Hello there,
When I enable the port to be forwarded, it shows as 'Stealth' in ShieldsUp! GRC tool. The port I am trying to open is recognized as the right protocol. I assume this is because the router is set to 'reject' at some point in the chain.
When I disable the port to be forwarded, it shows as closed. That is correct.
No combination of INPUT/OUTPUT/FORWARD 'reject/accept/drop' works on my firewall page. There is no change at all from any of the combinations and results on ShieldsUp! GRC tool or yougetsignal.com
xFinity has told me they are not blocking any ports, however they have reported the modem seems to be blocking ports. See My Hardware section at the end. They have recommended contacting Motorola CS. I have submitted a ticket with them in parallel to this post. I see no way that the modem could be blocking ports via the login page my modem has.
My Firewall settings are correct on my Host PC. I have previously used this PC as a host at my last house/router setup and had no issues. I have confirmed the host firewall rules allow both UDP and TDP on 7777.
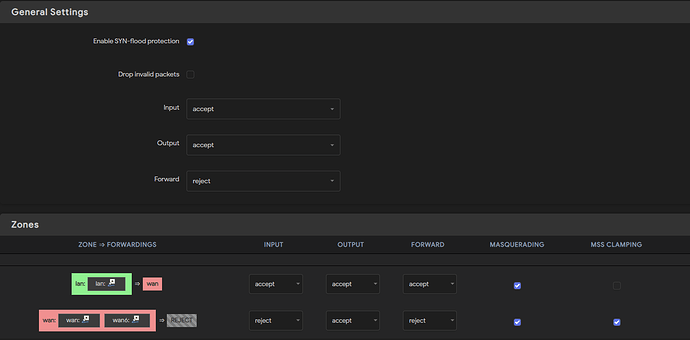
Now, onto my setup. These are screenshots of my config:
Firewall:
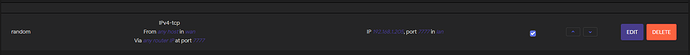
Port Forward rule:
Static IP Lease:
My Hardware:
I have only been using the LUCI interface as I have no familiarity with the CLI. If suggestions are brought up to use that interface, please provide instructions.
turn off masquerading in the lan firewall zone.
If that doesn't fix it, please post your complete config
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/firewall
1 Like
If you are trying in the general settings, it won't make much difference. When accessing from the internet, it's the wan zone which matters.
Other than that, remove the masq as @psherman suggested and post the iptables-save -c -t nat
1 Like
I am trying the Masq in just a few minutes. Waiting for Host to boot up.
ssh into your router and then issue those commands on the CLI (command line interface).
Quick instruction on SSH or should I google/youtube?
cat /etc/config/network OUTPUT:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option type 'bridge'
option ifname 'eth1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_eth1_dev'
option name 'eth1'
option macaddr 'MACADDRESS'
config interface 'wan'
option ifname 'eth0'
option proto 'dhcp'
config device 'wan_eth0_dev'
option name 'eth0'
option macaddr 'MACADDRESS'
config interface 'wan6'
option ifname 'eth0'
option _orig_ifname 'eth0'
option _orig_bridge 'false'
option proto 'dhcp'
cat /etc/config/firewall OUTPUT:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option fullcone '1'
option flow_offloading '1'
option flow_offloading_hw '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option input 'REJECT'
option forward 'REJECT'
option network 'wan wan6'
option mtu_fix '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config include 'zerotier'
option type 'script'
option path '/etc/zerotier.start'
option reload '1'
config include 'gowebdav'
option type 'script'
option path '/var/etc/gowebdav.include'
option reload '1'
config include 'openclash'
option type 'script'
option path '/var/etc/openclash.include'
option reload '1'
config include 'passwall'
option type 'script'
option path '/var/etc/passwall.include'
option reload '1'
config include 'passwall_server'
option type 'script'
option path '/var/etc/passwall_server.include'
option reload '1'
config include 'softethervpn'
option type 'script'
option path '/usr/share/softethervpn/firewall.include'
option reload '1'
config include 'shadowsocksr'
option type 'script'
option path '/var/etc/shadowsocksr.include'
option reload '1'
config include 'wrtbwmon'
option type 'script'
option path '/etc/wrtbwmon.include'
option reload '1'
config rule 'openvpn'
option name 'openvpn'
option target 'ACCEPT'
option src 'wan'
option proto 'tcp udp'
option dest_port '1194'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option dest_ip '192.168.1.205'
option name 'random'
option proto 'tcp'
option src_dport '7777'
option dest_port '7777'
config forwarding
option dest 'wan'
option src 'lan'
iptables-save -c -t nat OUTPUT:
# Generated by iptables-save v1.8.7 on Thu May 26 02:06:55 2022
*nat
:PREROUTING ACCEPT [3343:721447]
:INPUT ACCEPT [754:54157]
:OUTPUT ACCEPT [607:42812]
:POSTROUTING ACCEPT [367:18340]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[620:42816] -A PREROUTING -p udp -m comment --comment DNSMASQ -m udp --dport 53 -j REDIRECT --to-ports 53
[3707:738987] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[3223:713685] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[484:25302] -A PREROUTING -i eth0 -m comment --comment "!fw3" -j zone_wan_prerouting
[2976:400840] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[367:18340] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[2609:382500] -A POSTROUTING -o eth0 -m comment --comment "!fw3" -j zone_wan_postrouting
[367:18340] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.205/32 -p tcp -m tcp --dport 7777 -m comment --comment "!fw3: random (reflection)" -j SNAT --to-source 192.168.1.1
[3223:713685] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d PUBLICIP -p tcp -m tcp --dport 7777 -m comment --comment "!fw3: random (reflection)" -j DNAT --to-destination 192.168.1.205:7777
[2609:382500] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[2609:382500] -A zone_wan_postrouting -m comment --comment "!fw3" -j FULLCONENAT
[484:25302] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[7:404] -A zone_wan_prerouting -p tcp -m tcp --dport 7777 -m comment --comment "!fw3: random" -j DNAT --to-destination 192.168.1.205:7777
[477:24898] -A zone_wan_prerouting -m comment --comment "!fw3" -j FULLCONENAT
COMMIT
# Completed on Thu May 26 02:06:55 2022
There are a lot of vpn/proxy scripts.... I'm guessing that you are not using an official version of OpenWrt, and that may explain the problem (variants of OpenWrt may not work the same way that the official ones do because of customizations that are made by the developer/vendor)... let's verify that:
Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
ubus call system board
1 Like
Tyzam1
May 25, 2022, 6:19pm
10
psherman:
ubus call system board
{
"kernel": "5.4.162",
"hostname": "OpenWrt",
"system": "ARMv8 Processor rev 4",
"model": "FriendlyElec NanoPi R4S",
"board_name": "friendlyarm,nanopi-r4s",
"release": {
"distribution": "ImmortalWrt",
"version": "18.06-k5.4-SNAPSHOT",
"revision": "r11985-6bc7e9db52",
"target": "rockchip/armv8",
"description": "ImmortalWrt 18.06-k5.4-SNAPSHOT r11985-6bc7e9db52 (2022-05-07)"
}
}
Tyzam1
May 25, 2022, 6:21pm
11
We can absolutely get rid of the VPN stuff if you think it's causing problems.
Tyzam1:
ImmortalWrt
I'd recommend asking the developers (or support forums) for ImmoralWrt, or installing an official version of OpenWrt. In addition, the current stable release version of OpenWrt is 21.02.3 -- 18.06 is obsolete and unsupported (and may have security vulnerabilities). At the very least, please check to see if ImmoralWrt has a newer version.
1 Like
I wouldn't recommend making many changes to the ImmoralWrt version (such as removing the VPN stuff) because that may end up causing other issues (I have no idea if it could break things). Best bet is to use official OpenWrt.
2 Likes
Tyzam1
May 25, 2022, 6:24pm
14
I will do that. I had used this one following a guide specifically for R4S. I will follow up after trying OpenWRT.
Great. Let us know if you still have any questions or issues once you've got OpenWrt on there.
Welcome R4S club
SoC – Rockchip RK3399 hexa-core processor with dual-Core Cortex-A72 up to 2.0GHz, quad-core Cortex-A53 up to 1.5GHz, Mali-T864 GPU with OpenGL ES1.1/2.0/3.0/3.1, OpenCL, DX11, and AFBC support, 4K VP9 and 4K 10-bit H265/H264 60fps video decoder
System Memory – 4GB LPDDR4
Storage – MicroSD card slot
Networking – 2x GbE(RTL8211E 1Gbps - RTL8111H 1Gbps), including one native Gigabit Ethernet, and one PCIe Gigabit Ethernet
USB – 2x USB 3.0 Type-A ports, USB 2.0 via 4-pin header
E…
thats the semi offical thread.
You can use the offical OpenWrt snapshot (its not in main yet)
i personally like https://github.com/anaelorlinski/OpenWrt-NanoPi-R2S-R4S-Builds as he has docker built in. He also supports both the 1gb and 4gb builds. I dont know if the 1gb patch got added to OpenWrt yet. It was suppose to be upstreamed some while back but as i dont have the 1gb version its not a problem i keep an eye on.
FriendlyARM NanoPi R4S The NanoPi R4S (as “R4S”) is an open source platform designed and developed by FriendlyElec for IoT applications. The R4S uses the RK3399 SoC, has two Gbps Ethernet ports, microSD storage, and either 1GB DDR3 or 4GB LPDDR4...
2 Likes
Tyzam1
May 25, 2022, 6:34pm
17
I have the 4GB version, so I will try this one, Thanks!
1 Like
Tyzam1:
Quick instruction on SSH
If you are using windows? Putty for SSH and WinSCP for filetransfers etc.
Tyzam1
May 25, 2022, 8:02pm
19
Looks like I'm having the same issue
ubus call system board:
{
"kernel": "5.15.25",
"hostname": "FriendlyWrt",
"system": "ARMv8 Processor rev 4",
"model": "FriendlyElec NanoPi R4S",
"board_name": "friendlyelec,nanopi-r4s",
"release": {
"distribution": "OpenWrt",
"version": "22.03.0-rc1",
"revision": "r19302-df622768da",
"target": "rockchip/armv8",
"description": "OpenWrt 22.03.0-rc1 r19302-df622768da"
}
}
iptables-save -c -t nat
# Generated by iptables-save v1.8.7 on Wed May 25 20:00:17 2022
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:DOCKER - [0:0]
[1407:87442] -A PREROUTING -m addrtype --dst-type LOCAL -j DOCKER
[0:0] -A OUTPUT ! -d 127.0.0.0/8 -m addrtype --dst-type LOCAL -j DOCKER
[0:0] -A POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE
[0:0] -A DOCKER -i docker0 -j RETURN
COMMIT
# Completed on Wed May 25 20:00:17 2022
cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone 'docker'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option name 'docker'
list network 'docker'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Ark Game1'
option src 'wan'
option src_dport '7777'
option dest_port '7777'
option dest_ip '192.168.1.205'
list proto 'tcp'
list proto 'udp'
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd00:ab:cd::/48'
config device
option name 'eth0'
option macaddr 'MACADD'
config interface 'wan'
option device 'eth0'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config device
option name 'eth1'
option macaddr 'MACADD'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.1'
config interface 'docker'
option device 'docker0'
option proto 'none'
option auto '0'
config device
option type 'bridge'
option name 'docker0'
Have you verified that the host (at 192.168.1.205) is listening for (and responding to) connection requests (you can test this locally within your LAN).