fwiw, I've been running an old Tomato router as an FTP server, wired to LAN port of Chaos Calmer and currently LEDE 17.01 routers. Port forward rule for port 21 is defined. It all works fine for past few years.
Today, I replicated the setup from my main LEDE router to a spare router, but configured WAN port with a static IP address. Then connected a FTP client to the WAN port.
FTP client and server works fine through LEDE router.
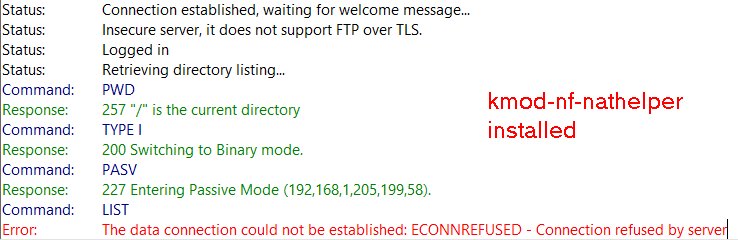
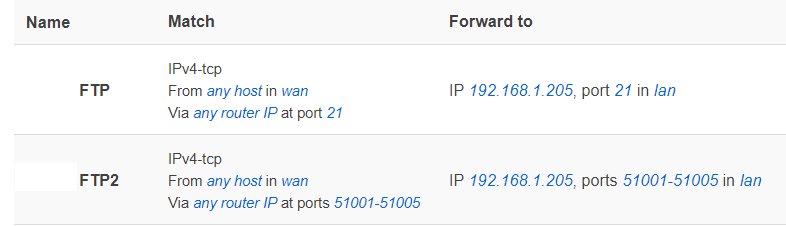
With LEDE, I had to specifically define the range of dynamic ports on the FTP server and set up corresponding port forwarding rules on the router. kmod-nf-nathelper (or kmod-nf-nathelper-extra) also had to be installed.
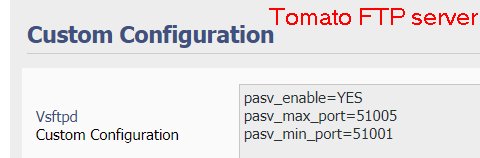
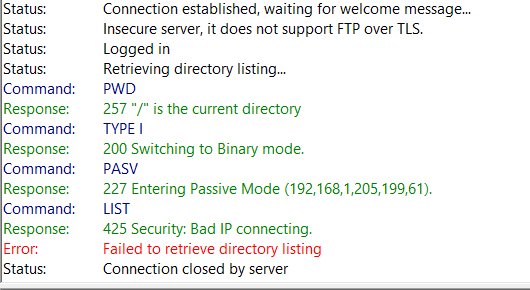
I then upgraded it to OpenWrt 18.06.4 (I also tried 18.06.2). After installing kmod-nf-nathelper (or kmod-nf-nathelper-extra), I encounter this error when using Filezilla FTP client from WAN side:
Without kmod-nf-nathelper* installed, I see the following which looks less promising than above error.
It's been suggested to also install kmod-ipt-raw package. Unfortunately, I see the same error message as above with this package installed too.
Looks like I can log into the FTP server, but cannot proceed any further. Looks similar to your wireshark logs?
I'm no expert but the above logs looks like yours and my FTP servers are returning LAN IP address (eg. 192.168.1.205) to the external FTP client, which is why it is failing.
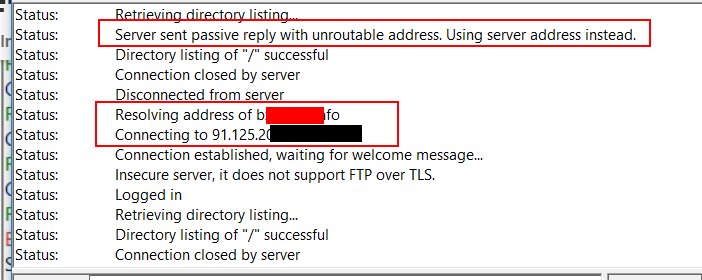
I reverted back to LEDE 17.01.6 and it works fine.
Firewall rules
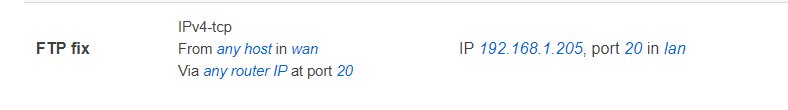
I also added this rule but it made no improvement.
With LEDE 17.01.6, filezilla client connects successfully (image is from may main router)
Update: I've googled two vsftpd settings which may help 'work around' the issue:
pasv_address
pasv_addr_resolve
If I use the pasv_address to hard code the WAN IP address of the OpenWrt 18 test router, I can successfully access the FTP server from a client on the WAN side. But I then had issues accessing the FTP server from LAN side caused by differing port number - this may be solvable.
I couldn't get pasv_addr_resolve to work when 'briefly' tested which allows use of host names in my 'test' environment, but it does seem to work in live environment with LEDE 17 router.
Repeated above tests using a spare laptop configured with Filezilla FTP server in passive FTP mode with same results as reported above.
Similarly, upgrading the test router to OpenWrt 19.07-snapshot and installing kmod-nf-nathelper and kmod-ipt-raw yielded same results in brief testing.