I don't think you understand what -o does...or should I say...what it won't do...
I need to know if these are real rules working now, so please be clear...especially since there are easier ways in the manual (and more secure) than this - to simply block kids...and because wan isn't a Linux PHY named on default OpenWrt for WAN...eth0.2 is the most common across devices with a built-in switch...and since your rule will only cover that PHY, and not the WAN zone (as I noted when explaining the exemption).
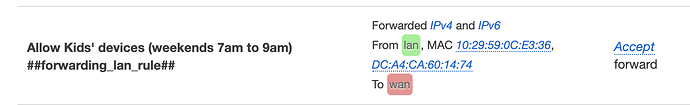
Yes there are, I listed one:
Given you mention parental controls again, I'll digress on the other inquires...can you simply explain why none of the parental control rules work for you (i.e. the ones that follow the instructions in the Wiki or in the forum)?
I only read your reasoning is that you want it before any established,related rules - but I already described one problem that's likely an undesired security consequence of what your rule as-written - could do - contrary to your TRUE desires (i.e. it WON'T block the kid's device).
https://forum.openwrt.org/search?q=parental%20controls
- If your kid used a UDP-based VPN e.g. Tunsafe with Wireguard client...I think this rule wouldn't block it...
- nor most UDP-based A/V chats, video streams, etc...
- also if you made a VPN for the router, used Wireless WAN, etc. and forgot to edit that rule, the kids would still have Internet (because it didn't cover Zone WAN thru chains; but only the current interface for the ISP connection - this is the another security issue - making rules on the same layer of abstraction...exempting PHYs from a Zone)
...but I'll respectfully digress on that too so you can answer the relevant inquires about the priority, currently working rule and security implications (assuming you actually added/tested the rules as stated).
(I think teaching kids to be good netizens is better than this.)