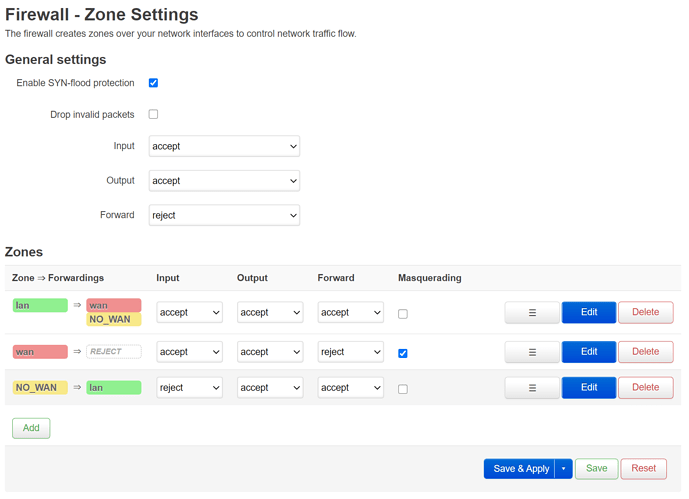
I've done a search, but most people have the opposite issue: a VLAN that can't get WAN access.VLAN100 (NO_WAN) can't reach WAN.VLAN100 is for my future IP cams.
This is my setup:
I let the NO_WAN zone forward only to LAN, not WAN.VLAN100 is part of NO_WAN only.VLAN100 can ping Google when you give it its IP address (DNS is blocked).
What am I missing here?NO_WAN to LAN and from there to WAN?
(Please ignore the input accept rule on WAN, I'm currently accessing this router from a higher level network)
I thought everything was blocked...?
What IP? Google controls millions
Can we see the /etc/config/network and /etc/config/firewall?
Nikotine:
What am I missing here?
Your configs.
lleachii:
I thought everything was blocked...?
Yes, I thought the same, based on the firewall rules.
172.217.17.142 = google.com .
lleachii:
Nikotine:
What am I missing here?
Your configs.
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd00:ab:cd::/48'
config interface 'lan'
option ifname 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.25.1.1'
config interface 'vlan9'
option ifname 'eth1.9'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.25.9.1'
config interface 'vlan100'
option ifname 'eth1.100'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.25.100.1'
config interface 'wan'
option ifname 'eth0'
option proto 'dhcp'
list dns '1.1.1.1'
list dns '1.0.0.1'
option peerdns '0'
config interface 'wan6'
option ifname 'eth0'
option proto 'dhcpv6'
list dns '2606:4700:4700::1111'
list dns '2606:4700:4700::1001'
option reqprefix 'auto'
option reqaddress 'try'
option peerdns '0'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan vlan9'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config redirect 'adblock_dns_53'
option name 'Adblock DNS, port 53'
option src 'lan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_dns_853'
option name 'Adblock DNS, port 853'
option src 'lan'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_dns_5353'
option name 'Adblock DNS, port 5353'
option src 'lan'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config zone
option network 'vlan100'
option output 'ACCEPT'
option name 'NO_WAN'
option input 'REJECT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'NO_WAN'
config forwarding
option dest 'lan'
option src 'NO_WAN'
config rule
option src_port '67-68'
option src 'NO_WAN'
option name 'Allow DHCP request'
option target 'ACCEPT'
option dest_port '67-68'
list proto 'udp'
config rule
option dest_port '53'
option src 'NO_WAN'
option name 'Allow DNS queries'
option target 'ACCEPT'
config rule
option dest_port '22'
option src 'wan'
option name 'Allow SSH from WAN'
option target 'ACCEPT'
option src_port '22'
The client:
pi@rpi4-servemepi:~ $ ifconfig
docker0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
inet6 fe80::42:cbff:fe7b:b75a prefixlen 64 scopeid 0x20<link>
ether 02:42:cb:7b:b7:5a txqueuelen 0 (Ethernet)
RX packets 56 bytes 51669 (50.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 38631 bytes 4225279 (4.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.25.100.129 netmask 255.255.255.0 broadcast 10.25.100.255
inet6 fe80::bc5c:a8bc:b1cc:49d9 prefixlen 64 scopeid 0x20<link>
ether dc:a6:32:b1:55:93 txqueuelen 1000 (Ethernet)
RX packets 241010 bytes 265308979 (253.0 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 164001 bytes 12521056 (11.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 37457 bytes 3526065 (3.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 37457 bytes 3526065 (3.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
vethdd632b5: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 169.254.181.178 netmask 255.255.0.0 broadcast 169.254.255.255
inet6 fe80::9eda:ad9e:b1a5:27a9 prefixlen 64 scopeid 0x20<link>
ether 0a:5f:35:f6:bf:76 txqueuelen 0 (Ethernet)
RX packets 52 bytes 51549 (50.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 102165 bytes 16906107 (16.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
pi@rpi4-servemepi:~ $ traceroute -i eth0 google.com
traceroute to google.com (172.217.17.46), 30 hops max, 60 byte packets
1 10.25.100.2 (10.25.100.2) 1.074 ms 1.558 ms 2.118 ms
2 FriendlyWrt.lan (10.25.100.1) 0.614 ms 0.490 ms 0.827 ms
3 192.168.1.1 (192.168.1.1) 2.076 ms 3.940 ms 1.789 ms
4 192.168.0.1 (192.168.0.1) 4.673 ms 3.621 ms 5.529 ms
5 <redacted> 27.737 ms 27.645 ms 27.377 ms
6 * * *
7 <redacted> 26.234 ms 26.567 ms 26.462 ms
8 <redacted> 41.595 ms 37.852 ms 37.680 ms
9 * * *
10 108.170.241.161 (108.170.241.161) 36.999 ms 209.85.240.30 (209.85.240.30) 21.736 ms 108.170.241.161 (108.170.241.161) 30.049 ms
11 ams16s29-in-f46.1e100.net (172.217.17.46) 31.088 ms 108.170.241.172 (108.170.241.172) 28.968 ms 108.170.236.135 (108.170.236.135) 28.435 ms
pi@rpi4-servemepi:~ $ route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.25.100.2 0.0.0.0 UG 202 0 0 eth0
10.25.100.0 0.0.0.0 255.255.255.0 U 202 0 0 eth0
169.254.0.0 0.0.0.0 255.255.0.0 U 206 0 0 vethdd632b5
172.17.0.0 0.0.0.0 255.255.0.0 U 0 0 0 docker0
pi@rpi4-servemepi:~ $
Whoa!!!
What is this router at 10.25.100.2 - and is it allowed to access the Internet?
This doesn't appear to be the OpenWrt device. Also, this is operational because you ALLOW FORWARD [to/from other routers] within the NO_WAN zone .
Sorry, I didn't think all this was relevant, but this is a Nanopi R4S running FriendlyWRT (a fork of OpenWRT). It has two ports, one is for WAN (192.168.1.116), the other goes to a tagged port of a managed L3 switch (Brocade ICX 6450).
The client 10.25.100.129 is connected to this switch. This switch has the same VLANs (9 and 100) and has virtual router interfaces to route within the VLAN. For VLAN100 this is 10.25.100.2.
192.168.1.1 = main OpenWRT router
I'm confused...or maybe you can just clarify...maybe you don't understand there are 2 firewalls/routers in VLAN 100, this is not common:
Why do you have two routers in VLAN 100?
Which router are you entering the configs?
Is any firewall/router actually running OpenWrt???
Who is 10.25.100.1 then???
1 ; but your first router in traceroute is 10.25.100.2 .
2 as its gateway (i.e. router), shouldn't it be 10.25.100.1 ?
How is your client getting .2 as its gateway?
ISP -> (WAN 192.168.0.1) main OpenWRT home network 192.168.1.1/24 -> (192.168.1.116) Nanopi r4s VLAN100 interface 10.25.100.1/24 -> L3 switch VLAN100 virtual router interface 10.25.100.2 -> client 10.25.100.129
The goal is to replace my current OpenWRT router with the Nanopi, once it works as intended.
This is the setup of the switch:
ICX6450-48P-Router>show run
Current configuration:
!
ver 08.0.30tT313
!
stack unit 1
module 1 icx6450-48p-poe-port-management-module
module 2 icx6450-sfp-plus-4port-40g-module
!
global-stp
!
!
!
vlan 9 name main by port
tagged ethe 1/1/1
untagged ethe 1/1/2 to 1/1/36
router-interface ve 9
!
vlan 100 name IPcams by port
tagged ethe 1/1/1
untagged ethe 1/1/37 to 1/1/48
router-interface ve 100
!
vlan 4095 name DEFAULT-VLAN by port
router-interface ve 4095
!
!
!
!
!
aaa authentication web-server default local
aaa authentication enable default local
aaa authentication login default local
default-vlan-id 4095
enable telnet authentication
hostname ICX6450-48P-Router
ip dhcp-client disable
ip dns server-address 10.25.1.1
ip route 0.0.0.0/0 10.25.1.1
!
mirror-port ethernet 1/1/1
!
no telnet server
username root password .....
snmp-server community ..... ro
!
!
clock summer-time
clock timezone gmt GMT+01
!
!
ntp
disable serve
server 10.25.1.1
!
!
web-management https
web-management refresh front-panel 30
web-management session-timeout 3600
!
!
!
interface ethernet 1/1/1
dual-mode
!
interface ethernet 1/1/2
mon ethe 1/1/1 both
!
interface ve 9
ip address 10.25.9.2 255.255.255.0
!
interface ve 100
ip address 10.25.100.2 255.255.255.0
!
interface ve 4095
ip address 10.25.1.2 255.255.255.0
!
!
!
!
!
!
!
!
!
end
ICX6450-48P-Router>
Nikotine:
traceroute to google.com (172.217.17.46), 30 hops max, 60 byte packets
1 10.25.100.2 (10.25.100.2) 1.074 ms 1.558 ms 2.118 ms
2 FriendlyWrt.lan (10.25.100.1) 0.614 ms 0.490 ms 0.827 ms
3 192.168.1.1 (192.168.1.1) 2.076 ms 3.940 ms 1.789 ms
4 192.168.0.1 (192.168.0.1) 4.673 ms 3.621 ms 5.529 ms
Can you clarify what's actually seen and not what you desire?
Do you realize what you're saying is not what you're showing?
If so, can you explain why what you show does not match what you're saying?
I'm completely confused now. If your issue is not OpenWrt related, you should inquire with the OEM of that software. And, you've still failed to explain why there's 2 routers. I surmise your issue is that 10.25.100.2 is routing it; and you ALLOW FORWARD on 10.25.100.1 .
BTW, welcome to the community, @Nikotine !
1 Like
One is on the Nanopi, the other is on the switch.
The Nanopi
The Nanopi runs FriendlyWRT: https://github.com/friendlyarm/friendlywrt
lleachii:
Who is 10.25.100.1 then
VLAN100 interface on the Nanopi: 10.25.100.1/24
Via option 3 in the DHCP settings.
Nikotine:
One is on the Nanopi, the other is on the switch.
Are you actually looking at your traceroute???
I see no switch, I see two routers ...and you intend for your devices to get 10.25.100.2 as their gateway!!!
...but you showed us configs on 10.25.100.1 ???.2 is not OpenWrt?
OK, I think I'm done, again:
Simply REJECT or DROP FORWARD in zone NO_WAN...since you seem unclear as to why you configured 2 routers in VLAN 100 and call one a switch.
EDIT:
Are you trying to say that you DO NOT want the OpenWrt 10.25.100.1 (the SECOND hop) to be a router - you want it gone ?
Why aren't you blocking on 10.25.100.2 (which is not OpenWrt related it seems)?
1 Like
Dear Ileachii,
The switch (Brocade ICX 6450) has been flashed with router firmware as per these instructions: https://fohdeesha.com/docs/icx64xx/
The switch (with router firmware) can't do NAT, so one tagged port goes to the Nanopi, which acts as the router to WAN.
I realize that inter-vlan firewall rules on the Nanopi won't have an effect because the switch itself is routing.
I don't see how turning a Layer 2 device into a Layer 3 on gets more speed...but this seems unrelated to OpenWrt too....unless this is .1 ?
OK, but is this your intention???
WHAT INSTRUCTIONS???
Then inquire there.
Also, you're just saying "switch", "Brocade" "Nanopi"...but you've yet to once identify OpenWrt, I guess it's .1 .
You do know this is an OpenWrt support-only forum, correct?
1 Like
Thanks I will try that.
10.25.100.1 should route (or block in case of this VLAN) to WAN.
To be honest, because the switch works with ACL which I haven't figured out yet.
You're going in circles...you haven't explained WHY you're routing twice. This is uncessary and I think you are misunderstanding firewall rules...but I donno where the OpenWrt devices (i.e. the only one supported here) is located, if you want it to route, etc.
Again, you actually fail to identify what/where is the OpenWrt.
And you do realize your clients get .2 as their gateway, not .1 - yet it seems you're firewalling on .1 ?
You do understand that error, correct?
Yes, if you DROP or REJECT FORWARD (on 10.25.100.1, if it's the OpenWrt), since it seems you're forwarding from 10.25.100.2 - which you ALLOW !
1 Like
Say, a NAS and an IP cam are connected to a switch.
Yes, see above.
lleachii:
WHAT INSTRUCTIONS???
Sorry, forgot to paste the link: https://fohdeesha.com/docs/icx64xx/
lleachii:
Then inquire there.
FriendlyWRT IS Openwrt.
But ok, it sounds like you won't accept that.
It ends here then.
lleachii:
Also, you're just saying "switch", "Brocade" "Nanopi"...but you've yet to once identify OpenWrt, I guess it's .1 .
Already stated above, but the switch is a Brocade ICX 6450. The Nanopi runs Friendlywrt = Openwrt.
I also posted /etc/config/network some posts ago.
EDIT: ok, while typing this I see you changed your post again
Nikotine:
FriendlyWRT IS Openwrt.
See: https://downloads.openwrt.org/ for official and current firmware.
Now I understand the confusion, you kept mixing FriendlyWRT and OpenWrt. Nonetheless, the settings I noted work for OpenWrt - so if you say they're the same, you're good to go.
I thought another device was running FriendlyWRT and one OpenWrt - since this support is only for official software, I never guessed you were continuing about unsupported software, my apologies.
I'll be honest, it's hard to follow having 2 routers in the same VLAN/sunbet (especially for a reason that doesn't follow actual computing, e.g. less CPUs yet you're still routing on the device you wanted to save them from)...I actually want to test to be sure.
You can:
Stop routing on the napo
Make the OpenWrt a real switch (i.e. don't forward traffic from the napo to the .1 )
1 Like
Yes thanks.
Unfortunately the Nanopi isn't supported yet, but the Nanopi developers have ported it to the Nanopi and (frustratingly) called it Friendlywrt.
lleachii:
Yes, if you DROP or REJECT FORWARD (on 10.25.100.1, if it's the OpenWrt), since it seems you're forwarding from 10.25.100.2 - which you ALLOW !
So, one more question unfortunately.
trendy
April 6, 2021, 3:42pm
19
Can you post iptables-save -c from the FriendlyWRT?
1 Like
Hi Trendy:
root@FriendlyWrt:~# iptables-save -c
# Generated by iptables-save v1.8.3 on Wed Apr 7 00:14:59 2021
*nat
:PREROUTING ACCEPT [83819:11035425]
:INPUT ACCEPT [16078:1191306]
:OUTPUT ACCEPT [3130:470017]
:POSTROUTING ACCEPT [2645:411767]
:postrouting_NO_WAN_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_NO_WAN_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_NO_WAN_postrouting - [0:0]
:zone_NO_WAN_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[83849:11037652] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[20182:1213190] -A PREROUTING -i eth1 -m comment --comment "!fw3" -j zone_lan_prerouting
[6:1025] -A PREROUTING -i eth1.9 -m comment --comment "!fw3" -j zone_lan_prerouting
[63635:9820932] -A PREROUTING -i eth0 -m comment --comment "!fw3" -j zone_wan_prerouting
[26:2505] -A PREROUTING -i eth1.100 -m comment --comment "!fw3" -j zone_NO_WAN_prerouting
[23197:1674565] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[652:102168] -A POSTROUTING -o eth1 -m comment --comment "!fw3" -j zone_lan_postrouting
[654:102544] -A POSTROUTING -o eth1.9 -m comment --comment "!fw3" -j zone_lan_postrouting
[20552:1262798] -A POSTROUTING -o eth0 -m comment --comment "!fw3" -j zone_wan_postrouting
[654:102544] -A POSTROUTING -o eth1.100 -m comment --comment "!fw3" -j zone_NO_WAN_postrouting
[654:102544] -A zone_NO_WAN_postrouting -m comment --comment "!fw3: Custom NO_WAN postrouting rule chain" -j postrouting_NO_WAN_rule
[26:2505] -A zone_NO_WAN_prerouting -m comment --comment "!fw3: Custom NO_WAN prerouting rule chain" -j prerouting_NO_WAN_rule
[1306:204712] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[20188:1214215] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Adblock DNS, port 53" -j REDIRECT --to-ports 53
[30:2227] -A zone_lan_prerouting -p udp -m udp --dport 53 -m comment --comment "!fw3: Adblock DNS, port 53" -j REDIRECT --to-ports 53
[0:0] -A zone_lan_prerouting -p tcp -m tcp --dport 853 -m comment --comment "!fw3: Adblock DNS, port 853" -j REDIRECT --to-ports 853
[0:0] -A zone_lan_prerouting -p udp -m udp --dport 853 -m comment --comment "!fw3: Adblock DNS, port 853" -j REDIRECT --to-ports 853
[0:0] -A zone_lan_prerouting -p tcp -m tcp --dport 5353 -m comment --comment "!fw3: Adblock DNS, port 5353" -j REDIRECT --to-ports 5353
[0:0] -A zone_lan_prerouting -p udp -m udp --dport 5353 -m comment --comment "!fw3: Adblock DNS, port 5353" -j REDIRECT --to-ports 5353
[20552:1262798] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[20552:1262798] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[63635:9820932] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Wed Apr 7 00:14:59 2021
# Generated by iptables-save v1.8.3 on Wed Apr 7 00:14:59 2021
*raw
:PREROUTING ACCEPT [473382:318895662]
:OUTPUT ACCEPT [9599:2172730]
:zone_NO_WAN_helper - [0:0]
:zone_lan_helper - [0:0]
[216918:24982471] -A PREROUTING -i eth1 -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
[1571:182037] -A PREROUTING -i eth1.9 -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
[1591:182867] -A PREROUTING -i eth1.100 -m comment --comment "!fw3: NO_WAN CT helper assignment" -j zone_NO_WAN_helper
[0:0] -A zone_NO_WAN_helper -p udp -m comment --comment "!fw3: Amanda backup and archiving proto" -m udp --dport 10080 -j CT --helper amanda
[0:0] -A zone_NO_WAN_helper -p tcp -m comment --comment "!fw3: FTP passive connection tracking" -m tcp --dport 21 -j CT --helper ftp
[0:0] -A zone_NO_WAN_helper -p udp -m comment --comment "!fw3: RAS proto tracking" -m udp --dport 1719 -j CT --helper RAS
[0:0] -A zone_NO_WAN_helper -p tcp -m comment --comment "!fw3: Q.931 proto tracking" -m tcp --dport 1720 -j CT --helper Q.931
[0:0] -A zone_NO_WAN_helper -p tcp -m comment --comment "!fw3: IRC DCC connection tracking" -m tcp --dport 6667 -j CT --helper irc
[0:0] -A zone_NO_WAN_helper -p tcp -m comment --comment "!fw3: PPTP VPN connection tracking" -m tcp --dport 1723 -j CT --helper pptp
[0:0] -A zone_NO_WAN_helper -p tcp -m comment --comment "!fw3: SIP VoIP connection tracking" -m tcp --dport 5060 -j CT --helper sip
[0:0] -A zone_NO_WAN_helper -p udp -m comment --comment "!fw3: SIP VoIP connection tracking" -m udp --dport 5060 -j CT --helper sip
[0:0] -A zone_NO_WAN_helper -p udp -m comment --comment "!fw3: SNMP monitoring connection tracking" -m udp --dport 161 -j CT --helper snmp
[0:0] -A zone_NO_WAN_helper -p udp -m comment --comment "!fw3: TFTP connection tracking" -m udp --dport 69 -j CT --helper tftp
[0:0] -A zone_lan_helper -p udp -m comment --comment "!fw3: Amanda backup and archiving proto" -m udp --dport 10080 -j CT --helper amanda
[0:0] -A zone_lan_helper -p tcp -m comment --comment "!fw3: FTP passive connection tracking" -m tcp --dport 21 -j CT --helper ftp
[0:0] -A zone_lan_helper -p udp -m comment --comment "!fw3: RAS proto tracking" -m udp --dport 1719 -j CT --helper RAS
[0:0] -A zone_lan_helper -p tcp -m comment --comment "!fw3: Q.931 proto tracking" -m tcp --dport 1720 -j CT --helper Q.931
[0:0] -A zone_lan_helper -p tcp -m comment --comment "!fw3: IRC DCC connection tracking" -m tcp --dport 6667 -j CT --helper irc
[0:0] -A zone_lan_helper -p tcp -m comment --comment "!fw3: PPTP VPN connection tracking" -m tcp --dport 1723 -j CT --helper pptp
[0:0] -A zone_lan_helper -p tcp -m comment --comment "!fw3: SIP VoIP connection tracking" -m tcp --dport 5060 -j CT --helper sip
[0:0] -A zone_lan_helper -p udp -m comment --comment "!fw3: SIP VoIP connection tracking" -m udp --dport 5060 -j CT --helper sip
[0:0] -A zone_lan_helper -p udp -m comment --comment "!fw3: SNMP monitoring connection tracking" -m udp --dport 161 -j CT --helper snmp
[0:0] -A zone_lan_helper -p udp -m comment --comment "!fw3: TFTP connection tracking" -m udp --dport 69 -j CT --helper tftp
COMMIT
# Completed on Wed Apr 7 00:14:59 2021
# Generated by iptables-save v1.8.3 on Wed Apr 7 00:14:59 2021
*mangle
:PREROUTING ACCEPT [473383:318895702]
:INPUT ACCEPT [29639:2612279]
:FORWARD ACCEPT [396040:307641625]
:OUTPUT ACCEPT [9600:2174066]
:POSTROUTING ACCEPT [412259:310585529]
[19993:1199580] -A FORWARD -o eth0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[19993:1039748] -A FORWARD -i eth0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Wed Apr 7 00:14:59 2021
# Generated by iptables-save v1.8.3 on Wed Apr 7 00:14:59 2021
*filter
:INPUT ACCEPT [1602:181984]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [1562:179904]
:forwarding_NO_WAN_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_NO_WAN_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_NO_WAN_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_NO_WAN_dest_ACCEPT - [0:0]
:zone_NO_WAN_dest_REJECT - [0:0]
:zone_NO_WAN_forward - [0:0]
:zone_NO_WAN_input - [0:0]
:zone_NO_WAN_output - [0:0]
:zone_NO_WAN_src_REJECT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_ACCEPT - [0:0]
[986:83577] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[28653:2528702] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[1639:214443] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[21:1220] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[1688:189402] -A INPUT -i eth1 -m comment --comment "!fw3" -j zone_lan_input
[1571:182037] -A INPUT -i eth1.9 -m comment --comment "!fw3" -j zone_lan_input
[20602:1580049] -A INPUT -i eth0 -m comment --comment "!fw3" -j zone_wan_input
[1591:182867] -A INPUT -i eth1.100 -m comment --comment "!fw3" -j zone_NO_WAN_input
[396040:307641625] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[375973:306437077] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[20067:1204548] -A FORWARD -i eth1 -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth1.9 -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth0 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i eth1.100 -m comment --comment "!fw3" -j zone_NO_WAN_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[986:83577] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[8614:2090489] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[1797:1306511] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1562:179904] -A OUTPUT -o eth1 -m comment --comment "!fw3" -j zone_lan_output
[1566:180943] -A OUTPUT -o eth1.9 -m comment --comment "!fw3" -j zone_lan_output
[562:62606] -A OUTPUT -o eth0 -m comment --comment "!fw3" -j zone_wan_output
[1565:180621] -A OUTPUT -o eth1.100 -m comment --comment "!fw3" -j zone_NO_WAN_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[1562:179904] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[21:1220] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[1565:180621] -A zone_NO_WAN_dest_ACCEPT -o eth1.100 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_NO_WAN_dest_REJECT -o eth1.100 -m comment --comment "!fw3" -j reject
[0:0] -A zone_NO_WAN_forward -m comment --comment "!fw3: Custom NO_WAN forwarding rule chain" -j forwarding_NO_WAN_rule
[0:0] -A zone_NO_WAN_forward -m comment --comment "!fw3: Zone NO_WAN to lan forwarding policy" -j zone_lan_dest_ACCEPT
[0:0] -A zone_NO_WAN_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_NO_WAN_forward -m comment --comment "!fw3" -j zone_NO_WAN_dest_REJECT
[1591:182867] -A zone_NO_WAN_input -m comment --comment "!fw3: Custom NO_WAN input rule chain" -j input_NO_WAN_rule
[3:988] -A zone_NO_WAN_input -p udp -m udp --sport 67:68 --dport 67:68 -m comment --comment "!fw3: Allow DHCP request" -j ACCEPT
[0:0] -A zone_NO_WAN_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Allow DNS queries" -j ACCEPT
[26:1975] -A zone_NO_WAN_input -p udp -m udp --dport 53 -m comment --comment "!fw3: Allow DNS queries" -j ACCEPT
[0:0] -A zone_NO_WAN_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[1562:179904] -A zone_NO_WAN_input -m comment --comment "!fw3" -j zone_NO_WAN_src_REJECT
[1565:180621] -A zone_NO_WAN_output -m comment --comment "!fw3: Custom NO_WAN output rule chain" -j output_NO_WAN_rule
[1565:180621] -A zone_NO_WAN_output -m comment --comment "!fw3" -j zone_NO_WAN_dest_ACCEPT
[1562:179904] -A zone_NO_WAN_src_REJECT -i eth1.100 -m comment --comment "!fw3" -j reject
[1562:179904] -A zone_lan_dest_ACCEPT -o eth1 -m comment --comment "!fw3" -j ACCEPT
[1566:180943] -A zone_lan_dest_ACCEPT -o eth1.9 -m comment --comment "!fw3" -j ACCEPT
[20067:1204548] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[20067:1204548] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to NO_WAN forwarding policy" -j zone_NO_WAN_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[3259:371439] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[40:2962] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[3219:368477] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[3128:360847] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[3128:360847] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[1648:186440] -A zone_lan_src_ACCEPT -i eth1 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[1571:182037] -A zone_lan_src_ACCEPT -i eth1.9 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[40:1600] -A zone_wan_dest_ACCEPT -o eth0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[20589:1265554] -A zone_wan_dest_ACCEPT -o eth0 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[20602:1580049] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[10:3386] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[752:24064] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -p tcp -m tcp --sport 22 --dport 22 -m comment --comment "!fw3: Allow SSH from WAN" -j ACCEPT
[0:0] -A zone_wan_input -p udp -m udp --sport 22 --dport 22 -m comment --comment "!fw3: Allow SSH from WAN" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[19840:1552599] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_ACCEPT
[562:62606] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[562:62606] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[19800:1550519] -A zone_wan_src_ACCEPT -i eth0 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
COMMIT
# Completed on Wed Apr 7 00:14:59 2021
root@FriendlyWrt:~#