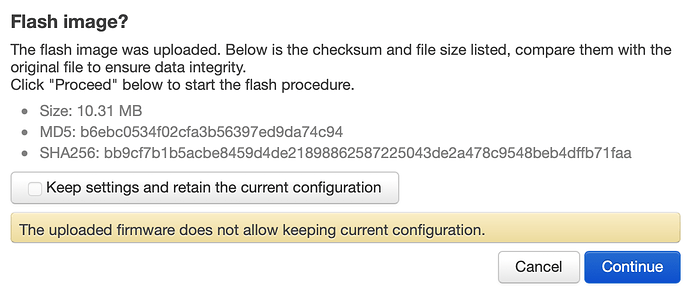
Is there a way to force a sysupgrade via LuCI to never preserve the old config? Better yet, not even show an option to do so? I build a firmware that self configures the router with scrips under /etc/uci-defaults and I would rather start fresh every time instead of trying to manage (merge with) the existing config, which might (or not) be working.
Iirc @rmilecki added support for this to the sysupgrade framework a while back:
LuCI support to honour this flag has been added in:
What's missing is a way to directly control that from the given image. I could imagine a new flag in the OpenWrt firmware image signature, but for that new generic sysupgrade code honouring that must be added first.
Thx, I cannot check right now but if this code is in 19.07, then I could patch the file from the first PR directly on the router. I will check later today.
If you're talking about the checkbox in Luci, then for 18.06.x you can add the following to your uci-defaults script to unset it by default:
sed -i 's|<input type="checkbox" name="keep" id="keep" checked="checked" />|<input type="checkbox" name="keep" id="keep" />|' /usr/lib/lua/luci/view/admin_system/flashops.htm
Luci has changed a lot for 19.07, so I'm yet to check what needs to be changed there.
The approach below works better for me
diff /rom/usr/libexec/validate_firmware_image /usr/libexec/validate_firmware_image
11c11
< ALLOW_BACKUP=1
---
> ALLOW_BACKUP=0
Thanks, changed my sed to sed -i 's|ALLOW_BACKUP=1|ALLOW_BACKUP=0|' /usr/libexec/validate_firmware_image
Would the signature-based approach support the image builder? Asking, because I have no idea what a signature is in this case.
Maybe a simpler approach could be to source a file from /usr/libexec/validate_firmware_image, which could be just a single line ALLOW_BACKUP=1 or ALLOW_BACKUP=1 ? The file would reside somewhere under /etc and may or may not exist on a given image.
Seems to me that ignoring sysupgrade.tar at boot would be more robust than assuming the previous firmware (which might not be yours) didn’t create one.
Well, I think both use cases are valid: 1) the current firmware does not want its config to be reused/visible (for security or other reasons) and 2) the new firmware does not want to accept the existing config.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.