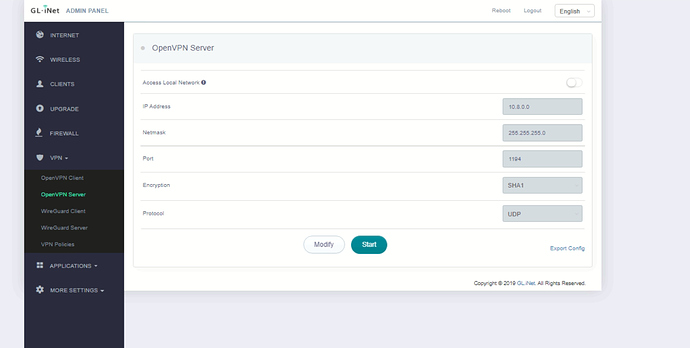
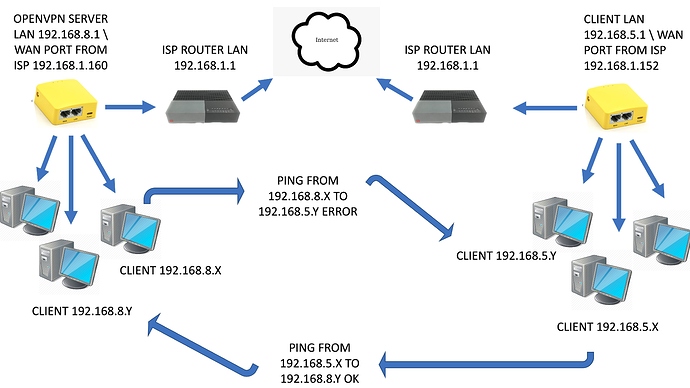
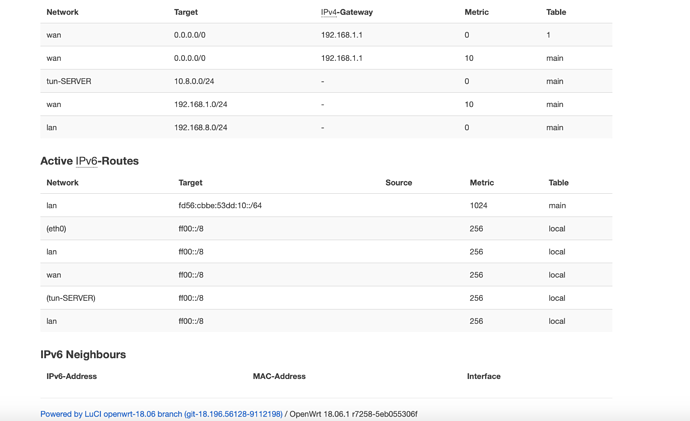
what I've done it's the simply start open vpn server with the simple gui wizard interface like I've attached in this post, nothing else, once that, I've exported the .ovpn config file in the client side. Now my question is: why I'm be able to ping from client to server and not the reverse? the two small router that I'm using server side and client side are the same. there's any standard guide to fix it? I really appreciate your suggestion but are unuseful to fix it untill now. for the advanced options I really don't know how to do it.
no idea how to use iroute option 
Let's see the configs then (from both devices):
uci show network; uci show firewall ; uci show openvpn; \
ip -4 addr; ip -4 ro; ip -4 ru; \
iptables-save -c
this is server side ---> https://pastebin.com/K6G7RxXM
this is client side ---> https://pastebin.com/7ZNcenpB
firewall.vpn_server_zone.masq='1'
What is the reason for NATing the VPN traffic?
OpenVPN configuration is not there. Find where you stored it and paste it again here.
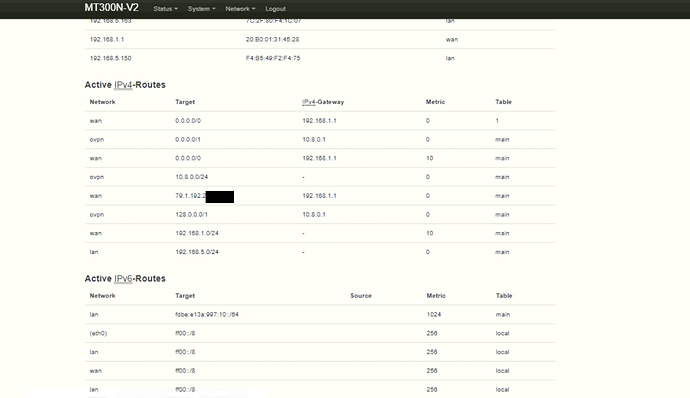
Also on server there is no route for 192.168.5.0/24 which is the client's LAN.
The same remarks apply for the client too.
could you please paste the ssh command to do it? I've done what you've asked
Yes, you should use iroute option in OpenVPN: https://community.openvpn.net/openvpn/wiki/RoutedLans
The ssh command to do what?
The OpenVPN configuration is not in the /etc/config/openvpn where it normally is.
You can try to look if it is inside /etc/openvpn and paste it here.
- You didn't answer my question why have you enabled the masquerade in the vpn zone.
- You didn't answer my question why have you enabled the masquerade in the vpn zone.
maybe a mistake, i don't know how to restore this value?
this the content about the .ovpn file that i'm currently using in client side: i mask the server ip with xxx
client
dev tun
proto udp
remote 79.1.192.xxx 1194
resolv-retry infinite
nobind
persist-key
persist-tun
auth SHA1
cipher BF-CBC
comp-lzo adaptive
nice 0
mute 5
verb 3
<ca>
-----BEGIN CERTIFICATE-----
MIIC/TCCAeWgAwIBAgIJAKNItkjp0PjhMA0GCSqGSIb3DQEBBQUAMBUxEzARBgNV
BAMMCk9wZW5WUE4gQ0EwHhcNMTkxMjA3MTgyMTUxWhcNMjkxMjA0MTgyMTUxWjAV
MRMwEQYDVQQDDApPcGVuVlBOIENBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIB
CgKCAQEAq6ldg/E63elmiieWBtYybYJI9Dm3Gov2+0V1XtuFuiz4pRUma7J0qEJD
S0M0BM6uaDttqZNEgS7kVr5xrfBzQ0TTmXdb3JVGw0W9J4nqJU3Hde5Bnj515wMT
bnPjdD1PTGhx8a5LrHj78jmtaakz5TkMJzmFww3QCOLsxpEzpykbTle7ZndsQC6C
Cqh/zWpInCvsRibe0gYhekVMhyC4qrWELN0Nw4wUepNDz5KhW3zkjlmtmk6DB+4R
TGpYYj8GmnZvBQpEYqg+fim5Krr554BDJHswzdOxPAFh3M3b4ZmPBBZJ84okaTtf
mkFQCSOb08DTWOLlk1s13lzjvRzVOwIDAQABo1AwTjAdBgNVHQ4EFgQUGHt2dapc
E4WFHOImp9PRKrF4I9QwHwYDVR0jBBgwFoAUGHt2dapcE4WFHOImp9PRKrF4I9Qw
DAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQUFAAOCAQEAKxKir8tWjuzmVOYpxOy+
MKWoX5dZLV/LTjnBedFWe9Kzw5n7IP2ElXV+IbRslvuwZrcrx06w8QNisRVlfi3m
xDUbhcWJBQQMz+SShI04dUJ/Jk983bDuwBDHSmUAIzZ6573KYZ1+WU2Hh0zEWxjD
MONs0sXw4h7XlbfoHOmM+5A+VAlK6m1p8NKXSTqx/ZtcwkuxD7iMykd1t5Dpk3jD
QHBWteKH8ZNyx9BoCWr9CEsSz0NZ4mngKm9WIk9zWR7uCsnSeQriXj9Mg7mVesdZ
S5Igtaf+VHJOSpPVOGu2DH5l/WRqv4eKHd2E81SJKRq8gFIL0Lcqm+mq3EO544u4
9A==
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
MIICqjCCAZICCQC9X0+rZXZVjDANBgkqhkiG9w0BAQUFADAVMRMwEQYDVQQDDApP
cGVuVlBOIENBMB4XDTE5MTIwNzE4MjIwNFoXDTI5MTIwNDE4MjIwNFowGTEXMBUG
A1UEAwwOT3BlblZwbiBjbGllbnQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
AoIBAQC/0x3Y2l4e3GlsSWm0qAzhPMCm5dzTqrtP3lu91gx9TeaqF4EVr0ClPIxk
vYeeNfmFn4EZFAp7jIMY/JU6KrX5eLX2ml/ZZXPoqdn2ArZQBloFHAzpApgGHVbb
ybUjopi9yPE+EPLPyvIUNPbFoRE2T1IlZ/wh8ys6VErHZdBqou8+sSeIV7qQ0Hus
5ZmsC7TsgCiJiRiMZiI5JkSp0fqpxAlhWumrlmBlhifRoRYlWSUXWXChv7oh35bT
Myembs4+TxVESM7Z4QEW73Wpb43PBazSgaWtIs2XM2g3Mmb0kKdlsAOC7Go2O+Dg
wd2aX53VZMvDGeASiMpFDPaotD9JAgMBAAEwDQYJKoZIhvcNAQEFBQADggEBABDh
dahG6f57v+mSCtdse0bEFZoVLv82N5xVI2sVkTwOwhe9W9ReYu4LJcGIIT35T0Ea
p6on8IlbWM0RcMu3HPEQZfQK1a12SAD1rCjpYnRuFEk2ukVCn/BsFIdKf1YSfN7d
qnD9/VZuwNnBWZbNxlqtitYgx0kbW2gBVMasIpQ8JZJXFLTh4wp10IEn8hza52uQ
6Xq0zrR4uUkyxfGbL7MvQ7ATIOgpUa2oAETTmmvhaeZOZn/1vCDbFMECRZwAtSm5
0gluJhEBLhqzKBETYS05SCCFr0Q7DTJg7/W6YkHlLs7lQd0GVmNHRRxQGG4ALd84
6fOz9KxPPVksE9FOvN8=
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQC/0x3Y2l4e3Gls
SWm0qAzhPMCm5dzTqrtP3lu91gx9TeaqF4EVr0ClPIxkvYeeNfmFn4EZFAp7jIMY
/JU6KrX5eLX2ml/ZZXPoqdn2ArZQBloFHAzpApgGHVbbybUjopi9yPE+EPLPyvIU
NPbFoRE2T1IlZ/wh8ys6VErHZdBqou8+sSeIV7qQ0Hus5ZmsC7TsgCiJiRiMZiI5
JkSp0fqpxAlhWumrlmBlhifRoRYlWSUXWXChv7oh35bTMyembs4+TxVESM7Z4QEW
73Wpb43PBazSgaWtIs2XM2g3Mmb0kKdlsAOC7Go2O+Dgwd2aX53VZMvDGeASiMpF
DPaotD9JAgMBAAECggEACKSxnpjQTuGtmmSAb9R2qBt9rseCuMLjp8ikJ5yieW7u
KtHeTiTUa92bkdp8ZuOVt7ClN4UQp9p/+bs/2hwckP4gbNkt4nTQ0TX+DTi4EEkI
+1v1NPaZ9QSTalnfYJit+zc3r41B85z4ZXKxf9wvE1xlniveT4VOeFVd/TgYOQXE
U6OzwRESkabu841MnafNh+rpR1dE0zLwLgB34z/kq1fmfoJYhSb8wrOndQA8qu7F
ujukrGyqQehopq79lDauBPgMBZzxlvYo2VeOpyHGUws7x7zXpQ9swuFgen14I1Vb
c0vE+8klov/pTE3q1x5DZBM/jKeNTwe67eNMgEingQKBgQD7Ey3cj6yvEPgmrB7H
xcepQeOMYi5f3LMvfujYMLoG784J8Kjpm9lTCjkIyCbw/Zw9usS2F0ui9D2wURZn
/B69B/SyAHuv/1sS2MXWYF7Bkx3rACYjrlJfQ9lKIgMO/el+HmLUyznSE5Y9rXtW
VAcO+taMssjBBr0ioU8wvCuhuQKBgQDDlmamiaGgi8PSDonyrDuezmCECBkU4rGz
nwygQJb2ToAyueB231IVGWE4S01w6KzPADjuM/4hiBShqs061hHNczRq7FUfNWXI
1dZmGJFojfQrU+hC+qWe7t1WW2jaMPQTSfhJizas7be672CcKhNVhXS0c9R2S0AV
xVuayauSEQKBgQDbst2nqaUej8fE90n732omBnzaA7O2uIWnIvMW8hRmK4LsmcUE
nhZeHoznzVSd/h2wunSVLe9GiVhNp7bmiOxQ1txcwiV5TQZhiIQdYbioxFYio7+7
6zczG0jRIM/yV2bwsCAlOiu/Utpd4CcT1HVUu1PwTCV1GrN30RVdfNrlKQKBgQCc
7MEzgV3CmCDnGm8n23SCeAcMKAsnrLLy8PuKYAg/WsCU8nncJlWPRCuypQhfPO/Z
rc3/oIuXj70t8QJ04GisNHCsES5Cue8OcjNw+uk/wBVV5h6GDuBvYisILJM17O0H
xOOG7kFSAfDV9VXINiIJDeiTGBQxTTL/xLc4u/ICYQKBgHhN+xFUewBsIWI/j90h
nqgQkithzum0XCqrbz4fSt+D4txw3U4zZOfynYPP4sVIfadqZF/L1hlrf4Q7bDWr
Nm2stxzjWqMvpdxM8gZujxM+2B4ra++zbPgGTEnm5SmbtmB69t9Ri682JVvXVcb6
0HCRWLVdcjAtHANPlKSODW7q
-----END PRIVATE KEY-----
</key>
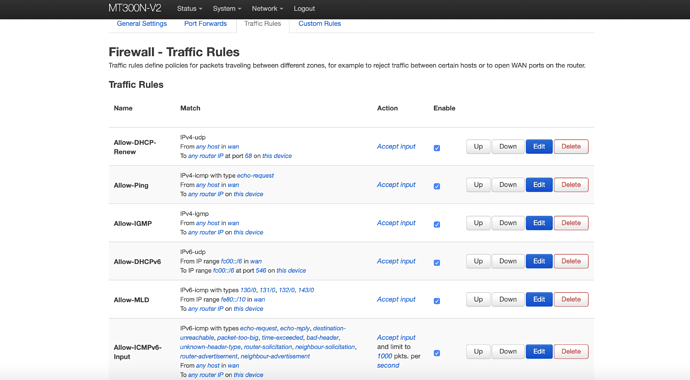
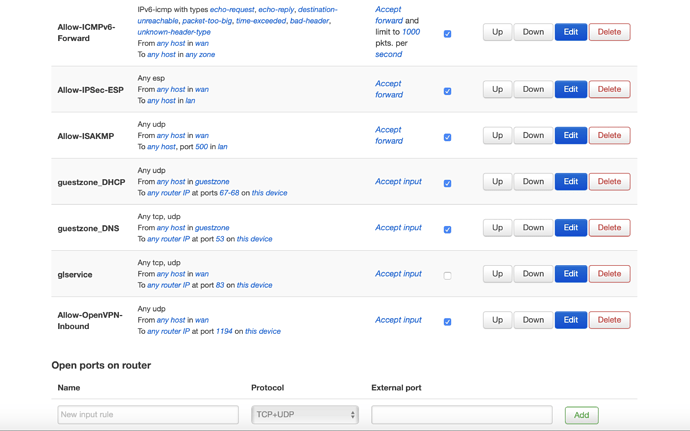
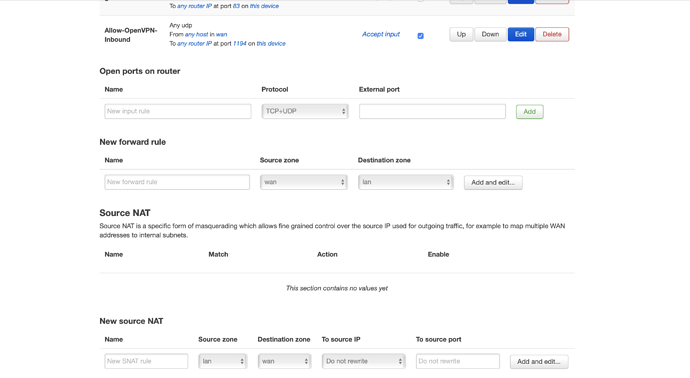
He asks you about firewall configuration of zones. See firewall configuration. I suppose, you have 'masq' option on vpn-zone on client, it should be only on client.
I've answered you, what you should do.
i become crazy  so many post and no idea to fix it i think that it's easy for a mod or someone developer about open wrt firmware while it's so hard for all to fix it... maybe you also don't have any idea to a working solution?
so many post and no idea to fix it i think that it's easy for a mod or someone developer about open wrt firmware while it's so hard for all to fix it... maybe you also don't have any idea to a working solution?
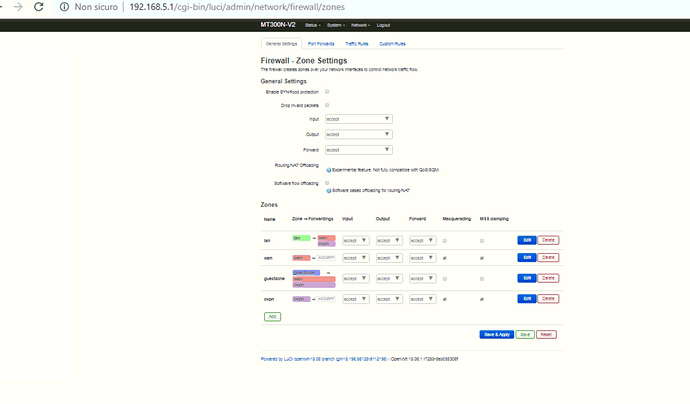
this is the firewall client config... i put everything accept ....
Is it client, everything is OK. The question of @trendy was about 'masq' option on server. It should not be set on server. But my recommendation is correct, you haven't done it. So I don't understand your question. The problem is in routing.
could you please explain me again in different words? i'm a noob in it and it's quite hard to apply your suggestion.
- Check option 'masq' in config or tick 'Masquerading' on web-interface on server near vpn-zone, it should NOT be set (@trendy).
- See manual by link above, you should do ONLY ON SERVER:
2.a Modify server config for OpenVPN.
2.b Create ccd directory in /etc/openvpn
2.c Create file with name of client in ccd directory, and insert string containing iroute in it.
-
ok I've unchecked 'Masquerading' near the vpn but still the same also rebooted both
-
i've done server by wizard mode, and first to do a restore and start it in a manual way i dont'know... because vpn is working at 90% i have internet access from client lan also when i ping server lan side, if i check my public static ip from client lan side i see the correct one (server side public static ip) the only thing that is wrong is that i can't ping client lan side that's all.