Its neither DSA nor swconfig, all of the ports are presented as regular netdevs and VLAN-s work AFAIK
There is a listing for a Dynalink DL-WRX36 on Amazon.de https://www.amazon.de/gp/product/B098WC99VC/ for 69.99EUR
available from amazon.com
https://www.amazon.com/Dynalink-DL-WRX36-8-Stream-Wireless-3-6Gbps/dp/B096K9SVCT
Oh, so they finally started selling directly in the EU as well though to select countries.
Damn, currently its only 67 EUR with shipping to DE, thats bargain for the HW
@robimarko I found an obscure case where WIFI stops working when old WPA1 (ecobee thermostat) is trying to join WPA2 SSID. (Ecobee thermostat is only capable of joining WPA1 SSID, but it should not crash whole WIFI). Ethernet ports and rest of the router continue to work normally.
logread and dmesg output: https://pastebin.com/nATKL3KD
password: badWIFI
I received my device and I have been playing with the OEM firmware to better understand it.
So far I have figured out how ssh and web access work, and why it was confusing early on the thread (ssh and web UI can have a different password).
/etc/shadow has the password for ssh, and probably serial as well (if required).
/etc/config/pwd has the password for the web UI.
There is also has an additional step for enabling ssh.
In addition to enabling the dropbear instance on /etc/config/dropbear, the user has to be authorized for "local ssh" access on /etc/config/pwd.
Here is a summary to reliable get ssh access on the OEM firmware:
- Download config, decrypt, and uncompress it
- To decrypt (assumes downloaded config is called "backup.cfg"):
# openssl enc -d -aes-256-cbc -a -in backup.cfg -out backup.tar.gz -pass pass:AskeyRT5000wKey1357924680 -
/etc/config/dropbear: Enable dropbear instance on lan interface# (change enable from 0 to 1) config dropbear option Interface 'lan' option enable '1' -
/etc/config/pwd: Enable local ssh access for the admin user# (change local_ssh from 0 to 1) config userinfo 'subscriber' option local_ssh '1' -
/etc/shadow: Change password for the admin user to a known value- Example: set password to "askey1234"
admin:$1$0Zm8tfKN$3hW1vziEpFyHfBu.uJ.q61:17410:0:99999:7::: - Compress configuration and encrypt it (assumes source directory is called "backup"):
# tar czf backup-enable_ssh.tar.gz -C backup etc lib # openssl enc -e -aes-256-cbc -a -in backup-enable_ssh.tar.gz -out backup-enable_ssh.cfg -pass pass:AskeyRT5000wKey1357924680 - Upload configuration (device will automatically reboot)
- SSH to the router using "admin" as the user
Credits to @lmore377 for finding how to decrypt and encrypt the config on link (from this thread)
Well, basically the whole ath11k FW crapped out and crashed
Hi All,
Anyone know how to flash back to Dynalink original FW?
I have modified my original post to include this and make it more explicit.
Credits to @lmore377 for finding how to decrypt and encrypt the config on link (from this thread)
Anyway, here it is again.
To decrypt (assumes downloaded config is called "backup.cfg"):
# openssl enc -d -aes-256-cbc -a -in backup.cfg -out backup.tar.gz -pass pass:AskeyRT5000wKey1357924680
To compress configuration and encrypt it (assumes source directory is called "backup"):
# tar czf backup-enable_ssh.tar.gz -C backup etc lib
# openssl enc -e -aes-256-cbc -a -in backup-enable_ssh.tar.gz -out backup-enable_ssh.cfg -pass pass:AskeyRT5000wKey1357924680
Thank you for porting some of the ath11k fixes. I did test the latest build (OpenWrt SNAPSHOT, r0-a56980f) bun unfortunately it continues having the same issue with ath11 crashing.
i tried to reproduce it with two ssid on radio1 one with WPA and it is not crashing maybe because i don't have a similar device as yours... are you able to share the wifi config ? one thought could be to setup the ssid that the ecobee is connecting to in legacy mode
When trying to reproduce the issue yesterday, it appears that I had to try to access two separate SSIDs from this one device (ecobee). Both are WPA2 but one is Auto and the other Force AES for cipher. (I incorrectly said it was WPA2 that prevents device from connecting but it seems to be cipher setting.
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/soc/c000000.wifi'
option band '5g'
option htmode 'HE160'
option country 'US'
option cell_density '1'
option distance '66'
option channel '100'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/soc/c000000.wifi+1'
option channel '1'
option band '2g'
option htmode 'HE20'
option cell_density '0'
config wifi-iface 'wifinet4'
option device 'radio1'
option mode 'ap'
option ssid 'wifi1'
option encryption 'psk2'
option key '***'
option network 'lan'
config wifi-iface 'wifinet5'
option device 'radio1'
option mode 'ap'
option ssid 'wifi2'
option network 'lan'
option encryption 'psk2+ccmp'
option key '***'
would you mind to add to radio1 the country? i always use psk2+ccmp... i doubt this is the problem
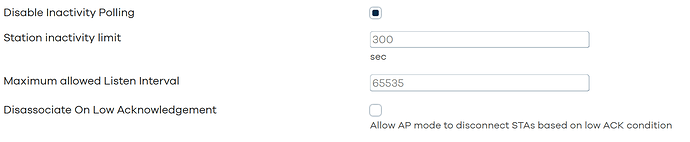
it crashes when "disassociated due to inactivity" ... is the mac 01:01:01:01:01 the ecobee? as a workaround set the interface like this
or you could increase the "station inactivity limit" .... i am curious to see if it still crashes
Sorry, I changed MACs of all devices to 01...
I think disassociated due to inactivity is a side-effect of the issue, as crash only happens on authentication. AES-CCMP is more secure therefore I choose it when I can. It might be that most people have it on psk-ccmp and hence the crash is not widely reported.
@robimarko, I see the commit on your repo adding support for single-partition only.
The script from @clayface has some interesting logic that can be used for multiple-partitions (and some bootcount for recovery).
What would be the best approach for official OpenWrt support?
Having a way to TFTP load an initramfs image as a recovery method without seral access would be great for users.
But there might be some trade-off like flash wearing.
bootcount logic from @clayface does a saveenv on each count.
And it seems implementing multiple-partitions would required saving the active one to u-boot env as well (on each sysupgrade).
I can run some tests on my device to make sure it's working fine.
On the same lines, do you know if we can detect at runtime what is the active slot being used?
OpenWrt probably has something for devices that support it, and I can try on OEM firmware as well.
U-boot writing bootcount or active partition is the least of worries for flash wear.
I dont have anything against using the traditional dual FW with update one, keep the previous as backup, but I dont have to implement anything like that myself.
I think I got an idea why attempting to automatically load (using bootcmd) an image from TFTP is not working compared to manually calling the commands by serial connection.
It seems the network is only initialized when autoboot is stopped and the U-Boot shell is shown.
Does anyone knows how to initialize the net (or anything that would make it work) without getting into the U-boot shell?
Any ideas are appreciated.
I used the following command to test (the same happens with tftpboot, and adding a sleep before doesn't help):
# setenv bootcmd "echo ping start; ping 192.168.1.10; echo ping end;"
And here is the output from serial connection:
Hit any key to stop autoboot: 0
ping start
No ethernet found.
ping failed; host 192.168.1.10 is not alive
ping end
Net: MAC0 addr:2c:ea:dc:xx:xx:xx
PHY ID1: 0x4d
PHY ID2: 0xd0b1
PHY ID1: 0x4d
PHY ID2: 0xd101
EDMA ver 1 hw init
Num rings - TxDesc:1 (0-0) TxCmpl:1 (7-7)
RxDesc:1 (15-15) RxFill:1 (7-7)
ipq807x_edma_alloc_rings: successfull
ipq807x_edma_setup_ring_resources: successfull
ipq807x_edma_configure_rings: successfull
ipq807x_edma_hw_init: successfull
eth0
(interactive shell reached)
IPQ807x# ping 192.168.1.10
ipq807x_eth_halt: done
eth0 PHY0 Down Speed :10 Half duplex
eth0 PHY1 up Speed :1000 Full duplex
eth0 PHY2 Down Speed :10 Half duplex
eth0 PHY3 Down Speed :10 Half duplex
eth0 PHY4 Down Speed :10 Half duplex
eth0 PHY5 Down Speed :10 Half duplex
ipq807x_eth_init: done
Using eth0 device
ipq807x_eth_halt: done
host 192.168.1.10 is alive
It seems to ipq7x functions are doing something.
U-boot will init networking as soon as you interrupt autoboot and drop into shell, but you have to give it like 20-30 seconds
That's the thing, I don't what to interrupt autoboot and get to the U-boot shell.
I'm trying to avoid the need for serial access.
Since I was not able to initialize the network with a command, I'm now exploring loading the initramfs image from USB.