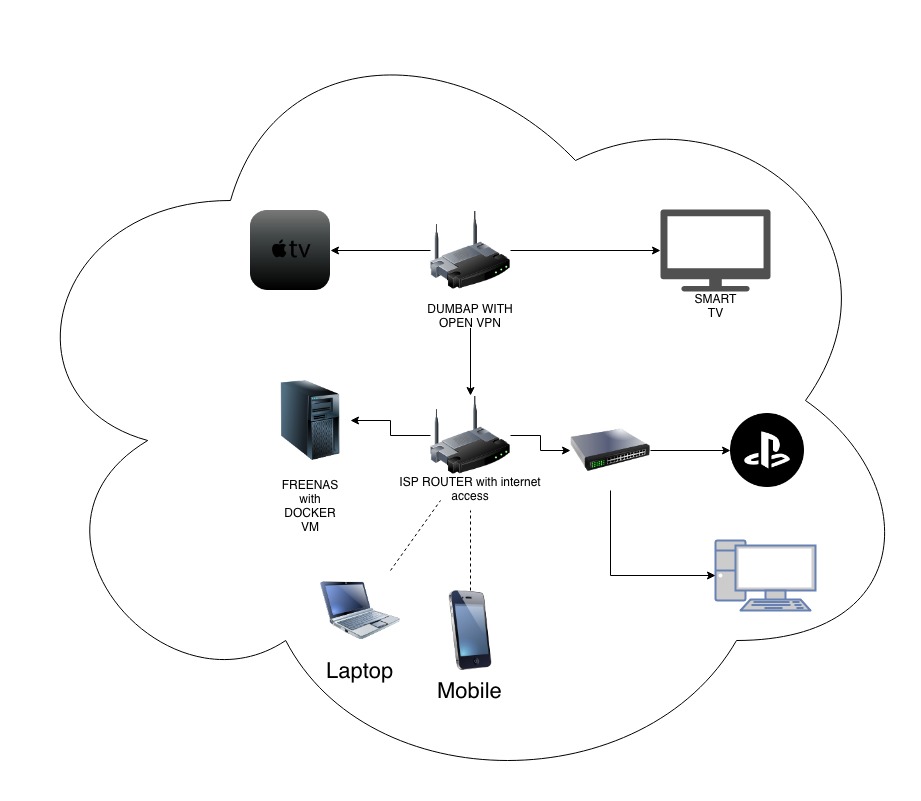
Hello,https://openwrt.org/docs/guide-user/network/wifi/dumbap https://nordvpn.com/tutorials/openwrt/openvpn/
I've managed to get working internet and local network(to access NAS(PLEX, Radarr etc.)) but I can't get OpenVPN working so it will pass all the traffic through VPN.
mk24
December 2, 2018, 2:06pm
2
You want the dumb AP machine to run OpenVPN in client mode, as a client of a third party service?
That is straightforward. After you get OpenVPN to connect to the service, it will start up a "tap" interface which is your end of the VPN tunnel. You then need to set up a new separate network in the dumb AP/VPN client machine for VPN users such as the Apple TV. Use VLANs in the Ethernet switch so that different Ethernet ports can serve different networks. Then just like a main router forwarding to the Internet, you use two firewall zones with Masquerade enabled on the destination zone, so the Apple TV will NAT into the VPN tunnel, and come out at the remote server's end.
So you do need a firewall running on that machine for the VPN users, but LAN users of the dumb AP do not pass through the firewall since they are all on the LAN network.
@braian87b made two really useful github post for your needs:
In the the last two links the DNS script is kinda messed up, here's the correct versionhttps://forum.archive.openwrt.org/viewtopic.php?id=26746&p=1#p118310
The solution is to create two scripts: /etc/openvpn/updns :
#!/bin/sh
mv /tmp/resolv.conf.auto /tmp/resolv.conf.auto.hold
echo $foreign_option_1 | sed -e 's/dhcp-option DOMAIN/domain/g' -e 's/dhcp-option DNS/nameserver/g' > /tmp/resolv.conf.auto
echo $foreign_option_2 | sed -e 's/dhcp-option DOMAIN/domain/g' -e 's/dhcp-option DNS/nameserver/g' >> /tmp/resolv.conf.auto
echo $foreign_option_3 | sed -e 's/dhcp-option DOMAIN/domain/g' -e 's/dhcp-option DNS/nameserver/g' >> /tmp/resolv.conf.auto
and /etc/openvpn/downdns :
#!/bin/sh
mv /tmp/resolv.conf.auto.hold /tmp/resolv.conf.auto
And add them to .ovpn files with this:
script-security 2 system
up "/etc/openvpn/updns"
down "/etc/openvpn/downdns"
in my .ovpn config I used
2 Likes
apologies for resurrecting an old thread, this is almost exactly the setup I need, im using a bthome hub 5 and i've followed the guide to setup the dumb AP and have gotten openvpn working and the traceroute confirms when ssh'd into openwrt the VPN is up, I would like to connect devices by wifi and ethernet ports to the AP for VPN.
Below are the configs I thought relevant, I did have this device running as my main router with VPN, but it crashed recently and I cant bring myself to spend a lot of cash on an OEM bells and whistles router.
firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option network 'lan'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list device 'tun0'
option network 'wan wan6'
network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc9:0c96:0fe6::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.253'
option gateway '192.168.1.254'
option dns '8.8.8.8'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '44:e9:dd:5b:18:12'
config interface 'wan'
option ifname 'dsl0'
option proto 'pppoe'
option username 'username'
option password 'password'
option ipv6 '1'
config device 'wan_dev'
option name 'dsl0'
option macaddr '44:e9:dd:5b:18:13'
config interface 'wan6'
option ifname '@wan'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0 1 2 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 6t'
option vid '2'
config interface 'torguardvpn'
option proto 'none'
option ifname 'tun0'
option auto '1'
more config output
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
link/ether da:8b:08:d8:9b:91 brd ff:ff:ff:ff:ff:ff
inet6 fe80::d88b:8ff:fed8:9b91/64 scope link
valid_lft forever preferred_lft forever
3: wlan0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 44:e9:dd:5b:18:15 brd ff:ff:ff:ff:ff:ff
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 44:e9:dd:5b:18:12 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.253/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fdc9:c96:fe6::1/60 scope global
valid_lft forever preferred_lft forever
inet6 fe80::46e9:ddff:fe5b:1812/64 scope link
valid_lft forever preferred_lft forever
6: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 44:e9:dd:5b:18:12 brd ff:ff:ff:ff:ff:ff
7: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 44:e9:dd:5b:18:14 brd ff:ff:ff:ff:ff:ff
inet6 fe80::46e9:ddff:fe5b:1814/64 scope link
valid_lft forever preferred_lft forever
8: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN qlen 100
link/[65534]
inet 10.9.0.14 peer 10.9.0.13/32 scope global tun0
valid_lft forever preferred_lft forever
inet6 fe80::9dfd:741a:977f:2d3a/64 scope link
valid_lft forever preferred_lft forever
0.0.0.0/1 via 10.9.0.13 dev tun0
default via 192.168.1.254 dev br-lan
10.9.0.1 via 10.9.0.13 dev tun0
10.9.0.13 dev tun0 scope link src 10.9.0.14
88.202.177.238 via 192.168.1.254 dev br-lan
128.0.0.0/1 via 10.9.0.13 dev tun0
192.168.1.0/24 dev br-lan scope link src 192.168.1.253
root@OpenWrt:/etc/config# uci show network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fdc9:0c96:0fe6::/48'
network.atm=atm-bridge
network.atm.vpi='1'
network.atm.vci='32'
network.atm.encaps='llc'
network.atm.payload='bridged'
network.atm.nameprefix='dsl'
network.dsl=dsl
network.dsl.annex='a'
network.dsl.tone='av'
network.dsl.ds_snr_offset='0'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0.1'
network.lan.proto='static'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.ipaddr='192.168.1.253'
network.lan.gateway='192.168.1.254'
network.lan.dns='8.8.8.8'
network.lan_dev=device
network.lan_dev.name='eth0.1'
network.lan_dev.macaddr='44:e9:dd:5b:18:12'
network.wan=interface
network.wan.ifname='dsl0'
network.wan.proto='pppoe'
network.wan.username='username'
network.wan.password='password'
network.wan.ipv6='1'
network.wan_dev=device
network.wan_dev.name='dsl0'
network.wan_dev.macaddr='44:e9:dd:5b:18:13'
network.wan6=interface
network.wan6.ifname='@wan'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].vid='1'
network.@switch_vlan[0].ports='0 1 2 4 6t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='5 6t'
network.@switch_vlan[1].vid='2'
network.torguardvpn=interface
network.torguardvpn.proto='none'
network.torguardvpn.ifname='tun0'
network.torguardvpn.auto='1'
root@OpenWrt:/etc/config# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.lan=zone
firewall.lan.name='lan'
firewall.lan.input='ACCEPT'
firewall.lan.output='ACCEPT'
firewall.lan.forward='REJECT'
firewall.lan.network='lan'
firewall.wan=zone
firewall.wan.name='wan'
firewall.wan.input='REJECT'
firewall.wan.output='ACCEPT'
firewall.wan.forward='REJECT'
firewall.wan.masq='1'
firewall.wan.mtu_fix='1'
firewall.wan.device='tun0'
firewall.wan.network='wan wan6'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[2]=zone
firewall.@zone[2].name='vpn'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].masq='1'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].forward='ACCEPT'
firewall.@zone[2].network='torguardvpn'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].dest='lan'
firewall.@forwarding[0].src='vpn'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].dest='vpn'
firewall.@forwarding[1].src='lan'