thanks for the heads up, will follow this on the github issue here and the mailing list where this patch is mentioned here
Thanks for the info.
Should it work as well on 1900acs?
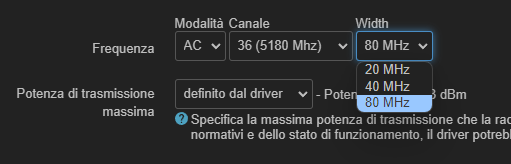
I'm in Italy and trying this, but 160 isn't showing up in the luci options even if FR and Force 40Mhz is configured
@komodikkio
80MHz should work, but only on some channels.
Force 40MHz only applies to 2.4GHz as the 1-11 channel can only have one non-overlapping 40MHz access point at any given time.
Ooh right, thanks for the clarification Skewed, so i can remove the "force 40 mhz" flag from the 5g configuration, right?
I was trying to understand if the 160mhz procedure was doable on the 1900acs, cause i can't see the option at all
160MHz doesn't work on 1200/1900ac series iirc, only wrt32x/3200
but dfs is broken on these, which makes it immediately drop back
got it, thanks ![]()
![]()
so should i install back the packages kmod-mwifiex-sdio kmod-btmrvl mwifiex-sdio-firmware?
@komodikkio
I don't think those packages do anything on wrt1200/1900 series, I just didn't split them out of the config
It appears MAC spoofing for WAN no longer works.
Ughh I discovered that Divested distro comes with an auto-updating script that block a bunch of random domains at the dnsmasq level. One of which for some reason happened to be my externally visible duckdns.org URL pointing to my HomeAssistant instance.
It was kinda fun chasing this down all the way into dnsmasq source to understand what those cryptic "config" dnsmasq log entries meant and then as I almost have up and was typing up pleas for help in OpenWrt forum I completely randomly stumbled into the config file under /tmp/dnsmasq.d/divblock.conf
Bruhh ![]()
I appreciate the effort for sure but can the maintainer please please please call out this functionality somewhere up on the landing page? -> https://divested.dev/unofficial-openwrt-builds/mvebu-linksys/
I bet this will save a lot of pulled out hair for other folks.
Still big thanks for keeping the lights on for my trusty router.
@Giorgik
I've amended the original post and the website: https://divested.dev/unofficial-openwrt-builds/mvebu-linksys/#divblock
duckdns.org isn't even blocked?
Thanks, that was fast.
duckdns.org isn't even blocked?
root@OpenWrt:/etc/init.d# cat /tmp/dnsmasq.d/divblock.conf | grep \.duckdns\.org | wc -l
145291
yes, many entries of duckdns.org are blocked, but it isn't wildcarded out.
I really should just wildcard it out, as you show it makes up nearly 1/5 of the list.
edit: did
Wait why though? Duckdns is a free DNS provider, anyone is free to make a subdomain with them. What's the logic behind blocking the whole thing? Who compiled this list to begin with, how did my private-use Home Assistant hostname end up in the blocklist?
So many question...
Duckdns is a free DNS provider, anyone is free to make a subdomain with them.
DDNS services are useful, especially for homelab use, but often end up rife with malware abusing them.
If I don't block them, then I'm neglecting my users.
If I don't wildcard it, it takes up too much of the list.
If I do wildcard it, it does impact more users but also probably benefits the wider gamut of them.
Who compiled this list to begin with
It is combined from many dozen sources, focused on ad/tracker and malware blocking.
how did my private-use Home Assistant hostname end up in the blocklist
You can download the lists yourself and see which it landed in: https://gitlab.com/divested/simple_hosts_merger/-/blob/master/blocklists.txt
What's your take on blocking the .zip TLD entirely?
Unfortunately I've got the blocklists disabled and a Pi-hole configured as the DNS for a few of the devices in my network instead. My partner works from home in marketing and having hubspot.com blocked is a bit of an issue.
For anyone who reads this and wonders how I did it this is the way:
In etc/config/dhcp:
Set a static lease for the pi-hole with a fixed IP based on its mac address:
config host
option name 'Pi-hole'
option dns '1'
option mac '{MAC_ADDR}'
option ip '192.168.1.{X}'
Create tags that you can apply that set the DNS for the tagged devices to use the Pi-hole
config tag 'pihole'
list dhcp_option '6,192.168.1.{X}'
config tag 'smarthome'
list dhcp_option '6,192.168.1.{X}'
Tag the relevant devices:
config host
option name 'Vizio'
option dns '1'
option mac '{DEVICE_MAC_ADDR}'
option tag 'pihole'
Any suggestions for improvement would be greatly appreciated.
I am unlikely to do that.
Yes, I understand this list can be an issue for those in marketing, but it can be excluded or disabled entirely: https://divested.dev/unofficial-openwrt-builds/mvebu-linksys/#divblock
This is actually a super neat trick, thank you for sharing it.
https://divested.dev/unofficial-openwrt-builds/mvebu-linksys/20230601-00/
- update to edb3a4162c0763ecc9d5e7660700a68a25bf28e3
- [upstream] update to kernel 5.15.114
- openssl: fix moderate-severity CVE-2023-2650
https://www.openssl.org/news/secadv/20230530.txt
just installed this build. rebooting seems to be slower than usual (maybe it's just me though)
Your builds have been great thanks, had a 50-day uptime on the previous build I installed and just moved up to the new one on my WRT32X. It's so good no real reason to update other than for fun. Going to put 23.05-rc1 on the other partition once that hits in a few days to mess with it (although little has changed from master at this point.)