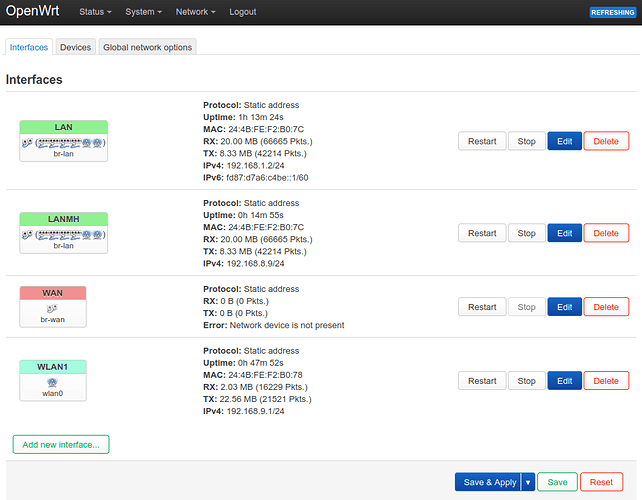
I have the following set-up
Internet <-- House 1 (192.168.8.0) <---WiFi---> House 2 (192.168.8.0) <---WiFi ---> House 3 (192.168.8.0) --> Internet
I'd like to install a network device in House 2 that connects to the WiFi bridge to/from House 3 and the local LAN in the house and filters out DHCP traffic. The reason is that I need to make sure devices in House 1 and 2 get an IP address only from the LTE Router in House 1 and devices in House 3 only get an IP address from the LTE Router in House 3. The next step is an mwan3 set-up (not relevant here).
I'm using an Asus RT-AC85P running OpenWrt 21.02.3. I'm aware that I'll have a (kind of) slow link, as all the traffic needs to pass the CPU for filtering. That's okay, it's only LTE uplinks and almost zero inter LAN traffic.
Setup Option A
I've tried a simple set-up with one bridge device for all LAN and the WAN ports. One LAN cable is in the LAN1 and one (to the WiFi bridge) in the WAN port. Traffic flows fine, but I can't filter any traffic, despite following Firewall Bridge doc. I can neither get iptables rules nor ebtables rules to filter DHCP traffic.
Here are the firewall rules I'm using:
config rule
option name 'Deny DHCP to server'
list proto 'udp'
option src 'lan'
option dest_port '67'
option target 'DROP'
option dest 'lan'
config rule
option name 'Deny DHCP to client'
list proto 'udp'
option src 'lan'
option dest_port '68'
option target 'DROP'
option dest 'lan'
I also tried ebtables rules with the MAC address of the DHCP server, but that doesn't work either. It seems like traffic between the ports never reaches the CPU.
After reading firwall on the same network, I switch to a VLAN based config:
Setup Option B
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
option stp '1'
config device
option name 'wan'
option macaddr '24:4b:fe:f2:b0:78'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'lan1'
config bridge-vlan
option device 'br-lan'
option vlan '2'
list ports 'lan2'
config bridge-vlan
option device 'br-lan'
option vlan '3'
list ports 'lan3'
config bridge-vlan
option device 'br-lan'
option vlan '4'
list ports 'lan4'
config device
option type 'bridge'
option name 'br-vlan'
list ports 'br-lan.1'
list ports 'br-lan.4'
option stp '1'
config interface 'brvlan'
option proto 'static'
option device 'br-vlan'
option ipaddr '192.168.8.9'
option netmask '255.255.255.0'
option gateway '192.168.8.1'
list dns '8.8.8.8'
list dns '8.8.4.4'
So basically two Bridge devices:
- br-lan with all lanX ports and the Bridge VLAN Filtering tab set to create one VLAN per LAN port.
- br-vlan with only the VLANs for port 1 & 4 (br-lan.1, br-lan.4)
and then one Interface brvlan with the IP address 192.168.8.9.
From the Router I can ping the upstream LTE (192.168.8.1) in House 1 and the Devices in House 3. All devices can ping the Router. But they can't ping each other. Running iptables -F doesn't help either.
From running wireshark, I can see that the ARP requests my Laptop sends remain unanswered.
$ ip route
default via 192.168.8.1 dev br-vlan
192.168.8.0/24 dev br-vlan scope link src 192.168.8.9
$ ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1504 qdisc fq_codel state UP qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
inet6 fe80::264b:feff:fef2:b07c/64 scope link
valid_lft forever preferred_lft forever
3: wan@eth0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
4: lan1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
5: lan2@eth0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue master br-lan state LOWERLAYERDOWN qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
6: lan3@eth0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue master br-lan state LOWERLAYERDOWN qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
7: lan4@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
9: wlan1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
13: wlan0: <BROADCAST,MULTICAST> mtu 1500 qdisc noqueue state DOWN qlen 1000
link/ether 24:4b:fe:f2:b0:78 brd ff:ff:ff:ff:ff:ff
23: br-vlan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
inet 192.168.8.9/24 brd 192.168.8.255 scope global br-vlan
valid_lft forever preferred_lft forever
inet6 fe80::264b:feff:fef2:b07c/64 scope link
valid_lft forever preferred_lft forever
24: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
inet6 fe80::264b:feff:fef2:b07c/64 scope link
valid_lft forever preferred_lft forever
25: br-lan.1@br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-vlan state UP qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
26: br-lan.4@br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-vlan state UP qlen 1000
link/ether 24:4b:fe:f2:b0:7c brd ff:ff:ff:ff:ff:ff
Questions
So two questions, solving one is enough ![]()
- Any idea why filtering in my set-up with one bridge for all LAN & WAN port doesn't work?
- How I can configure OpenWrt to pass my ARP requests through the bridge from LAN port 1 to 4?
- Is the bridge within bridge a problem? How can I set-up bridged VLANs without that?