I'm trying to set up a guest wifi on a TP link Archer C7 running open wrt 18.06.4 as a dumb access point, it has a wired connection to the router. My ISP provided router is very basic, no static routing, no vlan. This
https://blog.doenselmann.com/gaeste-wlan-auf-openwrt-access-point/
describes a method which does not require routing or vlan on the router but the guest wifi network it creates has no internet access.
Has anyone got this working? Is there another solution given my router limitations?
Allow forward from Guest to WAN.
On a dumb AP with locally routed guests, forward from guest to LAN (since WAN, if it still exists, isn't used for anything) and also you need to enable masq and mtu_fix on the lan firewall zone.
I think I have enabled masq and mtu_fix on the lan firewall - see the screenshot below but guest can still not get an IP address
Any other suggestions?
Guests get IP addresses from the DHCP server you set up at the bottom of the guest network interface page.
There is a DHCP server set up for the guest interface. Do I need to change any of the advanced DHCP settings?
Did you figure this out in the end? I'm having the same problem.
Sorry, I didn't get this to work. I think it's necessary to use a vlan and tag the network which is beyond me.
H
Following the "If you are using a wireless AP. Allow guest clients to forward traffic only to the internet.", on the link you provide,
i copy paste this:
Fetch LAN subnet
NET_IF="lan"
. /lib/functions/network.sh
network_flush_cache
network_get_subnet NET_SUB "${NET_IF}"Configure firewall
uci -q delete firewall.guest_wan
uci -q delete firewall.guest_fwd
uci set firewall.guest_fwd="rule"
uci set firewall.guest_fwd.name="Allow-Guest-Forward"
uci set firewall.guest_fwd.src="guest"
uci set firewall.guest_fwd.dest="lan"
uci set firewall.guest_fwd.dest_ip="!${NET_SUB%.}.0/${NET_SUB#/}"
uci set firewall.guest_fwd.proto="all"
uci set firewall.guest_fwd.target="ACCEPT"
uci set firewall.lan.masq="1"
uci commit firewall
/etc/init.d/firewall restart
from https://openwrt.org/docs/guide-user/network/wifi/guestwifi/extra#wireless_ap
still no internet connection,
the guest wifi is connected, guest dhcp is working, and yet, no internet/can not ping 8.8.8.8
FYI, my router also dumb AP, connected to main router via LAN
Collect the diagnostics:
ip address show; ip route show; ip rule show; iptables-save; \
head -n -0 /etc/resolv.* /tmp/resolv.*; \
uci show network; uci show wireless; uci show dhcp; uci show firewall
Thanks for yr reply,
what need to check from diagnostic?
-or- how to copy and paste all the output? I am using putty, and using copy to clipboard seem can not get all the output, so i can copy and paste in here,
(but it seem very big/lot of)
PS: i am not familiar with linux, and also new to openwrt (not more than 3 months)
https://openwrt.org/docs/guide-quick-start/sshadministration
It's problematic for me to advise you how to do it in Windows as I have only Linux. 
root@OpenWrt:/tmp# ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
link/ether 64:66:b3:a0:c5:dd brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 64:66:b3:a0:c5:df brd ff:ff:ff:ff:ff:ff
4: ifb0: <BROADCAST,NOARP> mtu 1500 qdisc noop state DOWN qlen 32
link/ether 6a:18:56:2e:65:fb brd ff:ff:ff:ff:ff:ff
5: ifb1: <BROADCAST,NOARP> mtu 1500 qdisc noop state DOWN qlen 32
link/ether 96:bf:ef:8c:b2:fa brd ff:ff:ff:ff:ff:ff
25: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 64:66:b3:a0:c5:dd brd ff:ff:ff:ff:ff:ff
inet 192.168.213.215/24 brd 192.168.213.255 scope global br-lan
valid_lft forever preferred_lft forever
26: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 64:66:b3:a0:c5:dd brd ff:ff:ff:ff:ff:ff
29: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 64:66:b3:a0:c5:de brd ff:ff:ff:ff:ff:ff
30: wlan0-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 66:66:b3:a0:c5:de brd ff:ff:ff:ff:ff:ff
inet 192.168.0.1/24 brd 192.168.0.255 scope global wlan0-1
valid_lft forever preferred_lft forever
31: wlan0-2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 62:66:b3:a0:c5:de brd ff:ff:ff:ff:ff:ff
inet 192.168.3.1/24 brd 192.168.3.255 scope global wlan0-2
valid_lft forever preferred_lft forever
root@OpenWrt:/tmp# ip route show
192.168.0.0/24 dev wlan0-1 scope link src 192.168.0.1
192.168.3.0/24 dev wlan0-2 scope link src 192.168.3.1
192.168.213.0/24 dev br-lan scope link src 192.168.213.215
root@OpenWrt:/tmp# ip rule show
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
root@OpenWrt:/tmp# iptables-save
# Generated by iptables-save v1.8.3 on Sun Aug 23 04:36:10 2020
*raw
:PREROUTING ACCEPT [11829:1667825]
:OUTPUT ACCEPT [8390:1239953]
:zone_guest_helper - [0:0]
-A PREROUTING -i wlan0-2 -m comment --comment "!fw3: guest CT helper assignment" -j zone_guest_helper
COMMIT
# Completed on Sun Aug 23 04:36:10 2020
# Generated by iptables-save v1.8.3 on Sun Aug 23 04:36:10 2020
*nat
:PREROUTING ACCEPT [5424:913588]
:INPUT ACCEPT [154:31032]
:OUTPUT ACCEPT [132:8976]
:POSTROUTING ACCEPT [132:8976]
:postrouting_GFire_rule - [0:0]
:postrouting_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_GFire_rule - [0:0]
:prerouting_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_GFire_postrouting - [0:0]
:zone_GFire_prerouting - [0:0]
:zone_guest_postrouting - [0:0]
:zone_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i wlan0-1 -m comment --comment "!fw3" -j zone_GFire_prerouting
-A PREROUTING -i wlan0-2 -m comment --comment "!fw3" -j zone_guest_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o wlan0-1 -m comment --comment "!fw3" -j zone_GFire_postrouting
-A POSTROUTING -o wlan0-2 -m comment --comment "!fw3" -j zone_guest_postrouting
-A zone_GFire_postrouting -m comment --comment "!fw3: Custom GFire postrouting rule chain" -j postrouting_GFire_rule
-A zone_GFire_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_GFire_prerouting -m comment --comment "!fw3: Custom GFire prerouting rule chain" -j prerouting_GFire_rule
-A zone_guest_postrouting -m comment --comment "!fw3: Custom guest postrouting rule chain" -j postrouting_guest_rule
-A zone_guest_prerouting -m comment --comment "!fw3: Custom guest prerouting rule chain" -j prerouting_guest_rule
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_postrouting -s 192.168.0.0/24 -m comment --comment "!fw3" -j MASQUERADE
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Sun Aug 23 04:36:10 2020
# Generated by iptables-save v1.8.3 on Sun Aug 23 04:36:10 2020
*mangle
:PREROUTING ACCEPT [11837:1668145]
:INPUT ACCEPT [6565:785433]
:FORWARD ACCEPT [2:156]
:OUTPUT ACCEPT [8405:1244121]
:POSTROUTING ACCEPT [8407:1244277]
-A FORWARD -o br-lan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone lan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o wlan0-1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone GFire MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sun Aug 23 04:36:10 2020
# Generated by iptables-save v1.8.3 on Sun Aug 23 04:36:10 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_GFire_rule - [0:0]
:forwarding_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_GFire_rule - [0:0]
:input_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_GFire_rule - [0:0]
:output_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_GFire_dest_ACCEPT - [0:0]
:zone_GFire_forward - [0:0]
:zone_GFire_input - [0:0]
:zone_GFire_output - [0:0]
:zone_GFire_src_REJECT - [0:0]
:zone_guest_dest_ACCEPT - [0:0]
:zone_guest_dest_REJECT - [0:0]
:zone_guest_forward - [0:0]
:zone_guest_input - [0:0]
:zone_guest_output - [0:0]
:zone_guest_src_REJECT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i wlan0-1 -m comment --comment "!fw3" -j zone_GFire_input
-A INPUT -i wlan0-2 -m comment --comment "!fw3" -j zone_guest_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i wlan0-1 -m comment --comment "!fw3" -j zone_GFire_forward
-A FORWARD -i wlan0-2 -m comment --comment "!fw3" -j zone_guest_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o wlan0-1 -m comment --comment "!fw3" -j zone_GFire_output
-A OUTPUT -o wlan0-2 -m comment --comment "!fw3" -j zone_guest_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_GFire_dest_ACCEPT -o wlan0-1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_GFire_dest_ACCEPT -o wlan0-1 -m comment --comment "!fw3" -j ACCEPT
-A zone_GFire_forward -m comment --comment "!fw3: Custom GFire forwarding rule chain" -j forwarding_GFire_rule
-A zone_GFire_forward -m comment --comment "!fw3: Zone GFire to lan forwarding policy" -j zone_lan_dest_ACCEPT
-A zone_GFire_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_GFire_forward -m comment --comment "!fw3" -j zone_GFire_dest_ACCEPT
-A zone_GFire_input -m comment --comment "!fw3: Custom GFire input rule chain" -j input_GFire_rule
-A zone_GFire_input -p udp -m udp --dport 67:68 -m comment --comment "!fw3: gDHCP" -j ACCEPT
-A zone_GFire_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: gDNS" -j ACCEPT
-A zone_GFire_input -p udp -m udp --dport 53 -m comment --comment "!fw3: gDNS" -j ACCEPT
-A zone_GFire_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_GFire_input -m comment --comment "!fw3" -j zone_GFire_src_REJECT
-A zone_GFire_output -m comment --comment "!fw3: Custom GFire output rule chain" -j output_GFire_rule
-A zone_GFire_output -m comment --comment "!fw3" -j zone_GFire_dest_ACCEPT
-A zone_GFire_src_REJECT -i wlan0-1 -m comment --comment "!fw3" -j reject
-A zone_guest_dest_ACCEPT -o wlan0-2 -m comment --comment "!fw3" -j ACCEPT
-A zone_guest_dest_REJECT -o wlan0-2 -m comment --comment "!fw3" -j reject
-A zone_guest_forward -m comment --comment "!fw3: Custom guest forwarding rule chain" -j forwarding_guest_rule
-A zone_guest_forward ! -d 192.168.213.0/24 -m comment --comment "!fw3: Allow-Guest-Forward" -j zone_lan_dest_ACCEPT
-A zone_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_guest_forward -m comment --comment "!fw3" -j zone_guest_dest_REJECT
-A zone_guest_input -m comment --comment "!fw3: Custom guest input rule chain" -j input_guest_rule
-A zone_guest_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Allow-DNS-Guest" -j ACCEPT
-A zone_guest_input -p udp -m udp --dport 53 -m comment --comment "!fw3: Allow-DNS-Guest" -j ACCEPT
-A zone_guest_input -p udp -m udp --dport 67 -m comment --comment "!fw3: Allow-DHCP-Guest" -j ACCEPT
-A zone_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_guest_input -m comment --comment "!fw3" -j zone_guest_src_REJECT
-A zone_guest_output -m comment --comment "!fw3: Custom guest output rule chain" -j output_guest_rule
-A zone_guest_output -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
-A zone_guest_src_REJECT -i wlan0-2 -m comment --comment "!fw3" -j reject
-A zone_lan_dest_ACCEPT -o br-lan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
COMMIT
# Completed on Sun Aug 23 04:36:10 2020
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# head -n -0 /etc/resolv.* /tmp/resolv.*
==> /etc/resolv.conf <==
==> /tmp/resolv.conf <==
==> /tmp/resolv.conf.auto <==
root@OpenWrt:/tmp# uci show network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0.1'
network.lan.proto='static'
network.lan.ipaddr='192.168.213.215/24'
network.lan.ip6assign='60'
network.lan.dns='9.9.9.9,149.112.112.112' '2620:fe::fe,2620:fe::9'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='1 2 3 4 0t'
network.GNet=interface
network.GNet.proto='static'
network.GNet.force_link='0'
network.GNet.broadcast='192.168.0.255'
network.GNet.ip6assign='60'
network.GNet.ipaddr='192.168.0.1/24'
network.GNet.dns='9.9.9.9,149.112.112.112' '2620:fe::fe, 2620:fe::9'
network.guest=interface
network.guest.proto='static'
network.guest.ipaddr='192.168.3.1'
network.guest.netmask='255.255.255.0'
root@OpenWrt:/tmp# uci show wireless
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.hwmode='11g'
wireless.radio0.path='platform/ar933x_wmac'
wireless.radio0.htmode='HT20'
wireless.radio0.country='TW'
wireless.radio0.legacy_rates='0'
wireless.radio0.txpower='18'
wireless.radio0.channel='10'
wireless.default_radio0=wifi-iface
wireless.default_radio0.device='radio0'
wireless.default_radio0.network='lan'
wireless.default_radio0.mode='ap'
wireless.default_radio0.ssid='emaho^71'
wireless.default_radio0.encryption='psk2+ccmp'
wireless.default_radio0.key='usnisa sitatapatra'
wireless.wifinet1=wifi-iface
wireless.wifinet1.device='radio0'
wireless.wifinet1.mode='ap'
wireless.wifinet1.ssid='GUEST-wifi'
wireless.wifinet1.encryption='none'
wireless.wifinet1.network='GNet'
wireless.wifinet1.isolate='1'
wireless.guest=wifi-iface
wireless.guest.device='radio0'
wireless.guest.mode='ap'
wireless.guest.network='guest'
wireless.guest.ssid='guest'
wireless.guest.encryption='none'
root@OpenWrt:/tmp# uci show dhcp
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].domain='lan'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.ignore='1'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.GNet=dhcp
dhcp.GNet.interface='GNet'
dhcp.GNet.start='100'
dhcp.GNet.limit='150'
dhcp.GNet.leasetime='12h'
dhcp.GNet.ra='server'
dhcp.GNet.dhcpv6='server'
dhcp.GNet.ra_management='1'
dhcp.GNet.dhcp_option='6,9.9.9.9,149.112.112.112'
dhcp.guest=dhcp
dhcp.guest.interface='guest'
dhcp.guest.start='100'
dhcp.guest.limit='150'
dhcp.guest.leasetime='1h'
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[0].masq='1'
firewall.@zone[0].masq_src='192.168.0.1/24'
firewall.@zone[0].mtu_fix='1'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan6'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[2]=zone
firewall.@zone[2].name='GFire'
firewall.@zone[2].network='GNet'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].forward='ACCEPT'
firewall.@zone[2].masq='1'
firewall.@zone[2].mtu_fix='1'
firewall.@zone[2].input='REJECT'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='GFire'
firewall.@forwarding[1].dest='lan'
firewall.@rule[9]=rule
firewall.@rule[9].name='gDHCP'
firewall.@rule[9].proto='udp'
firewall.@rule[9].src='GFire'
firewall.@rule[9].dest_port='67-68'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[10]=rule
firewall.@rule[10].name='gDNS'
firewall.@rule[10].src='GFire'
firewall.@rule[10].dest_port='53'
firewall.@rule[10].target='ACCEPT'
firewall.@rule[10].proto='tcp' 'udp'
firewall.@rule[11]=rule
firewall.@rule[11].name='gBLOCK'
firewall.@rule[11].proto='all'
firewall.@rule[11].src='GFire'
firewall.@rule[11].dest='lan'
firewall.@rule[11].dest_ip='192.168.213.0/24'
firewall.@rule[11].target='DROP'
firewall.@rule[11].enabled='0'
firewall.guest=zone
firewall.guest.name='guest'
firewall.guest.network='guest'
firewall.guest.input='REJECT'
firewall.guest.forward='REJECT'
firewall.guest.output='ACCEPT'
firewall.guest_dns=rule
firewall.guest_dns.name='Allow-DNS-Guest'
firewall.guest_dns.src='guest'
firewall.guest_dns.dest_port='53'
firewall.guest_dns.proto='tcpudp'
firewall.guest_dns.target='ACCEPT'
firewall.guest_dhcp=rule
firewall.guest_dhcp.name='Allow-DHCP-Guest'
firewall.guest_dhcp.src='guest'
firewall.guest_dhcp.dest_port='67'
firewall.guest_dhcp.family='ipv4'
firewall.guest_dhcp.proto='udp'
firewall.guest_dhcp.target='ACCEPT'
firewall.guest_fwd=rule
firewall.guest_fwd.name='Allow-Guest-Forward'
firewall.guest_fwd.src='guest'
firewall.guest_fwd.dest='lan'
firewall.guest_fwd.dest_ip='!192.168.213.0/24'
firewall.guest_fwd.proto='all'
firewall.guest_fwd.target='ACCEPT'
root@OpenWrt:/tmp#
Specify the default gateway for the LAN interface.
It should be your main router, i.e. something like 192.168.213.x.
Then you can remove the old guest network to avoid confusion:
uci -q delete dhcp.GNet
uci -q delete wireless.wifinet1
uci -q delete network.GNet
uci commit dhcp
uci commit wireless
uci commit network
/etc/init.d/dnsmasq enable
/etc/init.d/dnsmasq restart
/etc/init.d/network restart
it work  , thanks a lot
, thanks a lot 
you point out what i am missing.
I set again in another AP router, to create the another set of Guest wlan, and it work.
thanks again 
Can you guys help me with my guest network? I have a unifi ap ac lite connected with 802.11s mesh
Dhcp works on guest but it doesn't provide internet access, also no ping.
output of: ip address show; ip route show; ip rule show; iptables-save; \
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc fq_codel master br-lan state DOWN qlen 1000
link/ether fc:ec:da:89:07:ab brd ff:ff:ff:ff:ff:ff
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether fc:ec:da:89:07:ab brd ff:ff:ff:ff:ff:ff
inet 192.168.0.30/24 brd 192.168.0.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fd7e:7e1e:2b85::1/60 scope global
valid_lft forever preferred_lft forever
inet6 fe80::feec:daff:fe89:7ab/64 scope link
valid_lft forever preferred_lft forever
6: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether fc:ec:da:8b:07:ab brd ff:ff:ff:ff:ff:ff
inet6 fe80::feec:daff:fe8b:7ab/64 scope link
valid_lft forever preferred_lft forever
7: wlan0-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether fe:ec:da:8b:07:ab brd ff:ff:ff:ff:ff:ff
inet6 fe80::fcec:daff:fe8b:7ab/64 scope link
valid_lft forever preferred_lft forever
8: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether fc:ec:da:8a:07:ab brd ff:ff:ff:ff:ff:ff
inet6 fe80::feec:daff:fe8a:7ab/64 scope link
valid_lft forever preferred_lft forever
9: wlan1-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether fe:ec:da:8a:07:ab brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global wlan1-1
valid_lft forever preferred_lft forever
inet6 fe80::fcec:daff:fe8a:7ab/64 scope link
valid_lft forever preferred_lft forever
192.168.0.0/24 dev br-lan scope link src 192.168.0.30
192.168.1.0/24 dev wlan1-1 scope link src 192.168.1.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
*nat
:PREROUTING ACCEPT [55:11012]
:INPUT ACCEPT [9:569]
:OUTPUT ACCEPT [2:236]
:POSTROUTING ACCEPT [2:236]
:postrouting_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_guest_postrouting - [0:0]
:zone_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i wlan0 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i wlan1-1 -m comment --comment "!fw3" -j zone_guest_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o wlan0 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o wlan1-1 -m comment --comment "!fw3" -j zone_guest_postrouting
-A zone_guest_postrouting -m comment --comment "!fw3: Custom guest postrouting rule chain" -j postrouting_guest_rule
-A zone_guest_prerouting -m comment --comment "!fw3: Custom guest prerouting rule chain" -j prerouting_guest_rule
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
*mangle
:PREROUTING ACCEPT [289:44328]
:INPUT ACCEPT [229:25821]
:FORWARD ACCEPT [14:8064]
:OUTPUT ACCEPT [244:74376]
:POSTROUTING ACCEPT [257:81864]
-A FORWARD -o wlan0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_guest_dest_ACCEPT - [0:0]
:zone_guest_dest_REJECT - [0:0]
:zone_guest_forward - [0:0]
:zone_guest_input - [0:0]
:zone_guest_output - [0:0]
:zone_guest_src_REJECT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_dest_DROP - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i wlan0 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i wlan1-1 -m comment --comment "!fw3" -j zone_guest_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i wlan0 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i wlan1-1 -m comment --comment "!fw3" -j zone_guest_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o wlan0 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o wlan1-1 -m comment --comment "!fw3" -j zone_guest_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_guest_dest_ACCEPT -o wlan1-1 -m comment --comment "!fw3" -j ACCEPT
-A zone_guest_dest_REJECT -o wlan1-1 -m comment --comment "!fw3" -j reject
-A zone_guest_forward -m comment --comment "!fw3: Custom guest forwarding rule chain" -j forwarding_guest_rule
-A zone_guest_forward -m comment --comment "!fw3: Block Guest Access to Private Network" -j zone_lan_dest_DROP
-A zone_guest_forward -m comment --comment "!fw3: Zone guest to lan forwarding policy" -j zone_lan_dest_ACCEPT
-A zone_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_guest_forward -m comment --comment "!fw3" -j zone_guest_dest_REJECT
-A zone_guest_input -m comment --comment "!fw3: Custom guest input rule chain" -j input_guest_rule
-A zone_guest_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Allow-DNS-Guest" -j ACCEPT
-A zone_guest_input -p udp -m udp --dport 53 -m comment --comment "!fw3: Allow-DNS-Guest" -j ACCEPT
-A zone_guest_input -p udp -m udp --dport 67:68 -m comment --comment "!fw3: Allow-DHCP-Guest" -j ACCEPT
-A zone_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_guest_input -m comment --comment "!fw3" -j zone_guest_src_REJECT
-A zone_guest_output -m comment --comment "!fw3: Custom guest output rule chain" -j output_guest_rule
-A zone_guest_output -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
-A zone_guest_src_REJECT -i wlan1-1 -m comment --comment "!fw3" -j reject
-A zone_lan_dest_ACCEPT -o br-lan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_DROP -o br-lan -m comment --comment "!fw3" -j DROP
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o wlan0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o wlan0 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o wlan0 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i wlan0 -m comment --comment "!fw3" -j reject
COMMIT
output of: head -n -0 /etc/resolv.* /tmp/resolv.*; \
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.auto <==
output of: uci show network; uci show wireless; uci show dhcp; uci show firewall
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd7e:7e1e:2b85::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0'
network.lan.proto='static'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.gateway='192.168.0.1'
network.lan.ipaddr='192.168.0.30'
network.wwan=interface
network.wwan.proto='dhcp'
network.guest=interface
network.guest.proto='static'
network.guest.netmask='255.255.255.0'
network.guest.ipaddr='192.168.1.1'
network.guest.gateway='192.168.0.1'
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.hwmode='11a'
wireless.radio0.path='pci0000:00/0000:00:00.0'
wireless.radio0.htmode='VHT80'
wireless.radio0.channel='149'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.channel='11'
wireless.radio1.hwmode='11g'
wireless.radio1.path='platform/qca956x_wmac'
wireless.radio1.htmode='HT40'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.mode='ap'
wireless.default_radio1.key='xxxxx'
wireless.default_radio1.ssid='2.4GHZ'
wireless.default_radio1.encryption='psk-mixed'
wireless.default_radio1.network='lan'
wireless.wifinet2=wifi-iface
wireless.wifinet2.mesh_rssi_threshold='0'
wireless.wifinet2.key='xxxxx'
wireless.wifinet2.encryption='sae'
wireless.wifinet2.device='radio0'
wireless.wifinet2.mode='mesh'
wireless.wifinet2.mesh_fwding='1'
wireless.wifinet2.mesh_id='xxxxx'
wireless.wifinet2.network='lan wwan'
wireless.wifinet3=wifi-iface
wireless.wifinet3.ssid='5GHZ'
wireless.wifinet3.encryption='psk-mixed'
wireless.wifinet3.device='radio0'
wireless.wifinet3.mode='ap'
wireless.wifinet3.key='xxxxx'
wireless.wifinet3.network='lan'
wireless.wifinet5=wifi-iface
wireless.wifinet5.ssid='guest'
wireless.wifinet5.encryption='none'
wireless.wifinet5.device='radio1'
wireless.wifinet5.mode='ap'
wireless.wifinet5.network='guest'
dhcp.@.dnsmasq[0]=dnsmasq
dhcp.@.dnsmasq[0].domainneeded='1'
dhcp.@.dnsmasq[0].boguspriv='1'
dhcp.@.dnsmasq[0].filterwin2k='0'
dhcp.@.dnsmasq[0].localise_queries='1'
dhcp.@.dnsmasq[0].rebind_protection='1'
dhcp.@.dnsmasq[0].rebind_localhost='1'
dhcp.@.dnsmasq[0].local='/lan/'
dhcp.@.dnsmasq[0].domain='lan'
dhcp.@.dnsmasq[0].expandhosts='1'
dhcp.@.dnsmasq[0].nonegcache='0'
dhcp.@.dnsmasq[0].authoritative='1'
dhcp.@.dnsmasq[0].readethers='1'
dhcp.@.dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@.dnsmasq[0].resolvfile='/tmp/resolv.conf.auto'
dhcp.@.dnsmasq[0].nonwildcard='1'
dhcp.@.dnsmasq[0].localservice='1'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra='server'
dhcp.lan.ra_management='1'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
dhcp.guest=dhcp
dhcp.guest.interface='guest'
dhcp.guest.start='100'
dhcp.guest.limit='150'
dhcp.guest.leasetime='1h'
firewall.@.defaults[0]=defaults
firewall.@.defaults[0].syn_flood='1'
firewall.@.defaults[0].input='ACCEPT'
firewall.@.defaults[0].output='ACCEPT'
firewall.@.defaults[0].forward='REJECT'
firewall.@.zone[0]=zone
firewall.@.zone[0].name='lan'
firewall.@.zone[0].input='ACCEPT'
firewall.@.zone[0].output='ACCEPT'
firewall.@.zone[0].forward='ACCEPT'
firewall.@.zone[0].network='lan'
firewall.@.zone[0].masq='1'
firewall.@.zone[1]=zone
firewall.@.zone[1].name='wan'
firewall.@.zone[1].input='REJECT'
firewall.@.zone[1].output='ACCEPT'
firewall.@.zone[1].forward='REJECT'
firewall.@.zone[1].masq='1'
firewall.@.zone[1].mtu_fix='1'
firewall.@.zone[1].network='wan wan6 wwan'
firewall.@.forwarding[0]=forwarding
firewall.@.forwarding[0].src='lan'
firewall.@.forwarding[0].dest='wan'
firewall.@.rule[0]=rule
firewall.@.rule[0].name='Allow-DHCP-Renew'
firewall.@.rule[0].src='wan'
firewall.@.rule[0].proto='udp'
firewall.@.rule[0].dest_port='68'
firewall.@.rule[0].target='ACCEPT'
firewall.@.rule[0].family='ipv4'
firewall.@.rule[1]=rule
firewall.@.rule[1].name='Allow-Ping'
firewall.@.rule[1].src='wan'
firewall.@.rule[1].proto='icmp'
firewall.@.rule[1].icmp_type='echo-request'
firewall.@.rule[1].family='ipv4'
firewall.@.rule[1].target='ACCEPT'
firewall.@.rule[2]=rule
firewall.@.rule[2].name='Allow-IGMP'
firewall.@.rule[2].src='wan'
firewall.@.rule[2].proto='igmp'
firewall.@.rule[2].family='ipv4'
firewall.@.rule[2].target='ACCEPT'
firewall.@.rule[3]=rule
firewall.@.rule[3].name='Allow-DHCPv6'
firewall.@.rule[3].src='wan'
firewall.@.rule[3].proto='udp'
firewall.@.rule[3].src_ip='fc00::/6'
firewall.@.rule[3].dest_ip='fc00::/6'
firewall.@.rule[3].dest_port='546'
firewall.@.rule[3].family='ipv6'
firewall.@.rule[3].target='ACCEPT'
firewall.@.rule[4]=rule
firewall.@.rule[4].name='Allow-MLD'
firewall.@.rule[4].src='wan'
firewall.@.rule[4].proto='icmp'
firewall.@.rule[4].src_ip='fe80::/10'
firewall.@.rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@.rule[4].family='ipv6'
firewall.@.rule[4].target='ACCEPT'
firewall.@.rule[5]=rule
firewall.@.rule[5].name='Allow-ICMPv6-Input'
firewall.@.rule[5].src='wan'
firewall.@.rule[5].proto='icmp'
firewall.@.rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@.rule[5].limit='1000/sec'
firewall.@.rule[5].family='ipv6'
firewall.@.rule[5].target='ACCEPT'
firewall.@.rule[6]=rule
firewall.@.rule[6].name='Allow-ICMPv6-Forward'
firewall.@.rule[6].src='wan'
firewall.@.rule[6].dest='*'
firewall.@.rule[6].proto='icmp'
firewall.@.rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@.rule[6].limit='1000/sec'
firewall.@.rule[6].family='ipv6'
firewall.@.rule[6].target='ACCEPT'
firewall.@.rule[7]=rule
firewall.@.rule[7].name='Allow-IPSec-ESP'
firewall.@.rule[7].src='wan'
firewall.@.rule[7].dest='lan'
firewall.@.rule[7].proto='esp'
firewall.@.rule[7].target='ACCEPT'
firewall.@.rule[8]=rule
firewall.@.rule[8].name='Allow-ISAKMP'
firewall.@.rule[8].src='wan'
firewall.@.rule[8].dest='lan'
firewall.@.rule[8].dest_port='500'
firewall.@.rule[8].proto='udp'
firewall.@.rule[8].target='ACCEPT'
firewall.@.include[0]=include
firewall.@.include[0].path='/etc/firewall.user'
firewall.guest=zone
firewall.guest.name='guest'
firewall.guest.network='guest'
firewall.guest.input='REJECT'
firewall.guest.output='ACCEPT'
firewall.guest.forward='REJECT'
firewall.guest_dns=rule
firewall.guest_dns.name='Allow-DNS-Guest'
firewall.guest_dns.src='guest'
firewall.guest_dns.dest_port='53'
firewall.guest_dns.target='ACCEPT'
firewall.guest_dns.proto='tcp' 'udp'
firewall.guest_dhcp=rule
firewall.guest_dhcp.name='Allow-DHCP-Guest'
firewall.guest_dhcp.src='guest'
firewall.guest_dhcp.proto='udp'
firewall.guest_dhcp.target='ACCEPT'
firewall.guest_dhcp.dest_port='67-68'
firewall.@.forwarding[1]=forwarding
firewall.@.forwarding[1].dest='lan'
firewall.@.forwarding[1].src='guest'
firewall.@.rule[11]=rule
firewall.@.rule[11].src='guest'
firewall.@.rule[11].name='Block Guest Access to Private Network'
firewall.@.rule[11].dest='lan'
firewall.@.rule[11].target='DROP'
firewall.@.rule[11].proto='all'
Fix that first:
uci -q delete firewall.@.forwarding[1]
uci -q delete firewall.@.rule[11]
uci commit firewall
/etc/init.d/firewall restart
uci -q delete network.guest.gateway
uci commit network
/etc/init.d/network restart
Then apply this:
https://openwrt.org/docs/guide-user/network/wifi/guestwifi/extra#wireless_ap
In addition, specify upstream DNS:
uci -q delete network.lan.dns
uci add_list network.lan.dns="192.168.0.1"
uci add_list network.lan.dns="8.8.8.8"
uci add_list network.lan.dns="8.8.4.4"
uci commit network
/etc/init.d/network restart
/etc/init.d/dnsmasq enable
/etc/init.d/dnsmasq restart
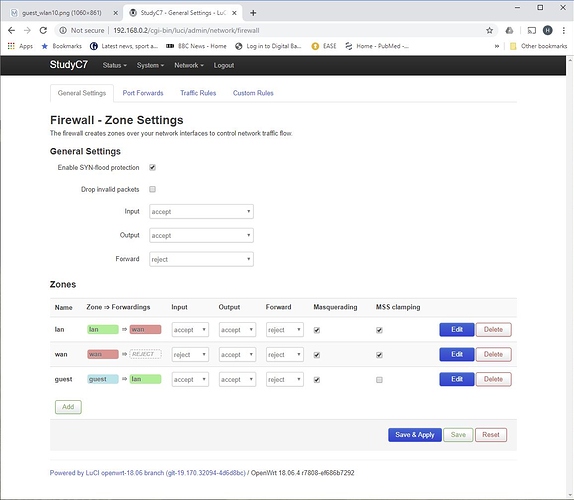
 Do you have any other suggestion?
Do you have any other suggestion?