No dude client isolation, wireless isolation all are same and @Pippo is correct isolation is between wireless and wired 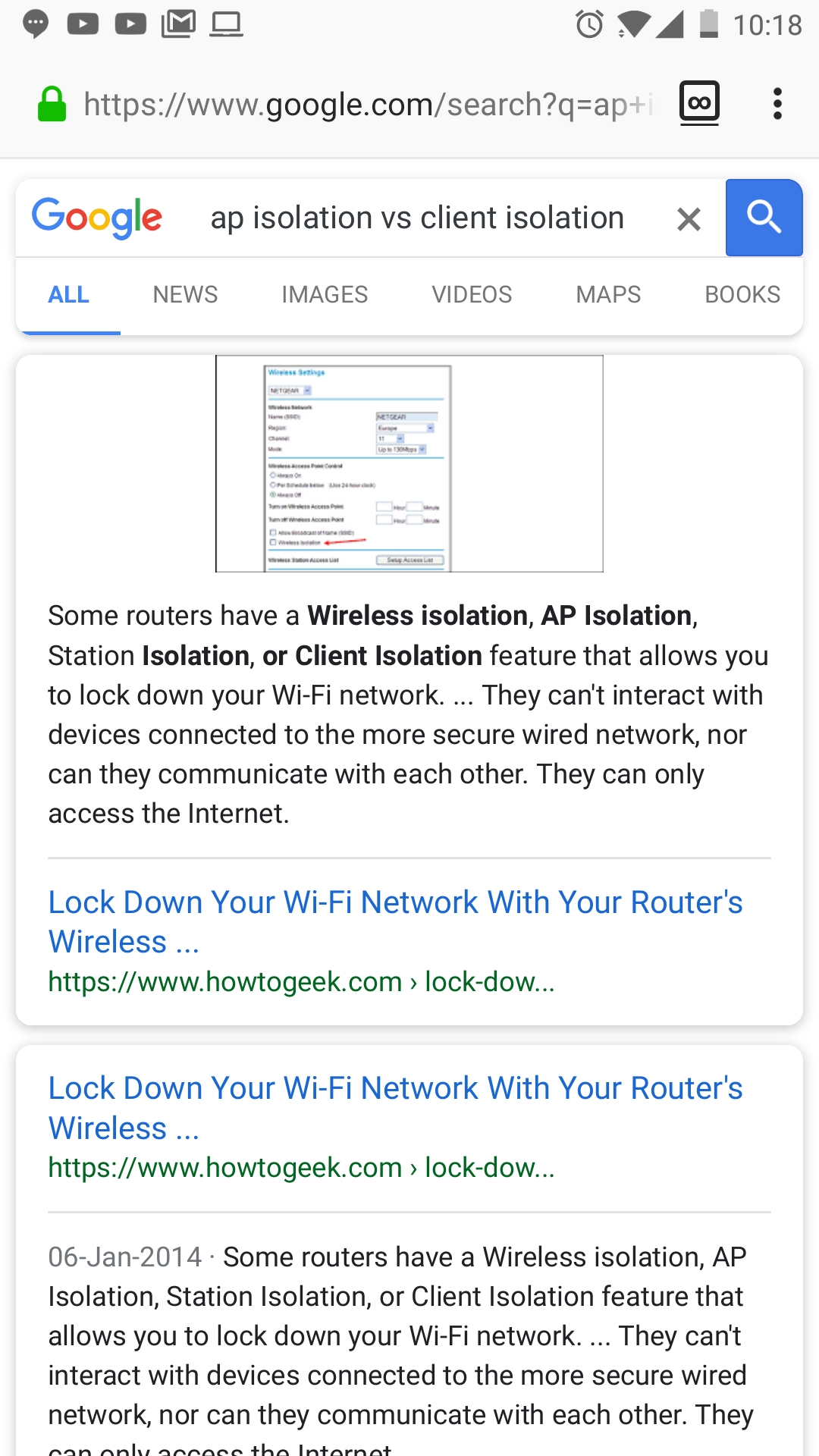
@arjuniet, please provide that information on OpenWrt.
Thanks
From: https://openwrt.org/docs/guide-user/network/wifi/basic#common_options1
isolate boolean no 0 Isolate wireless clients from each other, only applicable in ap mode.
sorry didnt understand ? what you are saying ?
I'm saying you are incorrect - HowToGeek is not OpenWrt. Per the OpenWrt WiKi:
Please refrain from taking over the topic to provide improper information.
oh sorry i beg your pardon , i had some generalised concept , my intention was not to take over the topic , sorry again
No problem. The "isolation" in OpenWrt only refers to the wireless clients. So in order to fully isolate in the OP's case:
- We need to know if his AP is OpenWrt-based
- In any case, the OP can create another VLAN for the WiFi clients, either on the firewall, the AP (if capable) or on the OpenWrt - only permitting traffic from LAN-to-WiFi. Traffic initiating in the opposite direction would not allowed by default.
@lleachii how making vlans can prevent wifi clients from reaching wired clients ? considering it to be openwrt router case
Simple:
- VLAN A (e.g. LAN)
- VLAN B (e.g. WiFi)
They can't talk to each other.
For more, see:
Firewall:
config rule
option src 'lan'
option dest 'wifi'
option name 'Allow_wired_to_wifi'
option proto 'all'
option target 'ACCEPT'
(This can also be done on his firewall instead)
This is the same information suggested at: https://openwrt.org/docs/guide-user/network/wifi/guestwifi/configuration
Again, if you have an issue, please consider making a new thread.
why are vlans created if same can be done without vlans ? WIFI radio and etherport are already seperate in layer 2 untill we bridge them. so why VLANS ?
now as we have three interface , three zone need to be created in firewall
LAN , WAN , WLAN
forwarding should be allowed b/w LAN - WAN and WLAN - WAN and whatever is requirement
and as the creator of topic is not getting ip , host a dhcp server on wlan interface along with a dns resolver.
This time I havnt done any mistake
Simple...
- again, in OpenWrt...you have to have a bridge if you intend to have a WiFi to a VLAN
- OpenWrt creates a br-lan by default
- A vlan is needed for Wired
- IF YOU REMOVE THIS, LAN has to be reconfigured.
- in OpenWrt, VLANs and Interfaces are synonyms, so it is possible to address a wlan1 without VLAN and add it to a bridge. BUT you would need to do this future if, FOR EXAMPLE, the OP CONNECTED IT TO THE FIREWALL MENTIONED!
The only problem is, your suggestion is more complex in OpenWrt.
Again, if you have an issue, please consider making a new thread.
Hi @lleachii, thanks again for your patience and help. To clarify, I am using a GL-MT300A running OpenWRT. My firewall is a real physical firewall box, I'm not referring to the software firewall in OpenWRT. I'm trying to set up VLANs as you explained, but it's a bit different than I'm used to. Here is my /etc/config/network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option ifname 'eth0.1'
option force_link '1'
option macaddr 'XX:XX:XX:XX:XX:3b'
option proto 'dhcp'
option delegate '0'
config interface 'wan'
option type 'bridge'
option _orig_ifname 'eth0.2'
option _orig_bridge 'true'
option ifname 'eth0.2'
option proto 'dhcp'
option macaddr 'XX:XX:XX:XX:XX:3c'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
I see that LAN is delegated 0, and 6t is the CPU, so presumably VLAN 2 is just LAN. VLAN 1 then has WAN and every other interface (which don't exist), and WAN is bridged to radio0. So it looks like the VLANs you outlined are there, just not named as such. I adapted the rule you posted above to suit those names.
Could you point me to any documentation regarding using my upstream firewall/DHCP server as the DHCP server for wireless clients? I haven't had any luck searching for it.
VLAN 2 is WAN!
VLAN 1 should be LAN!
Woops! I see your point and have adjusted accordingly! Any ideas on DHCP?
DHCP on WAN?
You have to allow the DHCP reply. There should be a rule in OpenWrt by default for that.
Are you referring to this:
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
I see that that rule is enabled, but my device still cannot get an IP. The good news is, it can maintain a connection at least!
I see something!
Edit to:
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option macaddr 'XX:XX:XX:XX:XX:3c'
Save and then do /etc/init.d/network restart
There shouldn't be a bridge, as you're only connected to a single system Interface, eth0.2.
Sorry for the delay, it's been a busy week! I've made your adjustments to the WAN config, but I still can't get an IP. I also tried setting WAN as a static IP and enabling DHCP server on it, with or without wireless bridged; still no luck. Does OpenWRT keep a log of DHCP requests? That would make it much easier to troubleshoot. For now, here's what my config files look like.
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option ifname 'eth0.1'
option force_link '1'
option proto 'dhcp'
option delegate '0'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option macaddr 'XX:XX:XX:XX:XX:3c'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
option vid '1'
/etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '10180000.wmac'
option noscan '1'
option channel '1'
option hwmode '11g'
option country 'US'
option distance '50'
option txpower '27'
config wifi-iface
option device 'radio0'
option mode 'ap'
option key 'goodlife'
option ifname 'wlan0'
option ssid 'wifi-test'
option encryption 'psk2+tkip+ccmp'
option network 'wan'
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
option local '/wan/'
option domain 'wan'
list server '84.200.69.80'
list server '216.146.35.35'
list server '37.235.1.174'
list server '208.67.222.222'
list server '91.239.100.100'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option start '100'
option limit '150'
option leasetime '12h'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
- Whoa...did you want your Wireless client to get a WAN IP directly (if so, you do need a bridge)?
- Did you mean for your WiFi to be connected to LAN instead?
- Also, disable DHCP on WAN!
It should go a little something like this:
- My firewall is connected to the internet on its own WAN interface, and has many additional interfaces. The two relevant for us are LAN and WIFI.
- GL-MT300A LAN port connects to my firewall's LAN interface through a switch and is used only for LuCi and dropbear. The firewall denies traffic from clients without a DHCP static mapping, so LAN will need to be a DHCP client. This works!
- GL-MT300A WAN port connects to my firewall's WIFI interface and is used to provide internet for wireless devices. The firewall will not allow traffic between LAN and WIFI so that LAN hosts cannot communicate with wireless devices at all. We have some flexibility on DHCP here, but if possible I would prefer to use the firewall as a DHCP server rather than the wireless router. This doesn't work yet.
This in mind, I've taken your suggestions to set WAN to a static IP and bridge wireless and WAN. This made it so that I can connect to the network, but the device still has no internet and there is no IP listed for it in LuCi. I get the same results regardless of whether DHCP is enabled on OpenWRT WAN. DHCP must be enabled on the firewall WIFI interface or the wireless device cannot connect at all. We're making progress!