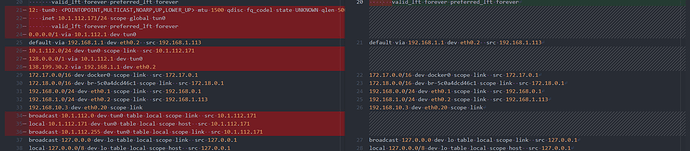
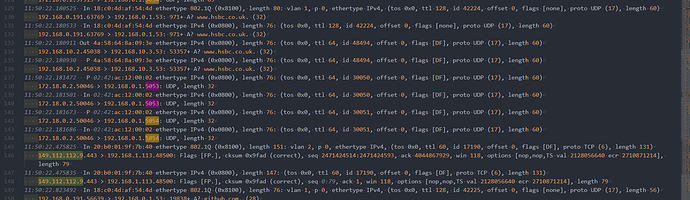
Rightio, I have another output. It does seem to show the response from Quad9 back to the Pi. Where at the moment it goes: internet -> modem -> Pi -> LAN clients, and on the way out in reverse of course.
root@OpenWrt:~# tcpdump -i any -evn '(udp port 53 or port 5053 or port 5054) or (host 1.1.1.1 or host 1.0.0.1 or host 9.9.9.9 or host 149.112.112.9)'
tcpdump: listening on any, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
11:50:18.814261 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 76: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42207, offset 0, flags [none], proto UDP (17), length 56)
192.168.0.191.56639 > 192.168.0.1.53: 19838+ A? github.com. (28)
11:50:18.814271 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 128, id 42207, offset 0, flags [none], proto UDP (17), length 56)
192.168.0.191.56639 > 192.168.0.1.53: 19838+ A? github.com. (28)
11:50:18.814693 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 48040, offset 0, flags [DF], proto UDP (17), length 56)
192.168.10.2.57075 > 192.168.10.3.53: 65405+ A? github.com. (28)
11:50:18.814712 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 48040, offset 0, flags [DF], proto UDP (17), length 56)
192.168.10.2.57075 > 192.168.10.3.53: 65405+ A? github.com. (28)
11:50:18.815325 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 29681, offset 0, flags [DF], proto UDP (17), length 56)
172.18.0.2.36327 > 192.168.0.1.5053: UDP, length 28
11:50:18.815353 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 29681, offset 0, flags [DF], proto UDP (17), length 56)
172.18.0.2.36327 > 192.168.0.1.5053: UDP, length 28
11:50:18.815536 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 29682, offset 0, flags [DF], proto UDP (17), length 56)
172.18.0.2.36327 > 192.168.0.1.5054: UDP, length 28
11:50:18.815550 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 29682, offset 0, flags [DF], proto UDP (17), length 56)
172.18.0.2.36327 > 192.168.0.1.5054: UDP, length 28
11:50:19.936693 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 83: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42211, offset 0, flags [none], proto UDP (17), length 63)
192.168.0.191.61248 > 192.168.0.1.53: 21425+ A? sync-v2.brave.com. (35)
11:50:19.936701 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 128, id 42211, offset 0, flags [none], proto UDP (17), length 63)
192.168.0.191.61248 > 192.168.0.1.53: 21425+ A? sync-v2.brave.com. (35)
11:50:19.937089 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 48267, offset 0, flags [DF], proto UDP (17), length 63)
192.168.10.2.35762 > 192.168.10.3.53: 43061+ A? sync-v2.brave.com. (35)
11:50:19.937105 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 48267, offset 0, flags [DF], proto UDP (17), length 63)
192.168.10.2.35762 > 192.168.10.3.53: 43061+ A? sync-v2.brave.com. (35)
11:50:19.937619 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 29884, offset 0, flags [DF], proto UDP (17), length 63)
172.18.0.2.55563 > 192.168.0.1.5053: UDP, length 35
11:50:19.937652 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 29884, offset 0, flags [DF], proto UDP (17), length 63)
172.18.0.2.55563 > 192.168.0.1.5053: UDP, length 35
11:50:19.937856 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 29885, offset 0, flags [DF], proto UDP (17), length 63)
172.18.0.2.55563 > 192.168.0.1.5054: UDP, length 35
11:50:19.937877 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 29885, offset 0, flags [DF], proto UDP (17), length 63)
172.18.0.2.55563 > 192.168.0.1.5054: UDP, length 35
11:50:20.089682 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 111: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42213, offset 0, flags [none], proto UDP (17), length 91)
192.168.0.191.59290 > 192.168.0.1.53: 15679+ A? REDACTED.blob.core.windows.net. (63)
11:50:20.089692 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 128, id 42213, offset 0, flags [none], proto UDP (17), length 91)
192.168.0.191.59290 > 192.168.0.1.53: 15679+ A? REDACTED.blob.core.windows.net. (63)
11:50:20.090149 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 48279, offset 0, flags [DF], proto UDP (17), length 91)
192.168.10.2.40115 > 192.168.10.3.53: 44573+ A? REDACTED.blob.core.windows.net. (63)
11:50:20.090168 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 48279, offset 0, flags [DF], proto UDP (17), length 91)
192.168.10.2.40115 > 192.168.10.3.53: 44573+ A? REDACTED.blob.core.windows.net. (63)
11:50:20.091635 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 29887, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5053: UDP, length 63
11:50:20.091697 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 29887, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5053: UDP, length 63
11:50:20.159639 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 80: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42214, offset 0, flags [none], proto UDP (17), length 60)
192.168.0.191.63769 > 192.168.0.1.53: 971+ A? www.hsbc.co.uk. (32)
11:50:20.159649 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 128, id 42214, offset 0, flags [none], proto UDP (17), length 60)
192.168.0.191.63769 > 192.168.0.1.53: 971+ A? www.hsbc.co.uk. (32)
11:50:20.159994 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 48284, offset 0, flags [DF], proto UDP (17), length 60)
192.168.10.2.45038 > 192.168.10.3.53: 53357+ A? www.hsbc.co.uk. (32)
11:50:20.160007 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 48284, offset 0, flags [DF], proto UDP (17), length 60)
192.168.10.2.45038 > 192.168.10.3.53: 53357+ A? www.hsbc.co.uk. (32)
11:50:20.162517 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 29904, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5053: UDP, length 32
11:50:20.162565 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 29904, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5053: UDP, length 32
11:50:21.090663 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 111: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42218, offset 0, flags [none], proto UDP (17), length 91)
192.168.0.191.59290 > 192.168.0.1.53: 15679+ A? REDACTED.blob.core.windows.net. (63)
11:50:21.090671 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 128, id 42218, offset 0, flags [none], proto UDP (17), length 91)
192.168.0.191.59290 > 192.168.0.1.53: 15679+ A? REDACTED.blob.core.windows.net. (63)
11:50:21.090935 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 48399, offset 0, flags [DF], proto UDP (17), length 91)
192.168.10.2.40115 > 192.168.10.3.53: 44573+ A? REDACTED.blob.core.windows.net. (63)
11:50:21.090945 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 48399, offset 0, flags [DF], proto UDP (17), length 91)
192.168.10.2.40115 > 192.168.10.3.53: 44573+ A? REDACTED.blob.core.windows.net. (63)
11:50:21.091258 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 29954, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5053: UDP, length 63
11:50:21.091278 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 29954, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5053: UDP, length 63
11:50:21.091378 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 29955, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5054: UDP, length 63
11:50:21.091394 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 29955, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5054: UDP, length 63
11:50:21.167001 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 80: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42219, offset 0, flags [none], proto UDP (17), length 60)
192.168.0.191.63769 > 192.168.0.1.53: 971+ A? www.hsbc.co.uk. (32)
11:50:21.167009 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 128, id 42219, offset 0, flags [none], proto UDP (17), length 60)
192.168.0.191.63769 > 192.168.0.1.53: 971+ A? www.hsbc.co.uk. (32)
11:50:21.167255 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 48404, offset 0, flags [DF], proto UDP (17), length 60)
192.168.10.2.45038 > 192.168.10.3.53: 53357+ A? www.hsbc.co.uk. (32)
11:50:21.167264 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 48404, offset 0, flags [DF], proto UDP (17), length 60)
192.168.10.2.45038 > 192.168.10.3.53: 53357+ A? www.hsbc.co.uk. (32)
11:50:21.167545 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 29968, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5053: UDP, length 32
11:50:21.167561 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 29968, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5053: UDP, length 32
11:50:21.167649 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 29969, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5054: UDP, length 32
11:50:21.167663 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 29969, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5054: UDP, length 32
11:50:21.998526 In 00:00:00:00:00:00 ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 9511, offset 0, flags [DF], proto UDP (17), length 58)
127.0.0.1.37966 > 127.0.0.1.53: 23200+ A? meta.plex.tv. (30)
11:50:21.998782 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 48478, offset 0, flags [DF], proto UDP (17), length 58)
192.168.10.2.46650 > 192.168.10.3.53: 60659+ A? meta.plex.tv. (30)
11:50:21.998811 In 00:00:00:00:00:00 ethertype IPv6 (0x86dd), length 94: (flowlabel 0xdcc8f, hlim 64, next-header UDP (17) payload length: 38) ::1.37966 > ::1.53: [bad udp cksum 0x0039 -> 0xf63a!] 23200+ A? meta.plex.tv. (30)
11:50:21.998988 In 00:00:00:00:00:00 ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 9512, offset 0, flags [DF], proto UDP (17), length 58)
127.0.0.1.37966 > 127.0.0.1.53: 23533+ AAAA? meta.plex.tv. (30)
11:50:21.999084 In 00:00:00:00:00:00 ethertype IPv6 (0x86dd), length 94: (flowlabel 0xdcc8f, hlim 64, next-header UDP (17) payload length: 38) ::1.37966 > ::1.53: [bad udp cksum 0x0039 -> 0xf4d2!] 23533+ AAAA? meta.plex.tv. (30)
11:50:21.999120 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 48479, offset 0, flags [DF], proto UDP (17), length 58)
192.168.10.2.49545 > 192.168.10.3.53: 26455+ AAAA? meta.plex.tv. (30)
11:50:21.999293 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 48478, offset 0, flags [DF], proto UDP (17), length 58)
192.168.10.2.46650 > 192.168.10.3.53: 60659+ A? meta.plex.tv. (30)
11:50:21.999323 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 48479, offset 0, flags [DF], proto UDP (17), length 58)
192.168.10.2.49545 > 192.168.10.3.53: 26455+ AAAA? meta.plex.tv. (30)
11:50:22.000251 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 30020, offset 0, flags [DF], proto UDP (17), length 58)
172.18.0.2.39877 > 192.168.0.1.5053: UDP, length 30
11:50:22.000279 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 30020, offset 0, flags [DF], proto UDP (17), length 58)
172.18.0.2.39877 > 192.168.0.1.5053: UDP, length 30
11:50:22.001070 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 30021, offset 0, flags [DF], proto UDP (17), length 58)
172.18.0.2.40747 > 192.168.0.1.5053: UDP, length 30
11:50:22.001096 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 30021, offset 0, flags [DF], proto UDP (17), length 58)
172.18.0.2.40747 > 192.168.0.1.5053: UDP, length 30
11:50:22.101835 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 111: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42223, offset 0, flags [none], proto UDP (17), length 91)
192.168.0.191.59290 > 192.168.0.1.53: 15679+ A? REDACTED.blob.core.windows.net. (63)
11:50:22.101843 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 128, id 42223, offset 0, flags [none], proto UDP (17), length 91)
192.168.0.191.59290 > 192.168.0.1.53: 15679+ A? REDACTED.blob.core.windows.net. (63)
11:50:22.102211 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 48493, offset 0, flags [DF], proto UDP (17), length 91)
192.168.10.2.40115 > 192.168.10.3.53: 44573+ A? REDACTED.blob.core.windows.net. (63)
11:50:22.102228 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 48493, offset 0, flags [DF], proto UDP (17), length 91)
192.168.10.2.40115 > 192.168.10.3.53: 44573+ A? REDACTED.blob.core.windows.net. (63)
11:50:22.102748 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 30040, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5053: UDP, length 63
11:50:22.102780 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 30040, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5053: UDP, length 63
11:50:22.102930 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 30041, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5054: UDP, length 63
11:50:22.102944 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 30041, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5054: UDP, length 63
11:50:22.180525 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 80: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42224, offset 0, flags [none], proto UDP (17), length 60)
192.168.0.191.63769 > 192.168.0.1.53: 971+ A? www.hsbc.co.uk. (32)
11:50:22.180533 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 128, id 42224, offset 0, flags [none], proto UDP (17), length 60)
192.168.0.191.63769 > 192.168.0.1.53: 971+ A? www.hsbc.co.uk. (32)
11:50:22.180911 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 48494, offset 0, flags [DF], proto UDP (17), length 60)
192.168.10.2.45038 > 192.168.10.3.53: 53357+ A? www.hsbc.co.uk. (32)
11:50:22.180930 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 48494, offset 0, flags [DF], proto UDP (17), length 60)
192.168.10.2.45038 > 192.168.10.3.53: 53357+ A? www.hsbc.co.uk. (32)
11:50:22.181472 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 30050, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5053: UDP, length 32
11:50:22.181501 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 30050, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5053: UDP, length 32
11:50:22.181673 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 30051, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5054: UDP, length 32
11:50:22.181686 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 30051, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5054: UDP, length 32
11:50:22.475825 In 20:b0:01:9f:7b:40 ethertype 802.1Q (0x8100), length 151: vlan 2, p 0, ethertype IPv4, (tos 0x0, ttl 60, id 17190, offset 0, flags [DF], proto TCP (6), length 131)
149.112.112.9.443 > 192.168.1.113.48500: Flags [FP.], cksum 0x9fad (correct), seq 2471424514:2471424593, ack 4044867929, win 118, options [nop,nop,TS val 2128056640 ecr 2710871214], length 79
11:50:22.475835 In 20:b0:01:9f:7b:40 ethertype IPv4 (0x0800), length 147: (tos 0x0, ttl 60, id 17190, offset 0, flags [DF], proto TCP (6), length 131)
149.112.112.9.443 > 192.168.1.113.48500: Flags [FP.], cksum 0x9fad (correct), seq 0:79, ack 1, win 118, options [nop,nop,TS val 2128056640 ecr 2710871214], length 79
11:50:22.823492 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 76: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42225, offset 0, flags [none], proto UDP (17), length 56)
192.168.0.191.56639 > 192.168.0.1.53: 19838+ A? github.com. (28)
11:50:22.823503 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 128, id 42225, offset 0, flags [none], proto UDP (17), length 56)
192.168.0.191.56639 > 192.168.0.1.53: 19838+ A? github.com. (28)
11:50:22.823893 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 48562, offset 0, flags [DF], proto UDP (17), length 56)
192.168.10.2.57075 > 192.168.10.3.53: 65405+ A? github.com. (28)
11:50:22.823911 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 48562, offset 0, flags [DF], proto UDP (17), length 56)
192.168.10.2.57075 > 192.168.10.3.53: 65405+ A? github.com. (28)
11:50:22.824411 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 30209, offset 0, flags [DF], proto UDP (17), length 56)
172.18.0.2.36327 > 192.168.0.1.5053: UDP, length 28
11:50:22.824444 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 30209, offset 0, flags [DF], proto UDP (17), length 56)
172.18.0.2.36327 > 192.168.0.1.5053: UDP, length 28
11:50:22.824620 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 30210, offset 0, flags [DF], proto UDP (17), length 56)
172.18.0.2.36327 > 192.168.0.1.5054: UDP, length 28
11:50:22.824633 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 72: (tos 0x0, ttl 64, id 30210, offset 0, flags [DF], proto UDP (17), length 56)
172.18.0.2.36327 > 192.168.0.1.5054: UDP, length 28
11:50:23.519875 In 20:b0:01:9f:7b:40 ethertype 802.1Q (0x8100), length 151: vlan 2, p 0, ethertype IPv4, (tos 0x0, ttl 60, id 15772, offset 0, flags [DF], proto TCP (6), length 131)
149.112.112.9.443 > 192.168.1.113.48496: Flags [FP.], cksum 0xd93e (correct), seq 2423391319:2423391398, ack 2448545630, win 118, options [nop,nop,TS val 2125185216 ecr 2710874549], length 79
11:50:23.519886 In 20:b0:01:9f:7b:40 ethertype IPv4 (0x0800), length 147: (tos 0x0, ttl 60, id 15772, offset 0, flags [DF], proto TCP (6), length 131)
149.112.112.9.443 > 192.168.1.113.48496: Flags [FP.], cksum 0xd93e (correct), seq 0:79, ack 1, win 118, options [nop,nop,TS val 2125185216 ecr 2710874549], length 79
11:50:23.939095 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 83: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42236, offset 0, flags [none], proto UDP (17), length 63)
192.168.0.191.61248 > 192.168.0.1.53: 21425+ A? sync-v2.brave.com. (35)
11:50:23.939103 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 128, id 42236, offset 0, flags [none], proto UDP (17), length 63)
192.168.0.191.61248 > 192.168.0.1.53: 21425+ A? sync-v2.brave.com. (35)
11:50:23.939487 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 48827, offset 0, flags [DF], proto UDP (17), length 63)
192.168.10.2.35762 > 192.168.10.3.53: 43061+ A? sync-v2.brave.com. (35)
11:50:23.939504 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 48827, offset 0, flags [DF], proto UDP (17), length 63)
192.168.10.2.35762 > 192.168.10.3.53: 43061+ A? sync-v2.brave.com. (35)
11:50:23.940027 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 30272, offset 0, flags [DF], proto UDP (17), length 63)
172.18.0.2.55563 > 192.168.0.1.5053: UDP, length 35
11:50:23.940058 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 30272, offset 0, flags [DF], proto UDP (17), length 63)
172.18.0.2.55563 > 192.168.0.1.5053: UDP, length 35
11:50:23.940256 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 30273, offset 0, flags [DF], proto UDP (17), length 63)
172.18.0.2.55563 > 192.168.0.1.5054: UDP, length 35
11:50:23.940270 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 79: (tos 0x0, ttl 64, id 30273, offset 0, flags [DF], proto UDP (17), length 63)
172.18.0.2.55563 > 192.168.0.1.5054: UDP, length 35
11:50:24.111621 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 111: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42238, offset 0, flags [none], proto UDP (17), length 91)
192.168.0.191.59290 > 192.168.0.1.53: 15679+ A? REDACTED.blob.core.windows.net. (63)
11:50:24.111629 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 128, id 42238, offset 0, flags [none], proto UDP (17), length 91)
192.168.0.191.59290 > 192.168.0.1.53: 15679+ A? REDACTED.blob.core.windows.net. (63)
11:50:24.111988 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 48854, offset 0, flags [DF], proto UDP (17), length 91)
192.168.10.2.40115 > 192.168.10.3.53: 44573+ A? REDACTED.blob.core.windows.net. (63)
11:50:24.112005 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 48854, offset 0, flags [DF], proto UDP (17), length 91)
192.168.10.2.40115 > 192.168.10.3.53: 44573+ A? REDACTED.blob.core.windows.net. (63)
11:50:24.112458 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 30297, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5053: UDP, length 63
11:50:24.112488 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 30297, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5053: UDP, length 63
11:50:24.112639 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 30298, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5054: UDP, length 63
11:50:24.112661 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 30298, offset 0, flags [DF], proto UDP (17), length 91)
172.18.0.2.57913 > 192.168.0.1.5054: UDP, length 63
11:50:24.189641 In 18:c0:4d:af:54:4d ethertype 802.1Q (0x8100), length 80: vlan 1, p 0, ethertype IPv4, (tos 0x0, ttl 128, id 42239, offset 0, flags [none], proto UDP (17), length 60)
192.168.0.191.63769 > 192.168.0.1.53: 971+ A? www.hsbc.co.uk. (32)
11:50:24.189651 In 18:c0:4d:af:54:4d ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 128, id 42239, offset 0, flags [none], proto UDP (17), length 60)
192.168.0.191.63769 > 192.168.0.1.53: 971+ A? www.hsbc.co.uk. (32)
11:50:24.190038 Out 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 48863, offset 0, flags [DF], proto UDP (17), length 60)
192.168.10.2.45038 > 192.168.10.3.53: 53357+ A? www.hsbc.co.uk. (32)
11:50:24.190057 P 4a:58:64:8a:09:3e ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 48863, offset 0, flags [DF], proto UDP (17), length 60)
192.168.10.2.45038 > 192.168.10.3.53: 53357+ A? www.hsbc.co.uk. (32)
11:50:24.190598 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 30305, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5053: UDP, length 32
11:50:24.190627 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 30305, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5053: UDP, length 32
11:50:24.190788 P 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 30306, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5054: UDP, length 32
11:50:24.190799 In 02:42:ac:12:00:02 ethertype IPv4 (0x0800), length 76: (tos 0x0, ttl 64, id 30306, offset 0, flags [DF], proto UDP (17), length 60)
172.18.0.2.50046 > 192.168.0.1.5054: UDP, length 32
....
^C
246 packets captured
265 packets received by filter
3 packets dropped by kernel