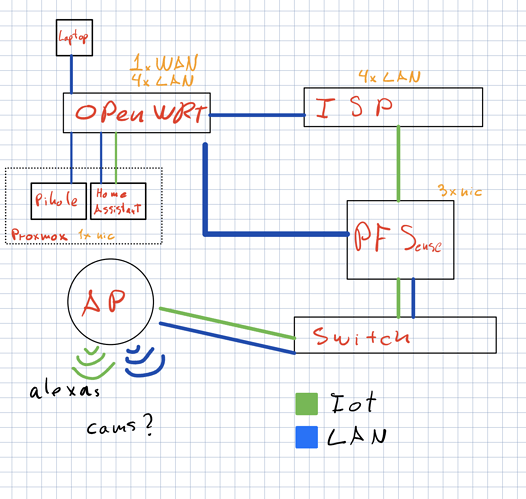
I don't quite get the intention behind that diagram, respectively what you expect the individual devices to do.
"ISP" with "4x LAN" suggests that you're dealing with an ISP modem-router, terminating your external WAN IPv4 address - while sometimes unavoidable, this is not an ideal setup, as you either need to do dual-NAT behind the ISP router (or static routes/ and NAT-less routing) or make your other devices part of the ISP-LAN network. In either way NAT/ routing/ firewalling would be handled by the ISP device, which one shouldn't consider to be 'trusted', nor as full-featured as either OpenWrt or pfsense (you'd lose a lot of features from the dumbed down ISP device).
The next aspect seems to be that you connect both the OpenWrt device and the pfsense box to your ISP router's LAN ports - and then interconnect the OpenWrt router and the pfsense box again, which doesn't really make sense. Unless you have a rather sophisticated VLAN- and segmented subnet setup (which the ISP router probably won't allow) or a LAG setting, you should only have one connection between devices - adding loops is just a recipe for pain.
Then I don't really understand the roles each of those devices is supposed to play. As it appears from the diagram, the pfsense box appears to only work as transparent bridge, to connect your switch with the ISP router, which wouldn't really make sense - the OpenWrt router appears to have more of a purpose. by acting as AP (but why do you have a WAN link there) and potentially spanning up multiple VLANs, but it's not really structured either.
It would be ideal if you would decide about the basic network structure first and what purpose each of these devices is supposed to play Basically there should only be one router (yes, that one might have to be behind the ISP router, if you can't get rid of that or degrade it to a mere bridged modem), which is the central decision maker in your network (external WAN IP terminated there, so it can do meaningful firewalling and port-forwardings as needed, inter-VLAN routing and firewalling, etc.), all other devices then play a strictly serving role for it (e.g. using the OpenWrt device merely as managed switch + AP, with all the VLANs defined on the pfsense - or doing away with the pfsense box alltogether and letting the OpenWrt router do everything).
Yes, in a corporate setting with hundreds of clients working on the clock and a need for multiple failovers it might make sense to put the individual roles on different devices (modem, router, firewall, DHCP+DNS server, backend switching, etc.), but at home that quickly shoots yourself into the foot (because everything has to work from the first second, just to read further documentation on the web, but that isn't going to be the case. You'd basically distribute your single point failure over several different -barely integrated- devices, with failure of any of those breaking the whole lot - thereby multiplying your failure potential.