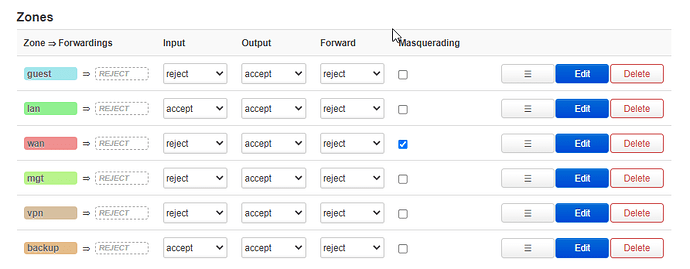
Hi all
I want to have some isolated VLANs and then open explicitly the communication between only some of them, or even concrete ports by using custom rules.
These are my configurations. As you can see, no forwardings are allowed
My current configuration is this one...
The input/output settings work as expected, but not the forward settings.
If i create explicit rules, I can block connectivity.
Am I right?
Thanks!
UPDATE: Input/Output seemed to work, but I have just tried to change an input action to reject and I still have connectivity from the VLAN to the router.
jow
November 2, 2022, 9:23am
2
Is the global forward policy set to reject? The per-zone forward policy just applies to multiple interfaces within the same zone. Zone-to-zone traffic is regulated by the global forward policy.
Also are you testing actual host IPs in different VLANs or just the routers various local IPs? Those will be covered by the input policy and not the forwarding one.
Hi
Checked here:
Network -> Firewall -> General Settings -> Forward=Reject
jow
November 2, 2022, 9:33am
4
Then please mention your OpenWrt version as well as installed packages. Also describe what/how you test exactly. Are there manual iptables or nftables rules configured on the system? Can you provide a screenshot of the firewall status screen?
Firmware Version:
Kernel Version
How i test
I have connected directly my laptop to interface "LAN 3" that is configured as untagged for VLAN "114 lan". IP is assigned via DHCP and then i simply ping:
8.8.8.8 to test forwarding to WAN
IP_of_host_in_VLAN_MGT to test forwarding to another internal VLAN
For both pings ICMP reply is received.
Network and Firewall
I have tried to send interesting forwarding related info.
Thanks for your help
wipeout
November 2, 2022, 10:00am
6
Im not using manual rules. I mean, im using manual rules with explicit IPs but anyway I have disabled them just in case to analyze the problem.
Packages im using:
tcpdump (for troubleshooting)
ddns
wireshark
jow
November 2, 2022, 12:51pm
7
The firewall status screenshot is truncated, we would need to see the entire ruleset. Alternatively connect via SSH and post the output of iptables-save. Also please show the LAN zone settings or the output of uci show firewall via SSH.
# Generated by iptables-save v1.8.7 on Wed Nov 2 14:09:15 2022
*nat
:PREROUTING ACCEPT [59:4058]
:INPUT ACCEPT [30:1820]
:OUTPUT ACCEPT [3:216]
:POSTROUTING ACCEPT [10:755]
:postrouting_backup_rule - [0:0]
:postrouting_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_mgt_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_vpn_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_backup_rule - [0:0]
:prerouting_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_mgt_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_vpn_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_backup_postrouting - [0:0]
:zone_backup_prerouting - [0:0]
:zone_guest_postrouting - [0:0]
:zone_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_mgt_postrouting - [0:0]
:zone_mgt_prerouting - [0:0]
:zone_vpn_postrouting - [0:0]
:zone_vpn_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i eth0.1 -m comment --comment "!fw3" -j zone_backup_prerouting
-A PREROUTING -i wlan1 -m comment --comment "!fw3" -j zone_guest_prerouting
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i eth0.115 -m comment --comment "!fw3" -j zone_mgt_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o eth0.1 -m comment --comment "!fw3" -j zone_backup_postrouting
-A POSTROUTING -o wlan1 -m comment --comment "!fw3" -j zone_guest_postrouting
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o eth0.115 -m comment --comment "!fw3" -j zone_mgt_postrouting
-A zone_backup_postrouting -m comment --comment "!fw3: Custom backup postrouting rule chain" -j postrouting_backup_rule
-A zone_backup_prerouting -m comment --comment "!fw3: Custom backup prerouting rule chain" -j prerouting_backup_rule
-A zone_guest_postrouting -m comment --comment "!fw3: Custom guest postrouting rule chain" -j postrouting_guest_rule
-A zone_guest_prerouting -m comment --comment "!fw3: Custom guest prerouting rule chain" -j prerouting_guest_rule
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_mgt_postrouting -m comment --comment "!fw3: Custom mgt postrouting rule chain" -j postrouting_mgt_rule
-A zone_mgt_prerouting -m comment --comment "!fw3: Custom mgt prerouting rule chain" -j prerouting_mgt_rule
-A zone_vpn_postrouting -m comment --comment "!fw3: Custom vpn postrouting rule chain" -j postrouting_vpn_rule
-A zone_vpn_prerouting -m comment --comment "!fw3: Custom vpn prerouting rule chain" -j prerouting_vpn_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Wed Nov 2 14:09:15 2022
# Generated by iptables-save v1.8.7 on Wed Nov 2 14:09:15 2022
*mangle
:PREROUTING ACCEPT [795:86780]
:INPUT ACCEPT [486:46875]
:FORWARD ACCEPT [306:39518]
:OUTPUT ACCEPT [527:357322]
:POSTROUTING ACCEPT [832:396764]
-A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -i pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Wed Nov 2 14:09:15 2022
# Generated by iptables-save v1.8.7 on Wed Nov 2 14:09:15 2022
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_backup_rule - [0:0]
:forwarding_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_mgt_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_vpn_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_backup_rule - [0:0]
:input_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_mgt_rule - [0:0]
:input_rule - [0:0]
:input_vpn_rule - [0:0]
:input_wan_rule - [0:0]
:output_backup_rule - [0:0]
:output_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_mgt_rule - [0:0]
:output_rule - [0:0]
:output_vpn_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_backup_dest_ACCEPT - [0:0]
:zone_backup_dest_REJECT - [0:0]
:zone_backup_forward - [0:0]
:zone_backup_input - [0:0]
:zone_backup_output - [0:0]
:zone_backup_src_REJECT - [0:0]
:zone_guest_dest_ACCEPT - [0:0]
:zone_guest_dest_REJECT - [0:0]
:zone_guest_forward - [0:0]
:zone_guest_input - [0:0]
:zone_guest_output - [0:0]
:zone_guest_src_REJECT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_dest_REJECT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_mgt_dest_ACCEPT - [0:0]
:zone_mgt_dest_REJECT - [0:0]
:zone_mgt_forward - [0:0]
:zone_mgt_input - [0:0]
:zone_mgt_output - [0:0]
:zone_mgt_src_REJECT - [0:0]
:zone_vpn_dest_ACCEPT - [0:0]
:zone_vpn_dest_REJECT - [0:0]
:zone_vpn_forward - [0:0]
:zone_vpn_input - [0:0]
:zone_vpn_output - [0:0]
:zone_vpn_src_REJECT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i eth0.1 -m comment --comment "!fw3" -j zone_backup_input
-A INPUT -i wlan1 -m comment --comment "!fw3" -j zone_guest_input
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i eth0.115 -m comment --comment "!fw3" -j zone_mgt_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -m comment --comment "!fw3: Zone * to lan forwarding policy" -j zone_lan_dest_ACCEPT
-A FORWARD -i eth0.1 -m comment --comment "!fw3" -j zone_backup_forward
-A FORWARD -i wlan1 -m comment --comment "!fw3" -j zone_guest_forward
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i eth0.115 -m comment --comment "!fw3" -j zone_mgt_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o eth0.1 -m comment --comment "!fw3" -j zone_backup_output
-A OUTPUT -o wlan1 -m comment --comment "!fw3" -j zone_guest_output
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o eth0.115 -m comment --comment "!fw3" -j zone_mgt_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_backup_dest_ACCEPT -o eth0.1 -m comment --comment "!fw3" -j ACCEPT
-A zone_backup_dest_REJECT -o eth0.1 -m comment --comment "!fw3" -j reject
-A zone_backup_forward -m comment --comment "!fw3: Custom backup forwarding rule chain" -j forwarding_backup_rule
-A zone_backup_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_backup_forward -m comment --comment "!fw3" -j zone_backup_dest_REJECT
-A zone_backup_input -m comment --comment "!fw3: Custom backup input rule chain" -j input_backup_rule
-A zone_backup_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_backup_input -m comment --comment "!fw3" -j zone_backup_src_REJECT
-A zone_backup_output -m comment --comment "!fw3: Custom backup output rule chain" -j output_backup_rule
-A zone_backup_output -m comment --comment "!fw3" -j zone_backup_dest_ACCEPT
-A zone_backup_src_REJECT -i eth0.1 -m comment --comment "!fw3" -j reject
-A zone_guest_dest_ACCEPT -o wlan1 -m comment --comment "!fw3" -j ACCEPT
-A zone_guest_dest_REJECT -o wlan1 -m comment --comment "!fw3" -j reject
-A zone_guest_forward -m comment --comment "!fw3: Custom guest forwarding rule chain" -j forwarding_guest_rule
-A zone_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_guest_forward -m comment --comment "!fw3" -j zone_guest_dest_REJECT
-A zone_guest_input -m comment --comment "!fw3: Custom guest input rule chain" -j input_guest_rule
-A zone_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_guest_input -m comment --comment "!fw3" -j zone_guest_src_REJECT
-A zone_guest_output -m comment --comment "!fw3: Custom guest output rule chain" -j output_guest_rule
-A zone_guest_output -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
-A zone_guest_src_REJECT -i wlan1 -m comment --comment "!fw3" -j reject
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_REJECT -o br-lan -m comment --comment "!fw3" -j reject
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to * forwarding policy" -j ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_REJECT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_mgt_dest_ACCEPT -o eth0.115 -m comment --comment "!fw3" -j ACCEPT
-A zone_mgt_dest_REJECT -o eth0.115 -m comment --comment "!fw3" -j reject
-A zone_mgt_forward -m comment --comment "!fw3: Custom mgt forwarding rule chain" -j forwarding_mgt_rule
-A zone_mgt_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_mgt_forward -m comment --comment "!fw3" -j zone_mgt_dest_REJECT
-A zone_mgt_input -m comment --comment "!fw3: Custom mgt input rule chain" -j input_mgt_rule
-A zone_mgt_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_mgt_input -m comment --comment "!fw3" -j zone_mgt_src_REJECT
-A zone_mgt_output -m comment --comment "!fw3: Custom mgt output rule chain" -j output_mgt_rule
-A zone_mgt_output -m comment --comment "!fw3" -j zone_mgt_dest_ACCEPT
-A zone_mgt_src_REJECT -i eth0.115 -m comment --comment "!fw3" -j reject
-A zone_vpn_forward -m comment --comment "!fw3: Custom vpn forwarding rule chain" -j forwarding_vpn_rule
-A zone_vpn_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_vpn_forward -m comment --comment "!fw3" -j zone_vpn_dest_REJECT
-A zone_vpn_input -m comment --comment "!fw3: Custom vpn input rule chain" -j input_vpn_rule
-A zone_vpn_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_vpn_input -m comment --comment "!fw3" -j zone_vpn_src_REJECT
-A zone_vpn_output -m comment --comment "!fw3: Custom vpn output rule chain" -j output_vpn_rule
-A zone_vpn_output -m comment --comment "!fw3" -j zone_vpn_dest_ACCEPT
-A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Wed Nov 2 14:09:15 2022
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].synflood_protect='1'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='backup'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='REJECT'
firewall.@zone[0].network='Backup'
firewall.@zone[0].input='REJECT'
firewall.@zone[1]=zone
firewall.@zone[1].name='guest'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].network='Guest'
firewall.@zone[2]=zone
firewall.@zone[2].name='lan'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].network='LAN'
firewall.@zone[2].forward='REJECT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[3]=zone
firewall.@zone[3].name='wan'
firewall.@zone[3].input='REJECT'
firewall.@zone[3].output='ACCEPT'
firewall.@zone[3].forward='REJECT'
firewall.@zone[3].masq='1'
firewall.@zone[3].mtu_fix='1'
firewall.@zone[3].network='wan'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].dest='lan'
firewall.@zone[4]=zone
firewall.@zone[4].output='ACCEPT'
firewall.@zone[4].forward='REJECT'
firewall.@zone[4].name='mgt'
firewall.@zone[4].network='MGT'
firewall.@zone[4].input='REJECT'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='lan'
firewall.@zone[5]=zone
firewall.@zone[5].output='ACCEPT'
firewall.@zone[5].forward='REJECT'
firewall.@zone[5].name='vpn'
firewall.@zone[5].network='VPN'
firewall.@zone[5].input='REJECT'
jow
November 2, 2022, 1:43pm
9
Hi,
this incomplete rule here is likely causing your issues:
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].dest='lan'
It misses a src option which in the end causes the staging of rules that accept forwarding traffic anywhere.
Please run the following uci commands and retry your tests:
uci delete firewall.@forwarding[0]
uci commit firewall
fw3 restart
2 Likes
wipeout
November 2, 2022, 1:58pm
10
Worked like a charm
Thanks!!
1 Like
system
November 12, 2022, 1:58pm
11
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.