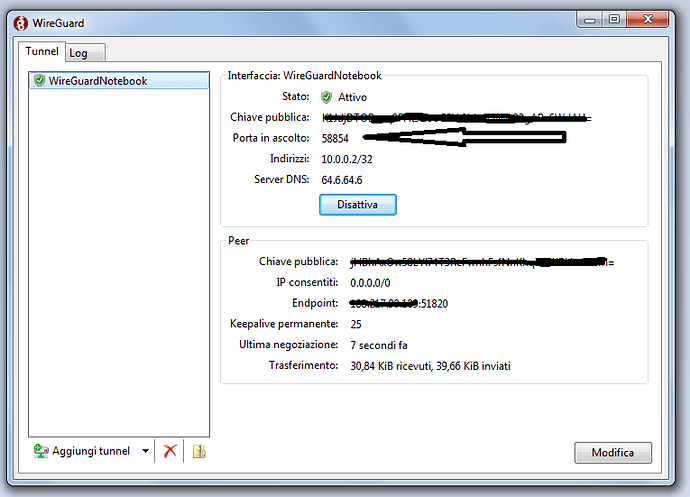
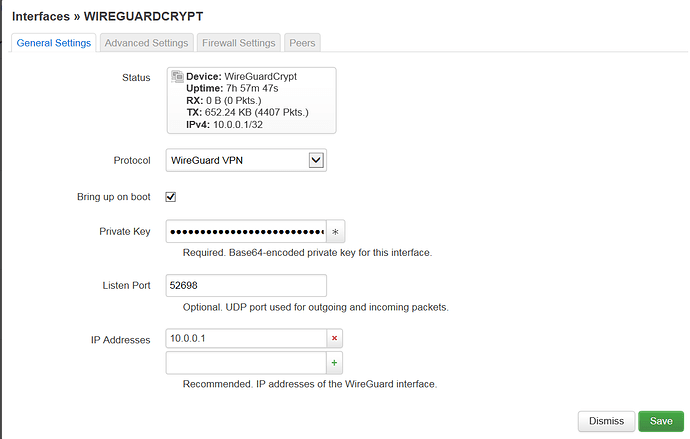
I recommend using LuCI to configure because the guide on the DuckDNS website is outdated.
I managed to start the script but the problem is not solved, the dns domain does not connect the interface to the wireguard network, it remains in congestion. I already use LUCI
,Okay, twist! I discovered that the DNS domain name works, what sends my wirguard network into congestion is the "listening port", when I find the network blocked by manually editing and updating the new port, the connection restarts.
How can I make it fixed and not change?
Here are my configuration files that may help you (I use recently updated snapshots):
SERVER
/etc/config/network
config interface 'wg0'
option proto 'wireguard'
list addresses '192.168.3.1/24'
option delegate '0'
option listen_port '12345'
option private_key 'server-private-key'
config wireguard_wg0
option public_key 'client-public-key'
option description 'SM-G531M'
list allowed_ips '192.168.3.2/24'
option route_allowed_ips '1'
option persistent_keepalive '25'
config interface 'wg1'
option proto 'wireguard'
option delegate '0'
list addresses '192.168.4.1/24'
option private_key 'server-private-key'
option listen_port '12346'
config wireguard_wg1
option description 'GA-B150M-DS3H'
option route_allowed_ips '1'
option persistent_keepalive '25'
option public_key 'client-public-key'
list allowed_ips '192.168.4.2/24'
/etc/config/firewall
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan wg0 wg1'
option family 'ipv4'
config rule
option name 'wg0'
option family 'ipv4'
list proto 'udp'
option src '*'
option dest_port '12345'
option target 'ACCEPT'
config rule
option name 'wg1'
option family 'ipv4'
list proto 'udp'
option src '*'
option dest_port '12346'
option target 'ACCEPT'
CLIENT
[Interface]
PrivateKey = client-private-key
Address = 192.168.4.2/24
DNS = 192.168.1.11
[Peer]
PublicKey = server-public-key
AllowedIPs = 0.0.0.0/0
Endpoint = domain.duckdns.org:12346
PersistentKeepalive = 25
Why do you have two wireguard interfaces?
Ok, I have come to the conclusion that this GL.inet interface is a disaster and it is better to totally eliminate it by inserting an updated and stable OPENWRT relase, could you tell me which relase to download for my AR750S EXT.?
The / etc / config / network parameters that I have set on LUCI do not correspond to those that I then find on the GL.INET interface ... A DISASTER AND WASTE OF TIME, I absolutely want to remove this proprietary interface by inserting a relase OPENWRT LUCI.
Thanks friends.
I'm pretty sure you can access Luci from the gl iNet GUI. It's under advanced or simar.
Certainly but it is an old outdated relase, exactly the "Powered by LuCI openwrt-18.06 branch (git-18.196.56128-9112198) / OpenWrt 18.06.1 r7258-5eb055306f"
I would like to remove the proprietary interface because it only creates confusion, everything I enter on LUCI is not transmitted to the GL.INET CLI, it is just a waste of time.
I understand that in a WireGuard connection, each peer has to have the public key of the other pair and each one has its private key. So I have two WireGuard interfaces. If I use the public key from a single interface, I would have to put the same private key on both clients. That is what I understood in a connection with private and public keys.
Not quite. Each peer has it's own unique private key and public key. The private key is used by the peer to decrypt data and the public key is used by other peers to encrypt data. You can give the public key out to as many other peers as you please, that's the point of a public key. So in the case of an endpoint on a OpenWRT router you only need one WG interface even if you want to connect multiple end devices, you just use multiple peers on that one device.
Oh, I understand! No wonder there is an option to add more pairs in the WireGuard interface. Thank you!
And how should I create the keys? Does one key not depend on the other or are they independent?
The keys for each peer are independent, i.e. each device has it's own private and public key. The private key stays on the device and the public key is used on other devices to setup the peer. So if you wanted to connect multiple devices to your OpenWRT router you'd use the router's public key on each of them to create a peer, and then set up multiple peers on the router with each one using a different public key from the devices you're connecting.
I ask if one key depends on the other because I noticed in the Android and Windows application that it only lets me configure the private key and start from it, generate the public one or that's what it seems.
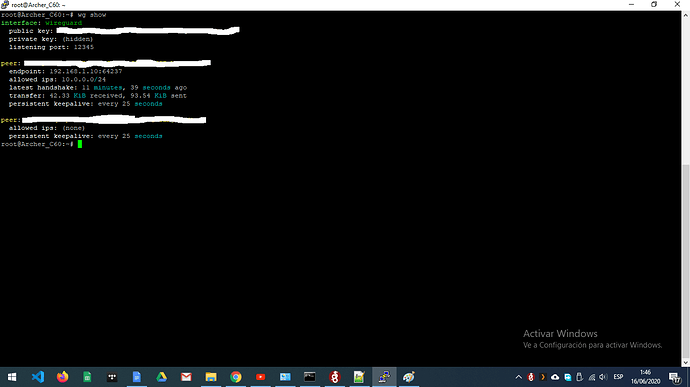
I also see that if I run wg show on the server it shows in allowed ips like (none), on one pair (I can't connect to anything). It seems that the interface does not support having two pairs. So I had to create two interfaces.
Ok @castillofrancodamian finally I managed to configure OpenWrt 19.07.3, I installed all the wireguard plugins, updated opkg and related upgrades, configured network cards, etc. Finally after hours and hours I managed to become the Master of my AR750S device.
Now I need your precious help to correctly set up wireguard server and to be able to connect my clients.
Could you help me with the SSH commands to use to generate the keys?
Maybe my case can help you.
ok, I generated the keys in /etc/wireguard
Now I need to understand how to paste these keys and how to configure the firewall.
root@OpenWrt:~# cd /etc
root@OpenWrt:/etc# cd wireguard
root@OpenWrt:/etc/wireguard# ls
client-privatekey client-publickey server-privatekey server-publickey
root@OpenWrt:/etc/wireguard#
piccoli passi iniziano a dare qualche risultato, adesso non capisco il perchè la connessione trasmetta una volta attivata la rete wireguard ma non riceve.
Sarà qualche problema legato al firewall?
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan WireGuardCrypt'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
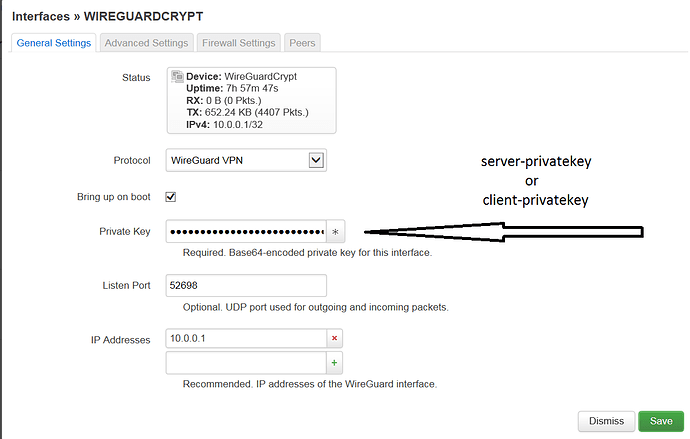
under PrivateKey I entered the client-privatekey, is it correct?
Private keys always stay on the device they're intended for. They shouldn't be entered or stored on any other device.