Firmware Version: OpenWrt 19.07.2 r10947-65030d81f3 / LuCI openwrt-19.07 branch git-20.103.29170-9bb1624
Model: TP-Link TL-WR1043ND v2
Hello.
I have this problem, when I restart the router I lose the configuration of some zones in the firewall.
For example:
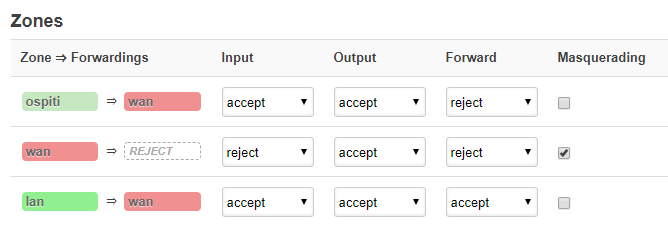
config defaults 'defaults'
option forward 'REJECT'
option input 'ACCEPT'
option output 'ACCEPT'
option syn_flood '1'
config rule 'rule1'
option dest_port '68'
option family 'ipv4'
option name 'Allow-DHCP-Renew'
option proto 'udp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule2'
option family 'ipv4'
option icmp_type 'echo-request'
option name 'Allow-Ping'
option proto 'icmp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule3'
option family 'ipv4'
option name 'Allow-IGMP'
option proto 'igmp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule4'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option name 'Allow-DHCPv6'
option proto 'udp'
option src 'wan'
option src_ip 'fc00::/6'
option target 'ACCEPT'
config rule 'rule5'
option family 'ipv6'
list icmp_type '131/0'
list icmp_type '130/0'
list icmp_type '143/0'
list icmp_type '132/0'
option name 'Allow-MLD'
option proto 'icmp'
option src 'wan'
option src_ip 'fe80::/10'
option target 'ACCEPT'
config rule 'rule6'
option family 'ipv6'
list icmp_type 'destination-unreachable'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'echo-reply'
list icmp_type 'neighbour-solicitation'
list icmp_type 'echo-request'
list icmp_type 'neighbour-advertisement'
list icmp_type 'packet-too-big'
list icmp_type 'router-advertisement'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
option limit '1000/sec'
option name 'Allow-ICMPv6-Input'
option proto 'icmp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule7'
option dest '*'
option family 'ipv6'
list icmp_type 'destination-unreachable'
list icmp_type 'echo-request'
list icmp_type 'packet-too-big'
list icmp_type 'unknown-header-type'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'echo-reply'
option limit '1000/sec'
option name 'Allow-ICMPv6-Forward'
option proto 'icmp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule8'
option dest 'lan'
option name 'Allow-IPSec-ESP'
option proto 'esp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule9'
option dest 'lan'
option dest_port '500'
option name 'Allow-ISAKMP'
option proto 'udp'
option src 'wan'
option target 'ACCEPT'
config include 'include1'
option path '/etc/firewall.user'
config zone 'zone3'
option forward 'REJECT'
option input 'ACCEPT'
option name 'ospiti'
option network 'ospiti'
option output 'ACCEPT'
config zone 'zone2'
option forward 'REJECT'
option input 'REJECT'
option masq '1'
option name 'wan'
option network 'wan wan6'
option output 'ACCEPT'
config zone 'zone1'
option forward 'ACCEPT'
option input 'ACCEPT'
option name 'lan'
option network 'lan'
option output 'ACCEPT'
config forwarding 'forwarding1'
option dest 'wan'
option src 'lan'
config forwarding
option dest 'wan'
option src 'ospiti'
After reboot:
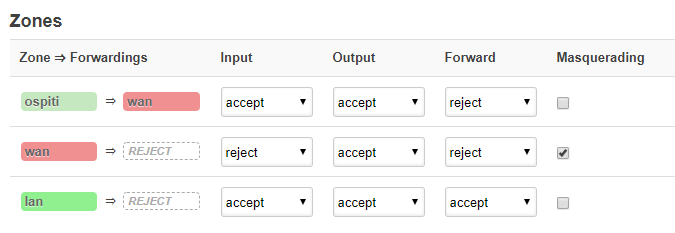
config defaults 'defaults'
option forward 'REJECT'
option input 'ACCEPT'
option output 'ACCEPT'
option syn_flood '1'
config rule 'rule1'
option dest_port '68'
option family 'ipv4'
option name 'Allow-DHCP-Renew'
option proto 'udp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule2'
option family 'ipv4'
option icmp_type 'echo-request'
option name 'Allow-Ping'
option proto 'icmp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule3'
option family 'ipv4'
option name 'Allow-IGMP'
option proto 'igmp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule4'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option name 'Allow-DHCPv6'
option proto 'udp'
option src 'wan'
option src_ip 'fc00::/6'
option target 'ACCEPT'
config rule 'rule5'
option family 'ipv6'
list icmp_type '131/0'
list icmp_type '130/0'
list icmp_type '143/0'
list icmp_type '132/0'
option name 'Allow-MLD'
option proto 'icmp'
option src 'wan'
option src_ip 'fe80::/10'
option target 'ACCEPT'
config rule 'rule6'
option family 'ipv6'
list icmp_type 'destination-unreachable'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'echo-reply'
list icmp_type 'neighbour-solicitation'
list icmp_type 'echo-request'
list icmp_type 'neighbour-advertisement'
list icmp_type 'packet-too-big'
list icmp_type 'router-advertisement'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
option limit '1000/sec'
option name 'Allow-ICMPv6-Input'
option proto 'icmp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule7'
option dest '*'
option family 'ipv6'
list icmp_type 'destination-unreachable'
list icmp_type 'echo-request'
list icmp_type 'packet-too-big'
list icmp_type 'unknown-header-type'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'echo-reply'
option limit '1000/sec'
option name 'Allow-ICMPv6-Forward'
option proto 'icmp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule8'
option dest 'lan'
option name 'Allow-IPSec-ESP'
option proto 'esp'
option src 'wan'
option target 'ACCEPT'
config rule 'rule9'
option dest 'lan'
option dest_port '500'
option name 'Allow-ISAKMP'
option proto 'udp'
option src 'wan'
option target 'ACCEPT'
config include 'include1'
option path '/etc/firewall.user'
config zone 'zone3'
option forward 'REJECT'
option input 'ACCEPT'
option name 'ospiti'
option network 'ospiti'
option output 'ACCEPT'
config zone 'zone2'
option forward 'REJECT'
option input 'REJECT'
option masq '1'
option name 'wan'
option network 'wan wan6'
option output 'ACCEPT'
config zone 'zone1'
option forward 'ACCEPT'
option input 'ACCEPT'
option name 'lan'
option network 'lan'
option output 'ACCEPT'
config forwarding 'forwarding1'
option dest 'wan'
option src 'ospiti'
Any suggestions?
Thanks,