Yes. I would actually recommend using the guest wifi tutorial to setup the first network. Once that is configured, it will be WiFi only. But we can then add Ethernet by using VLANs at that point. Then, you can repeat if you want multiple networks (lan, guest, iot).
Solution provided by @ncompact is the correct one and scales to any number of dumb AP's
Although I would argue that clients in guest and iot segments have no business accessing dumb AP itself in any way.
So there is no need to:
- make AP itself part of guest/iot VLANs (local=0)
- configure IP's for guest/iot interfaces (proto=none)
- allow traffic to pass between iot/guest wireless clients (isolate=1 and bridge_isolate '1')
/etc/config/network
...
config bridge-vlan
option device 'br-lan'
option vlan '20'
option local '0'
list ports 'lan4:t'
config bridge-vlan
option device 'br-lan'
option vlan '30'
option local '0'
list ports 'lan4:t'
....
config interface 'iot'
option device 'br-lan.20'
option proto 'none'
config interface 'guest'
option device 'br-lan.30'
option proto 'none'
/etc/config/wireless
...
config wifi-iface 'myguest'
option device 'radio0'
option ifname 'phy0-guest'
option network 'guest'
option isolate '1'
option bridge_isolate '1'
option mode 'ap'
option ssid 'myguest'
config wifi-iface 'myguest5'
option device 'radio1'
option ifname 'phy1-guest'
option network 'guest'
option isolate '1'
option bridge_isolate '1'
option mode 'ap'
option ssid 'myguest5'
...
hey everyone, I will try and implement this during the next days. Will keep you updated.
So I have tried to set up the IOT network and used the guide above to the letter. But connecting to it I have no internet connection, which seems weird.
From what I see the setup in /etc/config/network and firewall is also pretty much identical, although on my router there are a lot more rules for the guest network.
Can somebody help: why does this not work?
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd93:6410:07a0::/48'
config device 'dev_wan'
option name 'eth2'
config interface 'wan'
option device 'eth2'
option proto 'dhcp'
option hostname 'turris'
option ipv6 '1'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
config device 'br_lan'
option name 'br-lan'
option type 'bridge'
list ports 'lan0'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ip6ifaceid 'eui64'
option ip6addr 'fe80::1'
config device 'br_guest_turris'
option name 'br-guest-turris'
option type 'bridge'
option bridge_empty '1'
config interface 'guest_turris'
option enabled '1'
option proto 'static'
option device 'br-guest-turris'
option ipaddr '10.111.222.1'
option netmask '255.255.255.0'
option ip6assign '64'
config device
option bridge_empty '1'
option type 'bridge'
option name 'br-iot'
config interface 'iot'
option device 'br-iot'
option proto 'static'
option ipaddr '10.0.0.1'
option netmask '255.255.255.0'
and
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vpn'
config zone 'wan'
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option sentinel_minipot '1'
option sentinel_dynfw '1'
option sentinel_fwlogs '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config rule 'wan_ssh_turris_rule'
option name 'wan_ssh_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '22'
option proto 'tcp'
option src 'wan'
config rule 'wan_http_turris_rule'
option name 'wan_http_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '80'
option proto 'tcp'
option src 'wan'
config rule 'wan_https_turris_rule'
option name 'wan_https_turris_rule'
option enabled '0'
option target 'ACCEPT'
option dest_port '443'
option proto 'tcp'
option src 'wan'
config rule 'turris_wan_6in4_rule'
option enabled '0'
config rule 'turris_wan_6to4_rule'
option enabled '0'
config include 'bcp38'
option type 'script'
option path '/usr/lib/bcp38/run.sh'
config include
option path '/etc/firewall.user'
config zone 'guest_turris'
option enabled '1'
option name 'tr_guest'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
list network 'guest_turris'
config forwarding 'guest_turris_forward_wan'
option enabled '1'
option name 'guest to wan forward'
option src 'tr_guest'
option dest 'wan'
config rule 'guest_turris_dns_rule'
option name 'guest dns rule'
option src 'tr_guest'
option proto 'tcpudp'
option dest_port '53'
option target 'ACCEPT'
config rule 'guest_turris_dhcp_rule'
option name 'guest dhcp rule'
option src 'tr_guest'
option proto 'udp'
option src_port '67-68'
option dest_port '67-68'
option target 'ACCEPT'
config rule 'guest_turris_Allow_DHCPv6'
option src 'tr_guest'
option proto 'udp'
option src_ip 'fe80::/10'
option src_port '546-547'
option dest_ip 'fe80::/10'
option dest_port '546-547'
option family 'ipv6'
option target 'ACCEPT'
config rule 'guest_turris_Allow_MLD'
option src 'tr_guest'
option proto 'icmp'
option src_ip 'fe80::/10'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
config rule 'guest_turris_Allow_ICMPv6_Input'
option src 'tr_guest'
option proto 'icmp'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
{ ...redacted for readability - wireguard rules... }
config zone
option name 'iot'
option forward 'REJECT'
list network 'iot'
option output 'ACCEPT'
option input 'REJECT'
config forwarding
option dest 'wan'
option src 'iot'
config rule
option dest_port '53'
option src 'iot'
option name 'Allow-DNS-iot'
option target 'ACCEPT'
config rule
option dest_port '67'
option src 'iot'
option name 'Allow-DHCP-iot'
option target 'ACCEPT'
you can run this command via ssh and post the command output:
for x in /etc/config/*; do uci show "${x##*/}" >/dev/null || echo "$x is broken"; done
do you confirm that the router has internet connectivity?
ping -c 1 8.8.8.8; traceroute -n 8.8.8.8
I have not reviewed your config in detail, but the way it is setup currently will work for WiFi on that local device only. Do you want to extend it via Ethernet to other APs? If so, on what port(s)?
Yes, correct. I thought step by step might make sense here considering that I have no internet access on the new 'IOT' network.
This should then be extended to the other APs via LAN4. However, as described above there is a managed switch between port 4 and the other APs.
@ncompact: yes, I can confirm internet connectivity for the device overall, as it is my main router and I use it for my other devices.
Just in case I will restart the router when at home - sometimes it's the little things that get you.
I’m not seeing any obvious reason the iot network would not be working. How are you testing?
(some hints, from another thread, maybe useful)
Simple rules:
-
T means VLAN is tagged on the wire
-
u* (in OpenWrt) or UP (in a network switch) means untagged on the wire.
-
If you Tag a VLAN on a port in OpenWRT, then cable that port to a switch, you should also Tag the VLAN on the switch port. And vice versa.
-
Local in OpenWRT means create a virtual device to access the VLAN.
- You can create an Interface in OpenWRT on top of this virtual device.
- You can select that Interface in wifi_xx -> Network. This will bridge the wifi network with the underlying virtual device for that Interface.
- You can assign an IP address and subnet mask on that Interface. OpenWrt will then be able to act as a router in the VLAN.
- Devices in the VLAN can (but doesn't have to) use that IP address as their gateway. If they do, you have what many call a "routed" rather than a "dumb ap" or "bridged" setup on the OpenWrt AP.
- Once OpenWrt has an IP in the VLAN, you can also configure it to be a DHCP and/or DNS server there.
-
UP in switch also means making a physical port where you can attach a device which is not configured for VLANs into the VLAN (since frames are untagged on wire), for example a laptop.
-
Attaching a device such as a laptop into the VLAN can be useful to
pingsomething on the other end / far side of the VLAN. (You can set a static IP on the attached device, if DHCP services on the VLAN is not configured yet.) -
Often it's a good idea to be connected to the management interface GUI / CLI via another VLAN than the one you are creating or modifying.
I have connected both with my phone and my laptop to the new network and cannot reach any webpage.
Weird thing though: both ping 8.8.8.8 and traceroute work!
Maybe an issue with the DNS resolution in the firewall rules?
Hey, I have run this command, but nothing shows...
Yes, certainly a DNS issue. But IoT does have a DNS allow rule:
Let's see
cat /etc/config/dhcp
ok
check if there are any inconsistencies in the "uci" system, if it doesn't show anything everything is ok (just to verify that the configuration files are "uci" correct, this does not preclude other errors)
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option port '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
option force '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
list dhcp_option '6,192.168.1.1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
option force '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest_turris'
option interface 'guest_turris'
option ignore '0'
option start '100'
option limit '150'
option leasetime '3600'
option dhcpv6 'server'
option ra 'server'
list dhcp_option '6,10.111.222.1'
option force '1'
config host
option mac '5C:62:8B:39:94:8E'
option ip '192.168.1.150'
option name 'C110'
option leasetime 'infinite'
option dns '1'
config host
option mac 'E4:5F:01:5C:41:1F'
option name 'homeassistant'
option ip '192.168.1.178'
config host
option mac '90:09:D0:43:76:63'
option name 'SynNas'
option ip '192.168.1.167'
config host
option mac '34:98:7A:C2:00:83'
option name 'tasmotaHeizungOG-0131'
option ip '192.168.1.237'
config host
option mac '80:64:6F:8F:40:7F'
option name 'tasmotaHeizungDG-0127'
option ip '192.168.1.217'
config host
option mac '34:98:7A:C0:15:15'
option name 'tasmotaHeizungEG-5397'
option ip '192.168.1.196'
config host
option mac '08:3A:8D:D0:0F:05'
option name 'SmartMeter-3845'
option ip '192.168.1.169'
config host
option mac '54:F2:9F:12:FD:C9'
option name 'DTUBI-414392317396'
option ip '192.168.1.123'
config dhcp 'iot'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'iot'
Just to be clear, the issue is with the IoT network, correct?
correct, and with iot only
What DNS does your device try to use when connected to the iot network?
remove this ... (at most set the port to default 53)
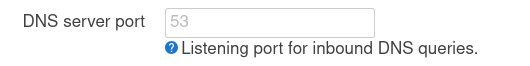
oh... good catch!
yeah, that did the trick (writing while connected to the 'iot' wifi). Weird though: why would the regular guest access work then?