Hi
I need help with setting up OpenWrt (18.06.2) with a special setup. I managed to get working what I needed but my network now is far too exposed as it would be acceptable.
I've set up my own mail server, which leads to the need to get the external ip known for incoming connections and to communicate to the outside with the static public ip of my gateway. As I didn't get a static public Ip at home, I've set up n VPS in Chicago.
<external ip> VPS <wg0 --------------------- wg1 > OpenWrt <zone mail> <mail server>
XX.XX.XX.X6 192.168.47.71 192.168.47.1 192.168.48.1 192.168.48.30 + 31
The VPS is forwarding anything coming in from external on port 25,465 to 192.168.48.31, without SNAT, just with DNAT to get the correct routing.
* filter
# Keep all established connections
-A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
-A FORWARD -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
# Allow all outbound traffic
-A OUTPUT -j ACCEPT
# Allow all inbout and forward from wg0
-A INPUT -i wg0 -j ACCEPT
-A FORWARD -i wg0 -j ACCEPT
# Open TCP ports for forwarding of mail
# smtp
-A FORWARD -i eth0 -o wg0 -p tcp --syn -m multiport --dports 25,465 -m conntrack --ctstate NEW -j ACCEPT
# Drop all other incoming/forward traffic
-A INPUT -j REJECT
-A FORWARD -j DROP
*nat
-A POSTROUTING -o eth0 -j MASQUERADE
# routing for mail
# smtp
-A PREROUTING -i eth0 -p tcp -m multiport --dports 25,465 -j DNAT --to-destination 192.168.48.31
#-A POSTROUTING -d 192.168.48.31 -o wg0 -p tcp -m multiport --dports 25,465,587 -j SNAT --to-source 192.168.47.71
To get the direction back, I've set up the mail server with a second ip (192.168.48.31) which is used for any outgoing smtp communication. To get this to the correct gateway, I've added on the OpenWrt
ip route add default via 192.168.47.71 dev wg1 table 210
ip rule add from 192.168.48.31 lookup 210 prio 210
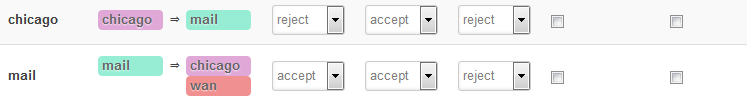
This works fine, as long as I expose the mail zone fully on my OpenWrt. At the moment, it's this:
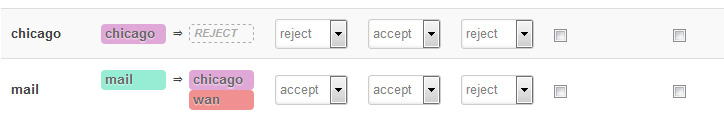
I now want to activate the firewall on the mail zone so that I have control over what's allowed incoming from Chicago and block everything else. Something like this:
With only opening or forwarding ports 25,465 to the mail server at 192.168.48.31 on the OpenWrt. But still with having the external IP as source and with outgoing communication from 192.168.48.31 via the Chicago gateway.
How do I achieve this with OpenWrt?
Basically it's clear what needs to be done on the OpenWrt:
the routing as described above
allow all related, established from wg1 to 192.168.48.31
allow new from wg1 with port 25,465 to 192.168.48.31
allow all from 192.168.48.31 to wg1
No NAT, but possibly conntrack?
If I want to do it with forwards
the routing as described above
allow all related, established from wg1
allow new from wg1 with port 25,465 to router forward to 192.168.48.31 (DNAT, no SNAT)
allow all from 192.168.48.31 to wg1
No NAT, but possibly conntrack?
Anything missing? I may test it with iptables rules on the custom rules tab. But ain't there way to do it with UCI or LuCi options?
Any help welcome. Thank you