,sackOK,TS val 8306754 ecr 0,nop,wscale 4], length 0
07:21:52.703644 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [S], seq 2900303454, win 29200, options [mss 1460,sackOK,TS val 8306754 ecr 0,nop,wscale 4], length 0
07:21:52.703482 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [S], seq 2900303454, win 29200, options [mss 1460,sackOK,TS val 8306754 ecr 0,nop,wscale 4], length 0
07:21:52.703644 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [S], seq 2900303454, win 29200, options [mss 1460,sackOK,TS val 8306754 ecr 0,nop,wscale 4], length 0
07:21:52.703482 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [S], seq 2900303454, win 29200, options [mss 1460,sackOK,TS val 8306754 ecr 0,nop,wscale 4], length 0
07:21:52.703644 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [S], seq 2900303454, win 29200, options [mss 1460,sackOK,TS val 8306754 ecr 0,nop,wscale 4], length 0
07:21:52.703482 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [S], seq 2900303454, win 29200, options [mss 1460,sackOK,TS val 8306754 ecr 0,nop,wscale 4], length 0
07:21:52.703644 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [S], seq 2900303454, win 29200, options [mss 1460,sackOK,TS val 8306754 ecr 0,nop,wscale 4], length 0
07:21:52.705495 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705495 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705495 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705878 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 0
07:21:52.705932 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 0
07:21:52.705495 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705495 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705495 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705878 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 0
07:21:52.705932 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 0
07:21:52.705495 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705495 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705495 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705878 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 0
07:21:52.705932 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 0
07:21:52.705495 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705495 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705495 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [S.], seq 3281663094, ack 2900303455, win 16384, options [mss 1460,nop,wscale 0,nop,nop,TS val 18498795 ecr 8306754], length 0
07:21:52.705878 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 0
07:21:52.705932 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 0
Connecting to 172.16.0.1:80
07:21:52.713448 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 1:35, ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 34: HTTP: GET / HTTP/1.1
07:21:52.713448 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 1:35, ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 34: HTTP: GET / HTTP/1.1
07:21:52.713589 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 1:35, ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 34: HTTP: GET / HTTP/1.1
07:21:52.713448 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 1:35, ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 34: HTTP: GET / HTTP/1.1
07:21:52.713589 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 1:35, ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 34: HTTP: GET / HTTP/1.1
07:21:52.713448 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 1:35, ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 34: HTTP: GET / HTTP/1.1
07:21:52.713589 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 1:35, ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 34: HTTP: GET / HTTP/1.1
07:21:52.713589 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 1:35, ack 1, win 1825, options [nop,nop,TS val 8306755 ecr 18498795], length 34: HTTP: GET / HTTP/1.1
07:21:52.742995 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.742995 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.742995 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.743286 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 35:64, ack 1, win 1825, options [nop,nop,TS val 8306758 ecr 18498798], length 29: HTTP
07:21:52.743340 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 35:64, ack 1, win 1825, options [nop,nop,TS val 8306758 ecr 18498798], length 29: HTTP
07:21:52.743968 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
07:21:52.743968 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
07:21:52.743968 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
07:21:52.744257 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 10, win 1825, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.744468 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 10:194, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 184: HTTP
07:21:52.745605 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 194:1781, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 1587: HTTP
07:21:52.745605 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 194:1781, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 1587: HTTP
07:21:52.745605 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 194:1781, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 1587: HTTP
07:21:52.745859 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1781, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.745899 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [.], ack 1781, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.742995 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.742995 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.742995 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.743286 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 35:64, ack 1, win 1825, options [nop,nop,TS val 8306758 ecr 18498798], length 29: HTTP
07:21:52.743340 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 35:64, ack 1, win 1825, options [nop,nop,TS val 8306758 ecr 18498798], length 29: HTTP
07:21:52.743968 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
07:21:52.743968 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
07:21:52.742995 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.742995 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.742995 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.743286 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 35:64, ack 1, win 1825, options [nop,nop,TS val 8306758 ecr 18498798], length 29: HTTP
07:21:52.743340 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 35:64, ack 1, win 1825, options [nop,nop,TS val 8306758 ecr 18498798], length 29: HTTP
07:21:52.743968 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
07:21:52.743968 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
07:21:52.742995 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.742995 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.742995 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 35, win 17376, options [nop,nop,TS val 18498798 ecr 8306755], length 0
07:21:52.743286 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 35:64, ack 1, win 1825, options [nop,nop,TS val 8306758 ecr 18498798], length 29: HTTP
07:21:52.743340 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [P.], seq 35:64, ack 1, win 1825, options [nop,nop,TS val 8306758 ecr 18498798], length 29: HTTP
07:21:52.743968 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
07:21:52.743968 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [P.], seq 1:10, ack 64, win 17376, options [nop,nop,TS val 18498798 ecr 8306758], length 9: HTTP
HTTP error 401
07:21:52.750842 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [F.], seq 64, ack 1782, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.750842 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [F.], seq 64, ack 1782, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.750930 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [F.], seq 64, ack 1782, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.750842 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [F.], seq 64, ack 1782, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.751102 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.750930 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [F.], seq 64, ack 1782, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.751102 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.751102 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.751102 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.751102 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.751102 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.750930 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [F.], seq 64, ack 1782, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.751102 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.751102 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.751102 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
root@GL-MT300N-V2:~# 07:21:52.750842 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [F.], seq 64, ack 1782, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.750930 IP 172.16.0.254.52446 > 172.16.0.1.80: Flags [F.], seq 64, ack 1782, win 2091, options [nop,nop,TS val 8306759 ecr 18498798], length 0
07:21:52.751102 ethertype IPv4, IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.751102 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0
07:21:52.751102 IP 172.16.0.1.80 > 172.16.0.254.52446: Flags [.], ack 65, win 17376, options [nop,nop,TS val 18498798 ecr 8306759], length 0