Thanks for the reference, but I am not a developer.
There should be log entries to provide insight of why you cannot restore upstream connectivity, via ssh cli you could try:
ifdown wan ; ifup wan ; logread -f
Hello,
I`ve try with "ifdown wan ; ifup wan ; logread -f" and see the result:
Blockquoteroot@turris:~# ifdown wan
root@turris:~# ifup wan
root@turris:~# logread -f
May 27 06:57:42 turris pppd[21264]: Plugin rp-pppoe.so loaded.
May 27 06:57:42 turris pppd[21264]: RP-PPPoE plugin version 3.8p compiled against pppd 2.4.7
May 27 06:57:42 turris pppd[21264]: pppd 2.4.7 started by root, uid 0
May 27 08:57:43 turris kernel: [39277.264440] mvneta f1034000.ethernet eth2: Link is Down
May 27 06:57:43 turris netifd: Network device 'eth2' link is down
May 27 06:57:43 turris netifd: Interface 'wan' has link connectivity loss
May 27 06:57:45 turris netifd: Network device 'eth2' link is up
May 27 06:57:45 turris netifd: Interface 'wan' has link connectivity
May 27 06:57:45 turris netifd: Interface 'wan' is setting up now
May 27 08:57:45 turris kernel: [39279.341105] mvneta f1034000.ethernet eth2: Link is Up - 1Gbps/Full - flow control off
May 27 06:57:47 turris pppd[21264]: PPP session is 2376
May 27 06:57:47 turris pppd[21264]: Connected to d4:6d:50:4e:81:d3 via interface eth2
May 27 08:57:47 turris kernel: [39281.657095] pppoe-wan: renamed from ppp0
May 27 06:57:47 turris pppd[21264]: Using interface pppoe-wan
May 27 06:57:47 turris pppd[21264]: Connect: pppoe-wan <--> eth2
May 27 06:57:47 turris pppd[21264]: Terminating on signal 15
May 27 06:57:47 turris pppd[21264]: Connection terminated.
May 27 06:57:47 turris pppd[21264]: Sent PADT
May 27 06:57:47 turris pppd[21264]: Exit.
May 27 06:57:47 turris netifd: Interface 'wan' is now down
May 27 06:57:47 turris netifd: Interface 'wan' is disabled
May 27 08:57:47 turris kernel: [39281.785974] mvneta f1034000.ethernet eth2: Link is Down
May 27 08:57:47 turris kernel: [39281.901992] mvneta f1034000.ethernet eth2: PHY [f1072004.mdio-mii:01] driver [Marvell 88E1510]
May 27 08:57:47 turris kernel: [39281.921071] mvneta f1034000.ethernet eth2: configuring for phy/sgmii link mode
May 27 08:57:47 turris kernel: [39281.928414] IPv6: ADDRCONF(NETDEV_UP): eth2: link is not ready
May 27 08:57:47 turris kernel: [39281.934584] mvneta f1034000.ethernet eth2: Link is Up - 1Gbps/Full - flow control off
May 27 06:57:47 turris netifd: Interface 'wan' is enabled
May 27 06:57:47 turris netifd: Interface 'wan' is setting up now
May 27 08:57:47 turris kernel: [39281.943458] IPv6: ADDRCONF(NETDEV_CHANGE): eth2: link becomes ready
May 27 06:57:47 turris insmod: module is already loaded - slhc
May 27 06:57:47 turris insmod: module is already loaded - ppp_generic
May 27 06:57:47 turris insmod: module is already loaded - pppox
May 27 06:57:47 turris insmod: module is already loaded - pppoe
May 27 06:57:47 turris pppd[21649]: Plugin rp-pppoe.so loaded.
May 27 06:57:48 turris pppd[21649]: RP-PPPoE plugin version 3.8p compiled against pppd 2.4.7
May 27 06:57:48 turris pppd[21649]: pppd 2.4.7 started by root, uid 0
May 27 06:57:49 turris netifd: Network device 'eth2' link is down
May 27 06:57:49 turris netifd: Interface 'wan' has link connectivity loss
May 27 08:57:49 turris kernel: [39283.104036] mvneta f1034000.ethernet eth2: Link is Down
May 27 06:57:51 turris netifd: Network device 'eth2' link is up
May 27 06:57:51 turris netifd: Interface 'wan' has link connectivity
May 27 06:57:51 turris netifd: Interface 'wan' is setting up now
May 27 08:57:51 turris kernel: [39285.180736] mvneta f1034000.ethernet eth2: Link is Up - 1Gbps/Full - flow control off
May 27 06:57:53 turris pppd[21649]: PPP session is 2377
May 27 06:57:53 turris pppd[21649]: Connected to d4:6d:50:4e:81:d3 via interface eth2
May 27 08:57:53 turris kernel: [39287.338498] pppoe-wan: renamed from ppp0
May 27 06:57:53 turris pppd[21649]: Using interface pppoe-wan
May 27 06:57:53 turris pppd[21649]: Connect: pppoe-wan <--> eth2
May 27 06:57:53 turris pppd[21649]: Terminating on signal 15
May 27 06:57:53 turris pppd[21649]: Connection terminated.
May 27 06:57:53 turris pppd[21649]: Sent PADT
May 27 06:57:53 turris pppd[21649]: Exit.
May 27 06:57:53 turris netifd: Interface 'wan' is now down
May 27 06:57:53 turris netifd: Interface 'wan' is disabled
May 27 08:57:53 turris kernel: [39287.465434] mvneta f1034000.ethernet eth2: Link is Down
May 27 08:57:53 turris kernel: [39287.580918] mvneta f1034000.ethernet eth2: PHY [f1072004.mdio-mii:01] driver [Marvell 88E1510]
May 27 08:57:53 turris kernel: [39287.594040] mvneta f1034000.ethernet eth2: configuring for phy/sgmii link mode
May 27 08:57:53 turris kernel: [39287.601416] IPv6: ADDRCONF(NETDEV_UP): eth2: link is not ready
...
Repeats again and again and don't stop. Will not reconnect in this way!
Sorry for the presentation here. Maybe it`s wrong.
I must reboot the router.
I`ve not enough knowledge to catch what is wrong here.
Maybe you have any idea what is wrong.
THX
If the manual reconnection does not work, we should try to solve this issue first.
No point in dealing with the automatic reconnection now.
Sure,
what can be the next step?
Let's have a look at the configuration first
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
root@turris:~# uci export network
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd94:8c3b:f847::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option bridge_empty '1'
list ifname 'lan0'
list ifname 'lan1'
list ifname 'lan2'
list ifname 'lan3'
list ifname 'lan4'
option _turris_mode 'managed'
config interface 'wan'
option ifname 'eth2'
option username '*redact*'
option password '*redact*'
option ipv6 '1'
option proto 'pppoe'
config interface 'guest_turris'
option enabled '1'
option type 'bridge'
option proto 'static'
option ipaddr '10.111.222.1'
option netmask '255.255.255.0'
option bridge_empty '1'
config interface 'wan6'
option ifname '@wan'
option proto 'dhcpv6'
uci export wireless
I do not use WLAN from the Turris Omnia Router. I`ve two separate APs for the WLAN net.
root@turris:~# uci export dhcp
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option port '0'
config dhcp 'lan'
option interface 'lan'
option dhcpv6 'server'
option ra 'server'
option ignore '0'
option leasetime '43200'
option start '106'
option limit '144'
list dhcp_option '6,192.168.1.1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest_turris'
option interface 'guest_turris'
option ignore '0'
option start '100'
option limit '150'
option leasetime '3600'
list dhcp_option '6,10.111.222.1'
root@turris:~# uci export firewall
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone 'guest_turris'
option enabled '1'
option name 'guest_turris'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
list network 'guest_turris'
config forwarding 'guest_turris_forward_wan'
option enabled '1'
option name 'guest to wan forward'
option src 'guest_turris'
option dest 'wan'
config rule 'guest_turris_dns_rule'
option enabled '1'
option name 'guest dns rule'
option src 'guest_turris'
option proto 'tcpudp'
option dest_port '53'
option target 'ACCEPT'
config rule 'guest_turris_dhcp_rule'
option enabled '1'
option name 'guest dhcp rule'
option src 'guest_turris'
option proto 'udp'
option src_port '67-68'
option dest_port '67-68'
option target 'ACCEPT'
config rule 'wan_ssh_turris_rule'
option name 'wan_ssh_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '22'
option proto 'tcp'
option src 'wan'
config rule 'wan_http_turris_rule'
option name 'wan_http_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '80'
option proto 'tcp'
option src 'wan'
config rule 'wan_https_turris_rule'
option name 'wan_https_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '443'
option proto 'tcp'
option src 'wan'
config rule 'turris_wan_6in4_rule'
option enabled '0'
root@turris:~# head -n -0 /etc/firewall.user
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
root@turris:~# iptables-save -c
# Generated by iptables-save v1.6.2 on Wed May 27 10:35:57 2020
*nat
:PREROUTING ACCEPT [4577:392406]
:INPUT ACCEPT [680:43810]
:OUTPUT ACCEPT [1736:129047]
:POSTROUTING ACCEPT [14:839]
:postrouting_guest_turris_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_guest_turris_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_guest_turris_postrouting - [0:0]
:zone_guest_turris_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[4577:392406] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[4008:366350] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[569:26056] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i br-guest_turris -m comment --comment "!fw3" -j zone_guest_turris_prerouting
[4629:282476] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[4615:281637] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o br-guest_turris -m comment --comment "!fw3" -j zone_guest_turris_postrouting
[0:0] -A zone_guest_turris_postrouting -m comment --comment "!fw3: Custom guest_turris postrouting rule chain" -j postrouting_guest_turris_rule
[0:0] -A zone_guest_turris_prerouting -m comment --comment "!fw3: Custom guest_turris prerouting rule chain" -j prerouting_guest_turris_rule
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[4008:366350] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[4615:281637] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[4615:281637] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[569:26056] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Wed May 27 10:35:57 2020
# Generated by iptables-save v1.6.2 on Wed May 27 10:35:57 2020
*mangle
:PREROUTING ACCEPT [1364745:1363115221]
:INPUT ACCEPT [21799:1629905]
:FORWARD ACCEPT [1341962:1361294215]
:OUTPUT ACCEPT [20091:1240081]
:POSTROUTING ACCEPT [1362049:1362534093]
[3462:194008] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Wed May 27 10:35:57 2020
# Generated by iptables-save v1.6.2 on Wed May 27 10:35:57 2020
*filter
:INPUT ACCEPT [1:590]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_guest_turris_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_guest_turris_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_guest_turris_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_guest_turris_dest_ACCEPT - [0:0]
:zone_guest_turris_dest_REJECT - [0:0]
:zone_guest_turris_forward - [0:0]
:zone_guest_turris_input - [0:0]
:zone_guest_turris_output - [0:0]
:zone_guest_turris_src_REJECT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[15842:833277] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[5965:797044] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[2416:650865] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[553:23220] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[2640:106380] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[909:39799] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i br-guest_turris -m comment --comment "!fw3" -j zone_guest_turris_input
[1341962:1361294215] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[1338427:1361085709] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[3535:208506] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i br-guest_turris -m comment --comment "!fw3" -j zone_guest_turris_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[15842:833277] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[4260:408236] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[2534:279868] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1:40] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[1725:128328] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o br-guest_turris -m comment --comment "!fw3" -j zone_guest_turris_output
[881:36203] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[25:3446] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[553:23220] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_guest_turris_dest_ACCEPT -o br-guest_turris -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_guest_turris_dest_REJECT -o br-guest_turris -m comment --comment "!fw3" -j reject
[0:0] -A zone_guest_turris_forward -m comment --comment "!fw3: Custom guest_turris forwarding rule chain" -j forwarding_guest_turris_rule
[0:0] -A zone_guest_turris_forward -m comment --comment "!fw3: Zone guest_turris to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_guest_turris_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_guest_turris_forward -m comment --comment "!fw3" -j zone_guest_turris_dest_REJECT
[0:0] -A zone_guest_turris_input -m comment --comment "!fw3: Custom guest_turris input rule chain" -j input_guest_turris_rule
[0:0] -A zone_guest_turris_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: guest dns rule" -j ACCEPT
[0:0] -A zone_guest_turris_input -p udp -m udp --dport 53 -m comment --comment "!fw3: guest dns rule" -j ACCEPT
[0:0] -A zone_guest_turris_input -p udp -m udp --sport 67:68 --dport 67:68 -m comment --comment "!fw3: guest dhcp rule" -j ACCEPT
[0:0] -A zone_guest_turris_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_guest_turris_input -m comment --comment "!fw3" -j zone_guest_turris_src_REJECT
[0:0] -A zone_guest_turris_output -m comment --comment "!fw3: Custom guest_turris output rule chain" -j output_guest_turris_rule
[0:0] -A zone_guest_turris_output -m comment --comment "!fw3" -j zone_guest_turris_dest_ACCEPT
[0:0] -A zone_guest_turris_src_REJECT -i br-guest_turris -m comment --comment "!fw3" -j reject
[1:40] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[3535:208506] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[3535:208506] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[2640:106380] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[2640:106380] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[1:40] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[1:40] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[2639:105790] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[4:203] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[5256:336631] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[909:39799] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[3:150] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[906:39649] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[1725:128328] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[1725:128328] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[906:39649] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
COMMIT
root@turris:~# ip -4 addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
21: br-guest_turris: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN qlen 1000
inet 10.111.222.1/24 brd 10.111.222.255 scope global br-guest_turris
valid_lft forever preferred_lft forever
22: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
23: pppoe-wan: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1492 qdisc fq_codel state UNKNOWN qlen 3
inet 134.101.155.233 peer 84.46.104.216/32 scope global pppoe-wan
valid_lft forever preferred_lft forever
root@turris:~# ip -4 ro li tab all
default via 84.46.104.216 dev pppoe-wan
10.111.222.0/24 dev br-guest_turris scope link src 10.111.222.1
84.46.104.216 dev pppoe-wan scope link src 134.101.155.233
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
broadcast 10.111.222.0 dev br-guest_turris table local scope link src 10.111.222.1
local 10.111.222.1 dev br-guest_turris table local scope host src 10.111.222.1
broadcast 10.111.222.255 dev br-guest_turris table local scope link src 10.111.222.1
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
local 134.101.155.233 dev pppoe-wan table local scope host src 134.101.155.233
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.1
root@turris:~# ip -4 ru
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
One info more: I`ve bought the Turris Omnia router as a second hand device and I must do a factory reset.
Therefore I expect to start with the standard configuration and nothing is crazy.
My Internet connection is FTTH.
One idea more: I've a new Turris Omnia brand new router in addition available. Normally I want sent back to the shop where I' be bought the router but I can test these device an will have a look there is the same procedure.
In wan interface you can enable option keepalive='6 10' to check periodically if the connection is alive.
In dhcp you don't need these, they are automatically propagated:
list dhcp_option '6,192.168.1.1'
list dhcp_option '6,10.111.222.1'
Remove any cronjobs you might have.
If the error persists take a backup of the configuration, do a reset to defaults and configure from scratch. Which OpenWrt version are you running? ubus call system board
root@turris:~# ubus call system board
{
"kernel": "4.14.162",
"hostname": "turris",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Turris Omnia",
"board_name": "armada-385-turris-omnia",
"release": {
"distribution": "TurrisOS",
"version": "4.0.5",
"revision": "ab9d1bf",
"target": "mvebu\/cortexa9",
"description": "TurrisOS 4.0.5 ab9d1bf"
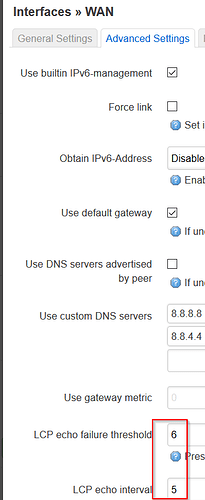
How I can activate the option keepalive='6 10' in the LuCi UI or means this the cmd on the cmd line?
On the UI side I can`t observe any CronJob.
What Ive wrote: Ive done an factory reset (5 days ago).
Makes sense?
Ive activate the shown option and after Ive "save & apply" this settings the connection is separate and I can`t reconnect.
I must reboot again the router.
The configuration is a little bit different.
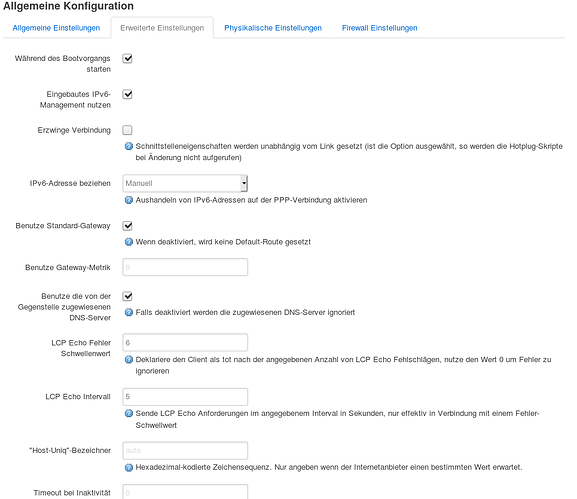
Have a look for example on "Optian IPv6 adress" it`s deactivated in your settings. On my settings is on "manual".
This does not appear to be related to an officially released OpenWrt version.
It is unlikely that you will receive useful input here. You can either seek advise from the relevant maintainer or flash with OpenWrt image.
What I said in the beginning: It`s a Turris Omnia Router but they based on OpenWRT.
You're using a german keyboard, right? 
The backtick character has a special meaning in the forum markup and that's why the text you write comes with different fonts and missing apostrophes 
The IPV6 is probably harmless: I'm using a tunnel because my ISP has poor IPV6 service (LOL, they call it "experimental", must be some sort of marketspeak for shit!)
They are based, but we don't support them.
You can either switch to OpenWrt or ask here for help.
OK, thanks a lot for your support.
The issue is with the PPPoE authentication process and that might be caused by something on the ISP's back-end.
The ppp instance on the router is issuing a SIGTERM (for unknown reason) signal
If you want to try to debug the matter it would require to alter /etc/ppp/options and add
debug
kdebug 7
also try with the ppp options (same file)
passive
maxfail 0
persist
The final process arguments pppd is running with can be queried with ps -aux | grep pppd - ![]() you may want to obfuscate potentially private data such as username | password
you may want to obfuscate potentially private data such as username | password
For verbose debug output in the logs of netifd it would require to edit /etc/init.d/network
modify procd_set_param command /sbin/netifd by adding -l 5, it should read then
procd_set_param command /sbin/netifd -l 5
and add below that line
procd_set_param stderr 1
Once done/set execute service network restart ; logread -f
With
through /lib/netifd/proto/ppp.sh is seems that ppp arguments set in /etc/ppp/options are discarded/neglected. Arguments should therefore be set through option pppd_options in /etc/config/network (but not all such available arguments are working through the UCI parser).
And then
which might cause issues with netifd's supervisory role.
Did you ever try
in the WAN section of /etc/config/network ?
Sorry for the delay.
I've switch to the Turris Forum and there is under the following link in thread an workaround available: