The Fritz needs to know that the OpenWrt router (its particular IP in the 178 network) is the gateway to 192.168.1.0/24. Devices on the Fritz network do not know anything about 192.168.1.0. When they return a packet to a device on the OpenWrt lan (which since you're not masquerading, has a return IP of 192.168.1.X) they send it to their default gateway which is the Fritz. Then the Fritz uses its route to forward the packet to the OpenWrt router WAN port. The OpenWrt router has a route to 192.168.1.0 is via br-lan, but it needs a firewall rule to allow such forwarding.
This is what i get:
default via 192.168.100.1 dev pppoe-wan
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
192.168.100.1 dev pppoe-wan scope link src 62.211.227.222
192.168.178.0/24 dev eth1 scope link src 192.168.178.2
root@OpenWrt:~#
The routes are already there.
So the problem can be the firewall?
If i try to ping the ip 192.168.1.11 from my home assistant server (ip 192.168.178.9) i have no answer...
It can be the firewall of 1.11, especially if it is windows.
1.11 it's just a set top box for sat tv, before adding the second router i correctly pinged it
Traceroute:
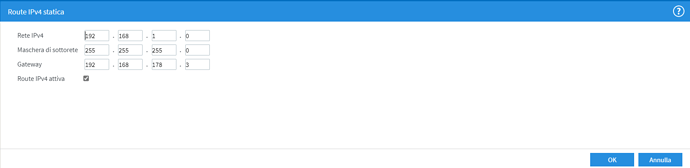
Then you have not installed the static route to fritzbox.
You way that the routes was there... i'm confused... ![]()
This is the OpenWrt, not the Fritz.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd60:cc52:542d::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_eth0_dev'
option name 'eth0'
option macaddr 'xxxx'
config interface 'wan'
option ifname 'eth1'
option proto 'pppoe'
option password 'xxxxl'
option ipv6 'auto'
option username 'xxxxx'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
option blinkrate '2'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5'
config switch_port
option device 'switch0'
option port '1'
option led '6'
config switch_port
option device 'switch0'
option port '2'
option led '9'
config switch_port
option device 'switch0'
option port '5'
option led '2'
config interface 'Modem'
option ifname 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.178.2'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'pci0000:00/0000:00:11.0'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-device 'radio1'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:12.0'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd60:cc52:542d::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_eth0_dev'
option name 'eth0'
option macaddr 'xxxx'
config interface 'wan'
option ifname 'eth1'
option proto 'pppoe'
option password 'xxxxl'
option ipv6 'auto'
option username 'xxxxx'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
option blinkrate '2'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5'
config switch_port
option device 'switch0'
option port '1'
option led '6'
config switch_port
option device 'switch0'
option port '2'
option led '9'
config switch_port
option device 'switch0'
option port '5'
option led '2'
config interface 'Modem'
option ifname 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.178.2'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'pci0000:00/0000:00:11.0'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-device 'radio1'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:12.0'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option mac 'xxxx'
option name 'SkyQ_Mansarda'
option dns '1'
option ip '192.168.1.11'
option leasetime 'infinite'
config host
option mac 'xxxx'
option name 'SkyQ_Salotto'
option dns '1'
option ip '192.168.1.29'
option leasetime 'infinite'
config host
option mac 'xxx'
option name 'SkyQ_Camera'
option dns '1'
option ip '192.168.1.16'
option leasetime 'infinite'
config host
option mac 'xxxxx'
option leasetime 'infinite'
option dns '1'
option name 'HerianPC'
option ip '192.168.1.3'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan Modem'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option masq '1'
option network 'wan wan6 lan'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option dest 'lan'
option src 'wan'
option target 'ACCEPT'
list src_ip '192.168.178.0'
list src_ip '192.168.178.0/24'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
# Generated by iptables-save v1.8.3 on Mon May 11 07:53:22 2020
*nat
:PREROUTING ACCEPT [298906:98250141]
:INPUT ACCEPT [5252:361905]
:OUTPUT ACCEPT [2498:171176]
:POSTROUTING ACCEPT [1:72]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[298906:98250141] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[185545:79254817] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[111159:18863362] -A PREROUTING -i eth1 -m comment --comment "!fw3" -j zone_lan_prerouting
[2202:131962] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[111159:18863362] -A PREROUTING -i eth1 -m comment --comment "!fw3" -j zone_wan_prerouting
[185545:79254817] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_wan_prerouting
[41431:2626747] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[34829:2091154] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[9:468] -A POSTROUTING -o eth1 -m comment --comment "!fw3" -j zone_lan_postrouting
[6592:535053] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[9:468] -A POSTROUTING -o eth1 -m comment --comment "!fw3" -j zone_wan_postrouting
[34829:2091154] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_wan_postrouting
[34838:2091622] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[296704:98118179] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[41430:2626675] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[41430:2626675] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[298906:98250141] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Mon May 11 07:53:22 2020
# Generated by iptables-save v1.8.3 on Mon May 11 07:53:22 2020
*raw
:PREROUTING ACCEPT [2579282:2000465735]
:OUTPUT ACCEPT [11229:1090677]
:zone_lan_helper - [0:0]
[1120581:490126087] -A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
[423778:44793605] -A PREROUTING -i eth1 -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
COMMIT
# Completed on Mon May 11 07:53:22 2020
# Generated by iptables-save v1.8.3 on Mon May 11 07:53:22 2020
*mangle
:PREROUTING ACCEPT [2579284:2000465815]
:INPUT ACCEPT [12876:1206438]
:FORWARD ACCEPT [2311915:1903876112]
:OUTPUT ACCEPT [11232:1091421]
:POSTROUTING ACCEPT [2323029:1904962813]
[1667:90004] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[34623:2077308] -A FORWARD -o eth1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[36474:2177588] -A FORWARD -o br-lan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Mon May 11 07:53:22 2020
# Generated by iptables-save v1.8.3 on Mon May 11 07:53:22 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[34:3429] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[12845:1203129] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[3886:593409] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1880:86640] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[5149:281685] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[980:169986] -A INPUT -i eth1 -m comment --comment "!fw3" -j zone_lan_input
[2830:158049] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i eth1 -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_wan_input
[2311915:1903876112] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[2274492:1901389667] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[2551:394005] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[34872:2092440] -A FORWARD -i eth1 -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i eth1 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_wan_forward
[58:5541] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[11180:1087240] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[8599:911891] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[8:2406] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o eth1 -m comment --comment "!fw3" -j zone_lan_output
[2573:172943] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o eth1 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_wan_output
[2486:111871] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[238:38336] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[1880:86640] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[8:2406] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_dest_ACCEPT -o eth1 -m comment --comment "!fw3" -j ACCEPT
[37423:2486445] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[37423:2486445] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[6129:451671] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[6129:451671] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[8:2406] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[8:2406] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[5149:281685] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[980:169986] -A zone_lan_src_ACCEPT -i eth1 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[118:4720] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[4997:561760] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o eth1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[9:468] -A zone_wan_dest_ACCEPT -o eth1 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o br-lan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[34872:2092440] -A zone_wan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o eth1 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o br-lan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -s 192.168.178.0/32 -p tcp -m comment --comment "!fw3: @rule[9]" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -s 192.168.178.0/24 -p tcp -m comment --comment "!fw3: @rule[9]" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -s 192.168.178.0/32 -p udp -m comment --comment "!fw3: @rule[9]" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -s 192.168.178.0/24 -p udp -m comment --comment "!fw3: @rule[9]" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[2830:158049] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[106:7842] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[2724:150207] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[2573:172943] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[2573:172943] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[2724:150207] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i eth1 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i br-lan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Mon May 11 07:53:22 2020
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
inet 192.168.178.2/24 brd 192.168.178.255 scope global eth1
valid_lft forever preferred_lft forever
13: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
14: pppoe-wan: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1492 qdisc cake state UNKNOWN qlen 3
inet xxx peer 192.168.100.1/32 scope global pppoe-wan
valid_lft forever preferred_lft forever
default via 192.168.100.1 dev pppoe-wan
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
192.168.100.1 dev pppoe-wan scope link src 79.50.133.133
192.168.178.0/24 dev eth1 scope link src 192.168.178.2
local xxxx dev pppoe-wan table local scope host src 79.50.133.133
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.1
broadcast 192.168.178.0 dev eth1 table local scope link src 192.168.178.2
local 192.168.178.2 dev eth1 table local scope host src 192.168.178.2
broadcast 192.168.178.255 dev eth1 table local scope link src 192.168.178.2
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
I can't even ping a device on the same subnet from openwrt, so i think it's a firewall issue.
If i ping 192.168.1.11 from 192.168.1.3 i get no answer
Should be no firewall...except on clients then. It's the same network.
![]()
What can be the issue then? The client is a set top box for sat tv so i doubt he has a firewall (and bte in the other network was working). I can correctly ping the fritz on the other subnet but not the devices on the same subnet
Possibly the firewall of the PC you are pinging from? If it's a Windows PC, make sure the network you are connected to is identified as private.
Uhm.... I correctly ping devices on the other subnet