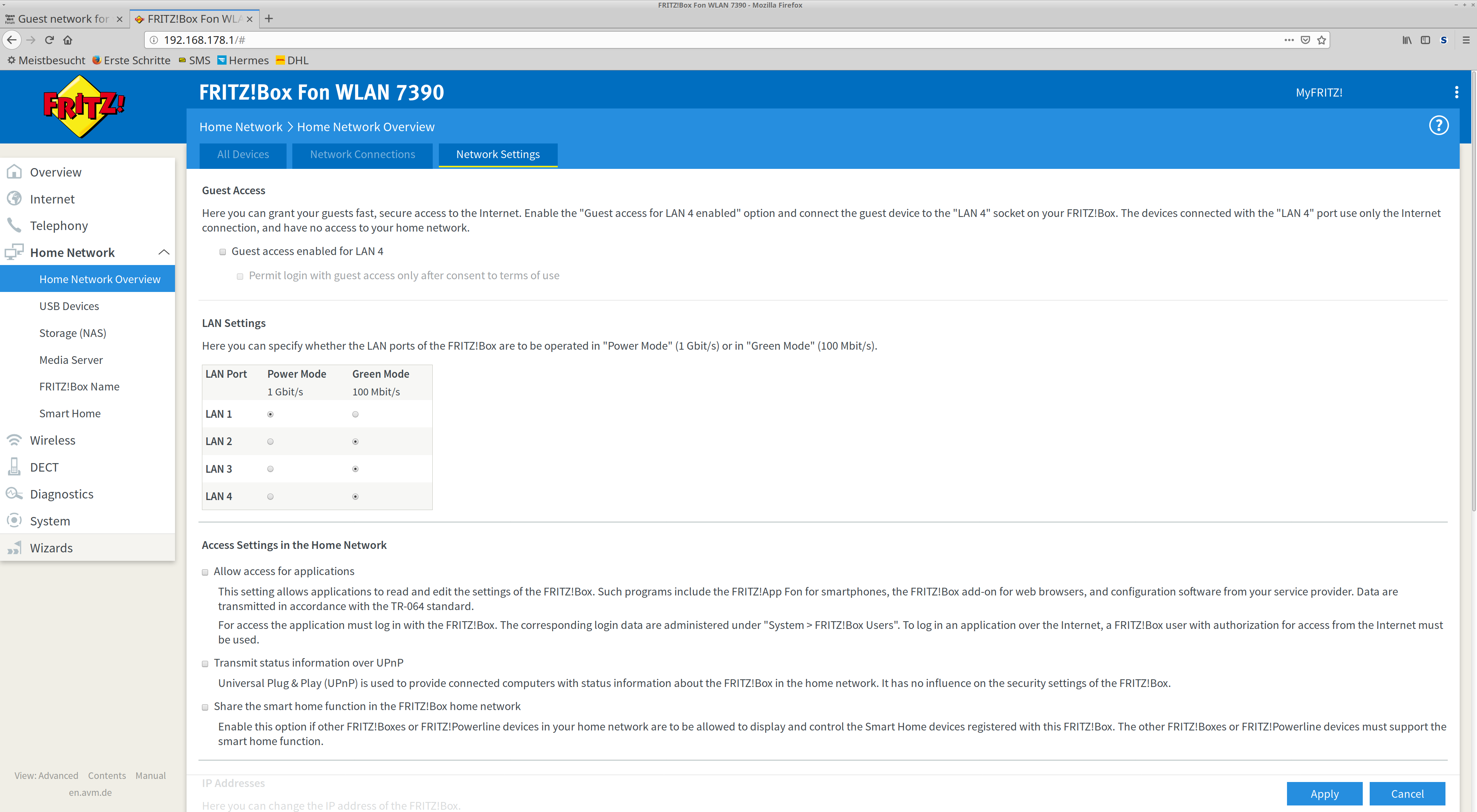
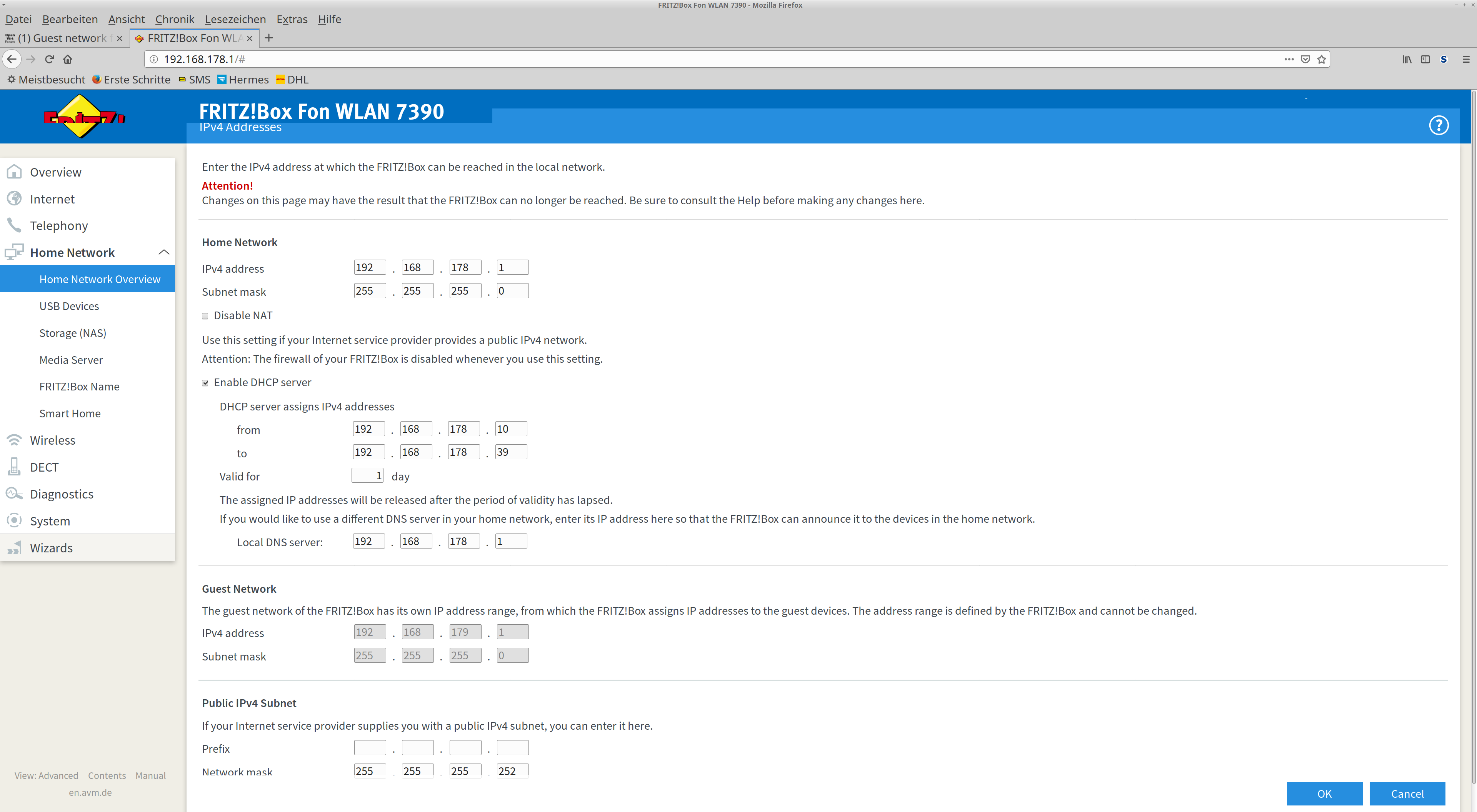
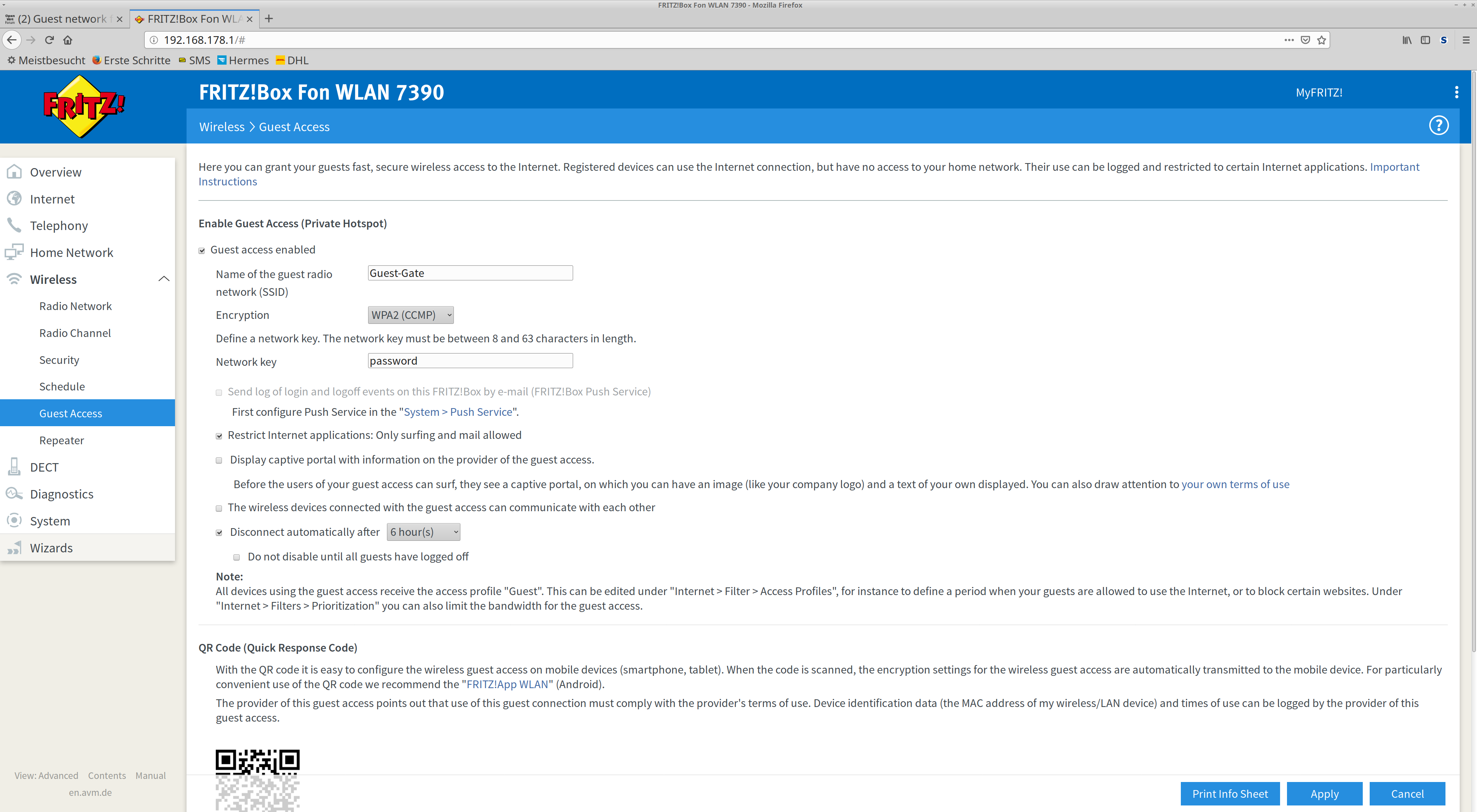
Personally, I'd "ignore" the Fritzbox and just deal with double-NAT. It will make the rest of your configuration portable and a bit easier.
If you need to bridge VLANs over wireless, things get a little trickier. The easiest (not "best") way of handling a couple of VLANs would be to use one WDS "channel" for each of the VLANs. This has the disadvantage of increasing "beacon pollution", so I'd read that article and take heed of disabling legacy rates and older 802.11 standards.
It's been a while since I've looked at WDS in depth, but I'm going on the assumption that a "normal" client can't connect to a WDS SSID. slh points out in the follow-on post that you may not need both an SSID for clients and a separate one for WDS, so I've struck out the separate WDS links.
Remembering that WDS needs to be on the same channel, that means that you're going to have to have both routers set to the same channel on the band supplying WDS.
Concept:
- Fritzbox provides IP connectivity to your "main" router
- Your main router provides NAT to its WAN address, all required services, and controls VLAN connectivity
- Your main router puts the "main network" out on its LAN ports
- Your "slave" router connects its AP SSIDs to the corresponding SSIDs and VLANs on your main router
- Your main router puts the "main network" out on its LAN ports
- Your slave router can only be managed by a single host on your "wired" network
On the main OpenWrt router:
WAN -- static, assigned to the subnet that the Fritzbox is providing, NAT enabled
VLAN 10 -- static IP, 10.0.0.1/24, tagged on the "CPU", bridged to SSID GuestNetwork, bridged to WDS SSID GuestNetworkWDS ; DHCP and DNS running here
VLAN 11 -- static IP, 10.1.0.1/24, tagged on the CPU, bridged to SSID WashingMachine, bridged to WDS SSID WashingMachineWDS ; DHCP and DNS running here
VLAN 12 -- static IP, 10.2.0.1/24, tagged on the CPU, untagged on the LAN ports, bridged to SSID MainNetwork, bridged to WDS SSID MainNetworkWDS; DHCP and DNS running here
Firewall rules to control traffic between VLANs, the Internet, and services on the router, as you see fit
On the slave OpenWrt router:
WAN -- unused
VLAN 10 -- (no IP, no CPU connection to switch), bridged to SSID GuestNetwork, bridged to WDS SSID GuestNetworkWDS
VLAN 11 -- (no IP, no CPU connection to switch), bridged to SSID WashingMachine, bridged to WDS SSID WashingMachineWDS
VLAN 12 -- static IP, 10.2.0.2/24, tagged on the CPU (for management), untagged on the LAN ports, bridged to SSID MainNetwork, bridged to WDS SSID MainNetworkWDS
Firewall rules block all VLAN-to-VLAN traffic, and block all traffic to the router itself, except for SSH/HTTP-S from your designated "desktop" that you use to manage it (better is a management VLAN, but that can wait for another day).
You can "hide" the WDS SSIDs to keep them from appearing on various devices' picker lists. It isn't really any more secure, but "looks better" on other devices.
If you can, using 5 GHz for the WDS will help reduce some of the congestion, especially if you can use wider channels.
("Better" ways would be using a Layer 2 GRE tunnel or a routing protocol like B.A.T.M.A.N. or OLSR. They, however, are much more complicated to implement.)