Hello ,
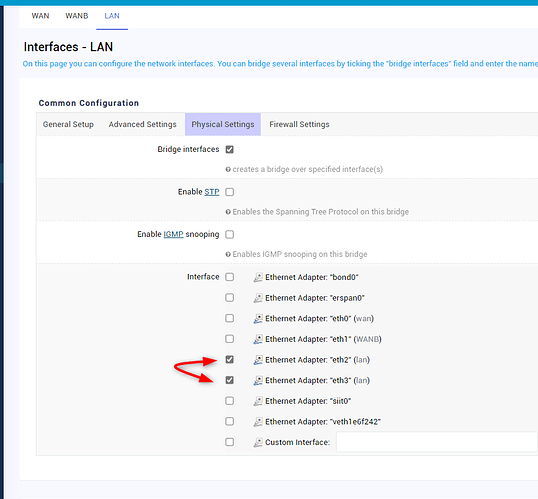
I have bridge eth 2 and eth 3 port to be on the same lan ip group. when clients join the network through wifi of eth2 or eth 3, both receive the same ip subnet.
however, i wasn't able to ping client connected using eth2 from client connected using eth3 and vice versa.
is it because of my firewall?
cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdab:0ac0:e69f::/48'
option packet_steering '1'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth2 eth3'
option ipaddr '192.168.7.1'
config interface 'wan'
option ifname 'eth0'
option proto 'dhcp'
option metric '10'
option delegate '0'
config interface 'WANB'
option proto 'dhcp'
option ifname 'eth1'
option delegate '0'
option metric '20'
cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option fullcone '1'
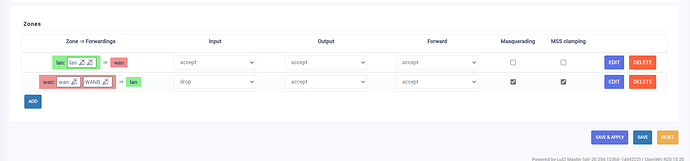
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'DROP'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'DROP'
option network 'wan WANB'
option forward 'ACCEPT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'zerotier'
option type 'script'
option path '/etc/zerotier.start'
option reload '1'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'adbyby'
option type 'script'
option path '/var/etc/adbyby.include'
option reload '1'
config rule 'adblock'
option name 'adblock'
option target 'DROP'
option src 'wan'
option proto 'tcp'
option dest_port '8118'
config include 'ipsecd'
option type 'script'
option path '/etc/ipsec.include'
option reload '1'
config rule 'ike'
option name 'ike'
option target 'ACCEPT'
option src 'wan'
option proto 'udp'
option dest_port '500'
config rule 'ipsec'
option name 'ipsec'
option target 'ACCEPT'
option src 'wan'
option proto 'udp'
option dest_port '4500'
config rule 'ah'
option name 'ah'
option target 'ACCEPT'
option src 'wan'
option proto 'ah'
config rule 'esp'
option name 'esp'
option target 'ACCEPT'
option src 'wan'
option proto 'esp'
config include 'passwall'
option type 'script'
option path '/var/etc/passwall.include'
option reload '1'
config include 'passwall_server'
option type 'script'
option path '/var/etc/passwall_server.include'
option reload '1'
config include 'softethervpn'
option type 'script'
option path '/usr/share/softethervpn/firewall.include'
option reload '1'
config include 'v2ray_server'
option type 'script'
option path '/usr/share/v2ray_server/firewall.include'
option reload '1'
config rule 'kms'
option name 'kms'
option target 'ACCEPT'
option src 'wan'
option proto 'tcp'
option dest_port '1688'
config include 'openclash'
option type 'script'
option path '/var/etc/openclash.include'
option reload '1'
config include 'shadowsocksr'
option type 'script'
option path '/var/etc/shadowsocksr.include'
option reload '1'
config include 'wrtbwmon'
option type 'script'
option path '/etc/wrtbwmon.include'
option reload '1'
config include 'mia'
option type 'script'
option path '/etc/mia.include'
option reload '1'
config rule 'openvpn'
option name 'openvpn'
option target 'ACCEPT'
option src 'wan'
option proto 'tcp udp'
option dest_port '1194'
config include 'unblockmusic'
option type 'script'
option path '/var/etc/unblockmusic.include'
option reload '1'
config forwarding
option dest 'lan'
option src 'wan'
config forwarding
option dest 'wan'
option src 'lan'
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option nonwildcard '1'
option localservice '1'
option filter_aaaa '1'
option port '53'
list server '127.0.0.1#5351'
option noresolv '1'
config dhcp 'lan'
option interface 'lan'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option ra_management '1'
option start '30'
option limit '200'
option leasetime '30m'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config srvhost
option srv '_vlmcs._tcp'
option target 'OpenWrt'
option port '1688'
option class '0'
option weight '100'