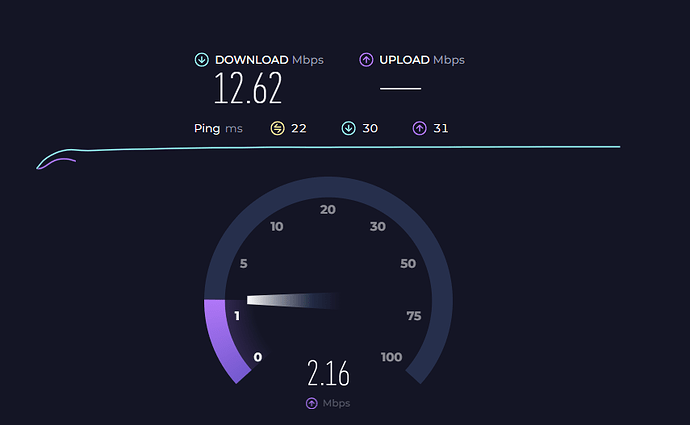
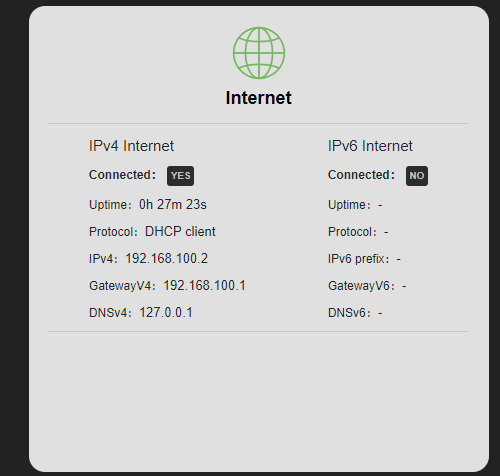
I installed the dnsmasq version and I have to report that it doesn't work (for me) in the vanilla version.
-
I have to use a serial console to configure it because I am unable to login via SSH. I changed the password both via luci and via the console, but using root to login does not work. What is the default root password and why can I not change it?
-
Even by default, the router has Internet but a client connected via cable doesn't have Internet. DNS resolution seems to be the issue:
C:\Users\odhiambo>ping gmail.com
Ping request could not find host gmail.com. Please check the name and try again.
C:\Users\odhiambo>ping gmail.com
Ping request could not find host gmail.com. Please check the name and try again.
C:\Users\odhiambo>nslookup
DNS request timed out.
timeout was 2 seconds.
Default Server: UnKnown
Address: 10.0.0.1
> gmail.com
Server: UnKnown
Address: 10.0.0.1
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to UnKnown timed-out
> gmail.com
Server: UnKnown
Address: 10.0.0.1
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to UnKnown timed-out
>
- Running opkg update also fails, meaning that I cannot install my pkgs.
root@OpenWrt_WRX36:/tmp# opkg update
Downloading https://fantastic-packages.github.io/packages/releases/23.05/package
s/aarch64_cortex-a53/packages/Packages.gz
Updated list of available packages in /var/opkg-lists/fantastic_packages_package
s
Downloading https://fantastic-packages.github.io/packages/releases/23.05/package
s/aarch64_cortex-a53/packages/Packages.sig
Signature check passed.
Downloading https://fantastic-packages.github.io/packages/releases/23.05/package
s/aarch64_cortex-a53/luci/Packages.gz
Updated list of available packages in /var/opkg-lists/fantastic_packages_luci
Downloading https://fantastic-packages.github.io/packages/releases/23.05/package
s/aarch64_cortex-a53/luci/Packages.sig
Signature check passed.
Downloading https://fantastic-packages.github.io/packages/releases/23.05/package
s/aarch64_cortex-a53/special/Packages.gz
Updated list of available packages in /var/opkg-lists/fantastic_packages_special
Downloading https://fantastic-packages.github.io/packages/releases/23.05/package
s/aarch64_cortex-a53/special/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/snapshots/targets/qualcommax/ipq807x/p
ackages/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_core
Downloading https://downloads.openwrt.org/snapshots/targets/qualcommax/ipq807x/p
ackages/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
base/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_base
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
base/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
luci/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_luci
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
luci/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
nss_packages/Packages.gz
*** Failed to download the package list from https://downloads.openwrt.org/snaps
hots/packages/aarch64_cortex-a53/nss_packages/Packages.gz
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
packages/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_packages
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
packages/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
routing/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_routing
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
routing/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
sqm_scripts_nss/Packages.gz
*** Failed to download the package list from https://downloads.openwrt.org/snaps
hots/packages/aarch64_cortex-a53/sqm_scripts_nss/Packages.gz
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
telephony/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_telephony
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
telephony/Packages.sig
Signature check passed.
Collected errors:
* opkg_download: Failed to download https://downloads.openwrt.org/snapshots/pac
kages/aarch64_cortex-a53/nss_packages/Packages.gz, wget returned 8.
* opkg_download: Failed to download https://downloads.openwrt.org/snapshots/pac
kages/aarch64_cortex-a53/sqm_scripts_nss/Packages.gz, wget returned 8.
root@OpenWrt_WRX36:/tmp#
And while at it, does is the image compile with dnsmasq-full or just dnsmasq? I use pbr/luci-proto-pbr which requires dnsmasq-full so I suggest that you build the image using dnsmasq-full.
-
Just for the kicks, I also tested the unbound version and that one works out of the box! But because pbr requires dnsmasq-full, this unbound version is not for me because I have to do Policy Based Routing and I have been using luci-proto-pbr/pbr and wireguard for that.
-
The adblock does NOT work with the dnsmasq version. I checked it and via http://10.0.0.1/cgi-bin/luci/admin/services/adblock and the Status showed error/4.1.5. On the unbound firmware, it shows enabled / 4.1.5.
-
The opkg update also fails to complete cleanly on the unbound version. I tried to install luci-app-minidlna and encountered this error:
Collected errors:
Collected errors:
* pkg_hash_check_unresolved: cannot find dependency kernel (= 6.6.32~edb82a9356
c51dab59aeaca493c36c2f-r1) for kmod-sound-core
* pkg_hash_fetch_best_installation_candidate: Packages for kmod-sound-core found, but incompatible with the architectures configured
But all in all, I wonder what I am missing. I was hoping that it would work out of the box. Do you suppose the issue is the adblock failure on the dnsmasq version?
I am looking forward to the dnsmasq version being build with dnsmasq-full.
I am willing to test it up to where it works because I have a spare functional router that I use for the home.
Last but not least, do I really need sqm? I am on a 45Mbps/45Mbps fiber link, but I cascade my router's WAN to the ISP router's LAN. I suppose some of you are given a direct ethernet cable from the fiber device to your router, no?
Lastly, while at it, could you consider including these packages: kmod-wireguard luci-proto-wireguard wireguard-tools pbr luci-app-pbr nlbwmon luci-app-nlbwmon ? Although I could add those later if opkg allows.
Right now I am abandoning the use of this particular router because I cannot install openvpn-openssl. Also I cannot install wireguard. VPN is a must for me here in KE.
root@OpenWrt_WRX36:/# opkg install openvpn-openssl
Multiple packages (libgcc1 and libgcc1) providing same name marked HOLD or PREFER. Using latest.
Installing openvpn-openssl (2.6.10-r1) to root...
Downloading https://downloads.openwrt.org/snapshots/packages/aarch64_cortex-a53/
packages/openvpn-openssl_2.6.10-r1_aarch64_cortex-a53.ipk
Collected errors:
* pkg_hash_check_unresolved: cannot find dependency kernel (= 6.6.32~edb82a9356
c51dab59aeaca493c36c2f-r1) for kmod-tun
* pkg_hash_fetch_best_installation_candidate: Packages for kmod-tun found, but incompatible with the architectures configured
* satisfy_dependencies_for: Cannot satisfy the following dependencies for openvpn-openssl:
* kernel (= 6.6.32~edb82a9356c51dab59aeaca493c36c2f-r1)
* opkg_install_cmd: Cannot install package openvpn-openssl.
root@OpenWrt_WRX36:/#
Thanks and looking forward to your updates.
![]()