I'm afraid VLANs don't work that way.
First of all, you cannot mix tagged and untagged frames on the same port using this hardware. If you want to assign more than one VLAN to a specific port, all these VLANs must be set as tagged. The device connected to that port must be VLAN-aware. It could be a managed switch, or a PC with a NIC, whose drivers support 802.1q VLAN tagging.
In your config VLAN 1 (lan) is assigned to ports 3,4 and 5, VLAN 2 (wan) is assigned to port 1 and VLAN 3 (SmartDNS) is assigned to port 2. Because most end devices work with untagged frames, here only the router’s CPU port (0t) uses tagged frames.
If you need more wired ports for VLAN 3, you have three options.
A) You could assign one more port to VLAN 3. You’ll have 2 wired ports (4 and 5) for lan and 2 ports (2 and 3) for SmartDNS.
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 4 5'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 2 3'
option vid '3'
B) You could connect an unmanaged switch to port 2 of the router and then connect all yours wired (SmartDNS) devices to that switch.
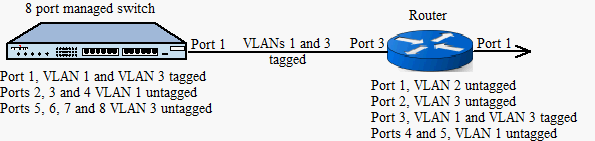
C) You could increase simultaneously the number of wired ports for VLAN 1 and VLAN 3 using an 8 port managed switch and tagged frames (for both VLANs) between the switch and the router.
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 3t 4 5'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 2 3t'
option vid '3'
I hope the scheme below will make option C more clear. You’ll have 5 wired ports for each VLAN.
VLAN 1 - Router ports 4,5 / Switch ports 2,3 and 4
VLAN 3 – Router port 2 / Switch ports 5, 6, 7 and 8.