It means that there are potential security risks. What specific known vulnerabilities exist in that version, I cannot say (it would require some work to compile the list, looking at everything that has been patched in the ensuing versions of 19.07 and now up to 21.02.2).
If the router itself is not connected to the internet at all, there is a much lower chance of an issue -- but there may be some wifi related vulnerabilities which means people could potentially hack your router if they are within wifi range. If wifi is disabled, there is an even smaller attack surface -- someone would require physical access to the router or the network to attack it. And if that's the case, you may have bigger issues.
Only DDWRT releases newer versions for this router. Actually, I still don't quite understand what exactly I should disable on the 1.2 network to only have the web interface available. I'll copy and paste a picture in a minute.
That's because it is ~13 years old -- that is ancient in the world of computers and network technology, especially true if it is a lower end/inexpensive bit of kit.
DDWRT does do a great job of supporting devices that have extremely limited resources, but they assemble a monolithic firmware that is not as flexible in terms of additional packages and such. Just a different paradigm.
I would have to somehow move the camera and the NAS server to the 1.2 network and then disable the connection so that no device can connect to the network. The admin interface of the NAS and camera should be accessible from the 1.1 network, everything else should be disabled.
Or is it already very complicated?
Let's see your complete config:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/dhcp
cat /etc/config/firewall
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xe9a:0930:vd97::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0t'
config interface 'CCTV'
option proto 'static'
option ifname 'eth0'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'CCTV'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'CCTV'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
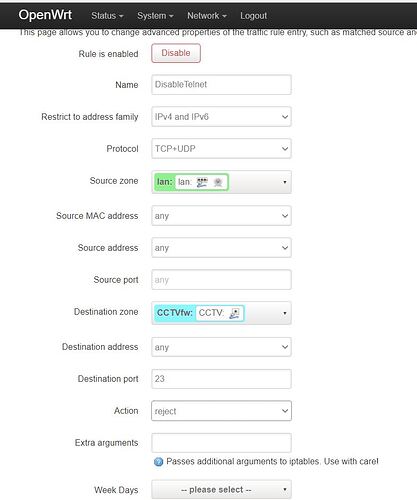
option src 'lan'
option name 'DisableSSH'
option dest_port '23'
option target 'REJECT'
option src_mac '00:62:6E:FE:5A:82'
option src_ip '192.168.1.106'
option dest 'wan'
option dest_ip '192.168.1.106'
config rule
option enabled '1'
option target 'ACCEPT'
option src 'wan'
option dest 'lan'
option name 'DisableTelnet'
config zone
option input 'ACCEPT'
option forward 'REJECT'
option output 'ACCEPT'
option name 'CCTVfw'
option network 'CCTV'
It appears you have configured your physical WAN port with this new network. Is that your desired situation (it is fine to repurpose that port -- the port can be used for anything).
The way things are now configured assumes that you do not have this device connected to the internet at all, is that correct?
If you plug a computer into that port, do you get an IP in the correct range (192.168.2.0/24)?
Yes, the router is not connected to the Internet. But if I want to connect it, I do it as a wifi client. If I plug a cord into the router port, it defaults to the 192.168.1.1 network.
Is this true for all 5 physical ports?
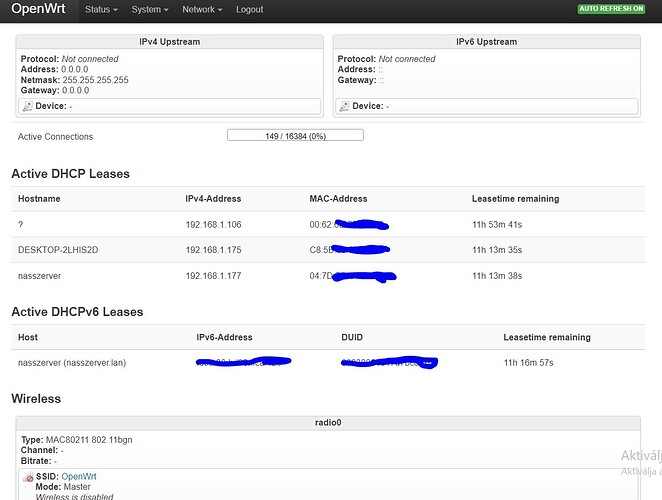
Yes. Both the camera and the NAS get their IP address from the 192.168.1.1 network.
(I tried to upload a picture, but the system would not upload it.)
You've tried all 5 physical ports, and all of them assign a DHCP issued address in the 192.168.1.0/24 network? In theory, one of the ports should issue an address in 192.168.2.0/24.
If that's not happening, reset your router to defaults and then post your config files again... this way we can use the original config to inform the changes.
There are 4 ports in total, yes, all 4 ports are in the 192.168.1.1 range. Is it possible that the physical interface I assigned to the virtual interface is not correct?
Instead of looking at the OpenWrt status page, the best way to determine what is happening with DHCP assignments is to look at the network configuration of the connected computer (as you connect it to each of the physical ports). One of 3 things will happen:
- address in 192.168.1.0/24
- address in 192.168.2.0/24
- no IP address issued at all.
So, should I now reset the device and resend the configuration files?
Sure. Makes sense to do this now.
I send you the reseted info:
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xce6:27i8b:5eu7::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0t'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
# Uncomment this line to disable ipv6 rules
# option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
# We need to accept udp packets on port 68,
# see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
# Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# Allow DHCPv6 replies
# see https://dev.openwrt.org/ticket/10381
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
# Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
# Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
# include a file with users custom iptables rules
config include
option path /etc/firewall.user
### EXAMPLE CONFIG SECTIONS
# do not allow a specific ip to access wan
#config rule
# option src lan
# option src_ip 192.168.45.2
# option dest wan
# option proto tcp
# option target REJECT
# block a specific mac on wan
#config rule
# option dest wan
# option src_mac 00:11:22:33:44:66
# option target REJECT
# block incoming ICMP traffic on a zone
#config rule
# option src lan
# option proto ICMP
# option target DROP
# port redirect port coming in on wan to lan
#config redirect
# option src wan
# option src_dport 80
# option dest lan
# option dest_ip 192.168.16.235
# option dest_port 80
# option proto tcp
# port redirect of remapped ssh port (22001) on wan
#config redirect
# option src wan
# option src_dport 22001
# option dest lan
# option dest_port 22
# option proto tcp
### FULL CONFIG SECTIONS
#config rule
# option src lan
# option src_ip 192.168.45.2
# option src_mac 00:11:22:33:44:55
# option src_port 80
# option dest wan
# option dest_ip 194.25.2.129
# option dest_port 120
# option proto tcp
# option target REJECT
#config redirect
# option src lan
# option src_ip 192.168.45.2
# option src_mac 00:11:22:33:44:55
# option src_port 1024
# option src_dport 80
# option dest_ip 194.25.2.129
# option dest_port 120
# option proto tcp
These are the default settings for the system.
With this solution, the 192.168.1.1 network will not be accessible from the 192.168.1.2 network, because it would require a physical connection to that port?
When we're done, you will have 2 networks: 192.168.1.0/24 and 192.168.2.0/24. They will be isolated by firewall rules.
We'll modify the following bits to look like this:
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 0t'
config interface 'camera'
option ifname 'eth0.2'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
Then in the dhcp file, add the following
config dhcp 'camera'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
and finally in the firewall file:
config zone
option name camera
list network 'camera'
option input ACCEPT
option output ACCEPT
option forward REJECT
config forwarding
option src lan
option dest camera
This won't yet prohibit the camera's telnet or anything else, but it will set them up on 2 different networks. We want to test that everything works here before we add any restrictions.
I don't know what the logical-to-physical port mapping is for your device. It will likely be that either physical port 1 or port 4 corresponds to the new network... connecting a computer to each of the LAN ports should confirm that 3 of them will use the 192.168.1.0/24, and one will use 192.168.2.0/24.
1 Like