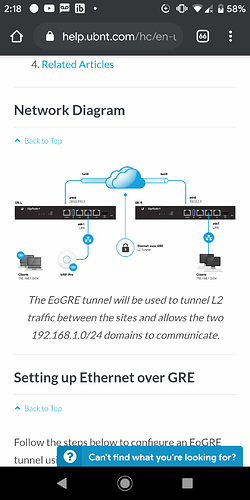
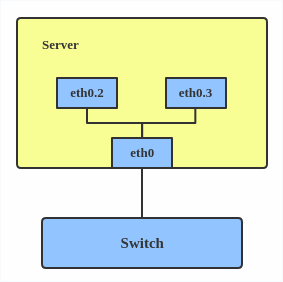
Not so bad.
I'm going to pick two VLAN numbers that should be small enough not to complicate config with switch drivers that are limited to 16 VLANs, and high enough to avoid "common" reserved VLANs in OpenWrt and consumer-grade, managed switches:
- VLAN 10 -- "LAN"
- VLAN 11 -- GRE tunnel participants
VLAN 10, conceptually, needs to handle the 192.168.1.0/24 subnet, including:
- EdgeRouter Ethernet "LAN" ports
- Switch “LAN” ports
- DIR "LAN" Ethernet ports
- DIR "LANSSID" wireless
- EX3700 "LAN" Ethernet ports
- EX3700 "LANSSID" wireless
If all of the above are logically bridged together, you've got your "LAN" on the right SSIDs and available untagged where you need it.
Now, to make a "wire" between the EX3700 and the "LAN" bridge...
VLAN 11, needs to handle the GRE tunnel traffic. I'll pick from the Class B Private Address Space for clarity, 172.16.0.0/30 (four hosts)
- EdgeRouter Ethernet port
- DIR Ethernet port
- DIR "GRESSID"
If you follow these line-by-line, you will probably lose connectivity at many points. Create a management VLAN first, or work though a plan on how to make the changes without locking yourself out!
Let’s get it “wired up” first
On the EdgeRouter
- Configure the LAN bridge or interface to involve eth1.10 (instead of just eth1)
- Configure eth1.11 for 172.16.0.1/30
- On the in-built switch, configure the “trunk” port to be
- VLAN 10 tagged
- VLAN 11 tagged
- PVID 4095 (blackhole)
- Reject untagged and unconfigured VLANs (if possible)
- On the in-built switch, configure the “LAN” ports to be
- VLAN 10 untagged
- PVID 10
- Reject unconfigured VLANs (if possible)
On the switch
- Configure VLAN 10 and VLAN 11
- Configure the EdgeRouter’s port to be
- VLAN 10 tagged
- VLAN 11 tagged
- PVID 4095 (blackhole)
- Reject untagged and unconfigured VLANs (if possible)
- Configure the DIR’s port to be
- VLAN 10 tagged
- VLAN 11 tagged
- PVID 4095 (blackhole)
- Reject untagged and unconfigured VLANs (if possible)
- Configure the “LAN” ports to be
- VLAN 10 untagged
- PVID 10
- Reject unconfigured VLANs (if possible)
On the DIR
- Configure the LAN/LANSSID bridge to involve eth0.10
- Create GRESSID as an AP, with a “sufficiently large” MTU, bridging over eth0.11
- For now, set its IP to 172.16.0.2/30, confirming that the MTU (
ip link) is still sufficiently large for GRE traffic
- Configure its built-in switch for VLAN 10 and VLAN 11
- Configure the DIR’s switch port that connects to the central switch to be
- VLAN 10 tagged
- VLAN 11 tagged
- PVID 4095 (blackhole)
- Reject untagged and unconfigured VLANs (if possible)
Cabling
- Run an Ethernet cable from the EdgeRouter’s “trunk” port to the central switch’s “EdgeRouter” port
- Run an Ethernet cable from the DIR’s “trunk” port to the central switch’s “DIR” port
You now should be able to ping:
- 172.16.0.1 <==> 172.16.0.2
- 192.168.1.1 <==> 192.168.1.2
Set up the wireless link
On the EX3700
- Set up a new interface as a client of the DIR’s GRESSID with the static/fixed address of 172.16.0.3/30 and a sufficiently large MTU
- Set its LAN bridge for 192.168.1.3/32 (which already includes LANSSID)
You now should be able to ping among 172.16.0.1, 172.16.0.2, and 172.16.0.3
Set up the GRE tunnel
Now that you can ping 172.16.0.3 from 172.16.0.1, you can configure the GRE L2 tunnel portals on the EdgeRouter and the EX3700.
The DIR is “invisible” in the setup.
- On the EdgeRouter, add gre0.10 to the “LAN” bridge
- On the EX3700, add gre4t-xxx.10 to the “LAN” bridge
I think that should do it!
Finishing touches would be to make sure there is no forwarding permitted between the LAN and the GRE subnets. You may need firewall rules at each of the three routers.
You can remove 172.16.0.2 from the DIR once you’re confident everything is up and running.